Cloud Misconfiguration Examples
Updated on February 18, 2026, by Xcitium

Did you know that cloud misconfigurations are responsible for the majority of cloud data breaches worldwide? As organizations rapidly migrate to AWS, Azure, and Google Cloud, even a small configuration mistake can expose millions of records.
Cloud platforms are powerful—but they are not secure by default. One incorrect setting, an overly permissive policy, or an exposed storage bucket can become an open door for attackers.
In this comprehensive guide, we’ll break down real-world cloud misconfiguration examples, explain how they happen, and provide practical steps to prevent them. Whether you’re a CISO, IT manager, cloud architect, or security professional, this guide will help you strengthen your cloud security posture.
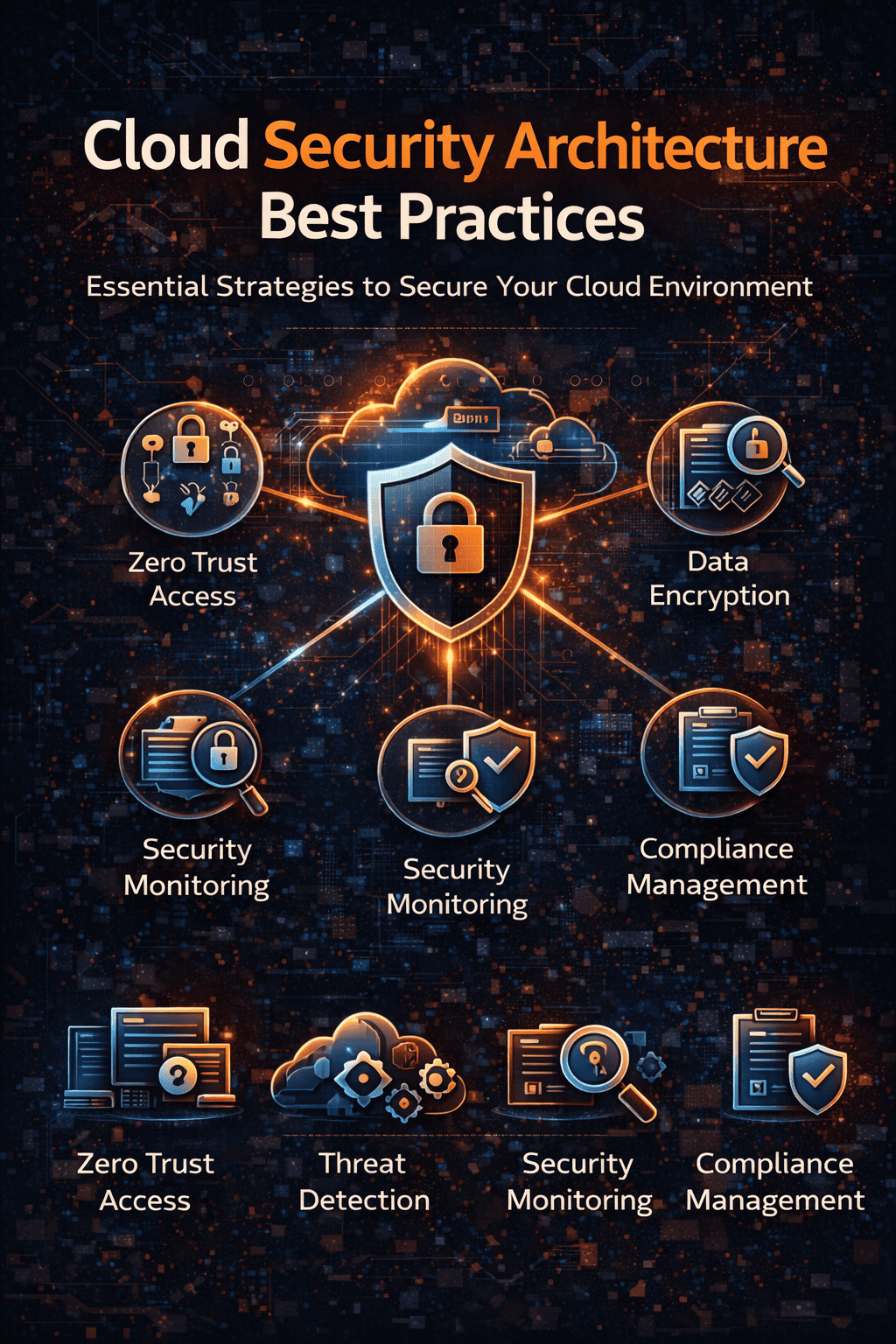
What Is a Cloud Misconfiguration?
A cloud misconfiguration occurs when cloud resources are incorrectly set up, leaving them vulnerable to unauthorized access, data exposure, or cyberattacks.
These errors often stem from:
-
Human error
-
Lack of visibility
-
Overly complex cloud environments
-
Poor identity and access management (IAM)
-
Misunderstanding of shared responsibility models
Unlike traditional infrastructure, cloud environments are dynamic. Resources spin up and down quickly, making it easier for misconfigurations to go unnoticed.
Why Cloud Misconfigurations Are So Dangerous
Cloud misconfigurations can result in:
-
Data breaches
-
Regulatory fines (GDPR, HIPAA, PCI DSS)
-
Account takeovers
-
Ransomware attacks
-
Cryptojacking incidents
-
Reputation damage
Attackers actively scan the internet for exposed cloud assets. They don’t need sophisticated exploits—just one open port or public bucket.
Common Cloud Misconfiguration Examples
Let’s examine the most frequent cloud security misconfigurations across AWS, Azure, and Google Cloud.
1. Publicly Exposed Storage Buckets
One of the most well-known cloud misconfiguration examples is a publicly accessible storage bucket.
How It Happens
-
Amazon S3 bucket set to “public”
-
Azure Blob storage without proper access restrictions
-
Google Cloud Storage bucket with open permissions
-
Lack of bucket policy review
The Risk
Anyone on the internet can access sensitive files such as:
-
Customer records
-
API keys
-
Backup files
-
Internal documents
How to Prevent It
-
Disable public access by default
-
Enable bucket-level logging
-
Apply least privilege IAM policies
-
Use automated cloud security posture management (CSPM) tools
-
Conduct regular permission audits
2. Overly Permissive IAM Policies
Identity and Access Management (IAM) misconfigurations are among the most dangerous security gaps in cloud environments.
Common IAM Mistakes
-
Granting “*” (full wildcard) permissions
-
Assigning admin rights unnecessarily
-
Using shared credentials
-
Failing to rotate access keys
Why This Is Critical
If attackers compromise one account with excessive privileges, they can:
-
Escalate privileges
-
Access sensitive data
-
Modify security settings
-
Deploy malicious workloads
Prevention Best Practices
-
Enforce the principle of least privilege
-
Use role-based access control (RBAC)
-
Enable multi-factor authentication (MFA)
-
Monitor privileged account activity
3. Unrestricted Security Groups and Open Ports
Security groups act as virtual firewalls. Misconfigurations here can expose cloud workloads to the public internet.
Example
-
Port 22 (SSH) open to 0.0.0.0/0
-
Port 3389 (RDP) accessible globally
-
Database ports open externally
Potential Impact
-
Brute-force attacks
-
Ransomware deployment
-
Remote code execution
-
Data theft
Prevention Strategies
-
Restrict inbound traffic to trusted IP ranges
-
Use bastion hosts
-
Implement network segmentation
-
Continuously monitor exposed ports
4. Disabled Logging and Monitoring
Without logging, you cannot detect suspicious behavior.
Misconfiguration Examples
-
CloudTrail disabled in AWS
-
Azure Monitor not configured
-
Logging not retained long enough
Why It Matters
If a breach occurs, you will have:
-
No visibility into attacker actions
-
No forensic trail
-
Delayed incident response
Prevention
-
Enable logging across all services
-
Store logs in a centralized location
-
Use SIEM integration
-
Set up real-time alerts
5. Unencrypted Data at Rest or in Transit
Encryption misconfigurations can expose sensitive information.
Typical Mistakes
-
Not enabling default encryption
-
Using outdated encryption protocols
-
Failing to enforce HTTPS
The Risk
-
Compliance violations
-
Data interception
-
Credential theft
How to Fix It
-
Enable encryption by default
-
Use strong TLS protocols
-
Implement key management best practices
-
Rotate encryption keys regularly
6. Misconfigured Containers and Kubernetes Clusters
Container environments introduce new misconfiguration risks.
Examples
-
Kubernetes dashboard exposed publicly
-
Running containers as root
-
Insecure container images
-
Weak RBAC policies
Prevention
-
Use private container registries
-
Scan images for vulnerabilities
-
Restrict API server access
-
Enforce pod security policies
Real-World Cloud Misconfiguration Scenarios
Understanding real-world scenarios helps illustrate the severity of cloud security mistakes.
Data Exposure Through a Misconfigured S3 Bucket
A company uploads backup files to S3 but leaves the bucket public. Security researchers discover and report the exposure. Customer data becomes accessible online for weeks.
Cryptojacking via Open Compute Instances
An attacker scans for exposed cloud servers. After finding an open SSH port with weak credentials, they deploy cryptocurrency mining malware.
Privilege Escalation in Multi-Cloud Environments
A compromised developer account with excessive IAM permissions allows attackers to create new admin roles and move laterally across environments.
Root Causes of Cloud Misconfiguration
Cloud misconfigurations typically arise from:
Rapid Cloud Adoption
Organizations prioritize speed over security.
Complex Multi-Cloud Environments
Managing AWS, Azure, and GCP together increases configuration complexity.
Lack of Cloud Security Expertise
Traditional IT teams may not fully understand shared responsibility models.
Shadow IT
Developers deploy cloud resources without centralized governance.
How to Prevent Cloud Misconfigurations
Prevention requires both process and technology.
Implement Cloud Security Posture Management (CSPM)
CSPM tools continuously monitor cloud configurations and detect risky settings.
They help:
-
Identify compliance violations
-
Detect misconfigured resources
-
Automate remediation
Enforce the Principle of Least Privilege
Only grant access that users absolutely need. Regularly review and revoke unused permissions.
Automate Configuration Checks
Use infrastructure-as-code (IaC) scanning tools to detect misconfigurations before deployment.
Continuous Monitoring and Threat Detection
Security doesn’t stop after deployment. Continuous monitoring is essential to detect anomalies, suspicious behavior, and emerging risks.
Conduct Regular Cloud Security Audits
Schedule recurring audits to:
-
Review IAM policies
-
Evaluate exposed assets
-
Validate encryption settings
-
Check compliance frameworks
Cloud Misconfiguration and Compliance Risks
Regulatory frameworks require strict data protection standards.
Cloud misconfigurations can lead to:
-
GDPR penalties
-
HIPAA violations
-
PCI DSS non-compliance
-
SOC 2 audit failures
Proactive configuration management reduces legal and financial exposure.
Building a Strong Cloud Security Strategy
A mature cloud security strategy should include:
-
Asset visibility across all cloud environments
-
Continuous vulnerability assessment
-
Zero Trust principles
-
Endpoint detection and response (EDR)
-
Automated threat remediation
Organizations that combine configuration management with advanced threat detection significantly reduce breach risk.
FAQ: Cloud Misconfiguration Examples
1. What is the most common cloud misconfiguration?
Publicly exposed storage buckets are among the most common cloud misconfiguration examples, especially in AWS S3 environments.
2. How do cloud misconfigurations lead to data breaches?
Misconfigured permissions, open ports, or exposed storage can allow attackers to access sensitive data without exploiting complex vulnerabilities.
3. Are cloud providers responsible for misconfigurations?
Cloud providers follow a shared responsibility model. They secure the infrastructure, but customers must secure configurations, data, and access controls.
4. How can organizations detect cloud misconfigurations?
Organizations use cloud security posture management (CSPM), automated compliance checks, and continuous monitoring tools to identify misconfigurations.
5. How often should cloud configurations be reviewed?
Cloud environments should be continuously monitored, with formal audits conducted quarterly or after major infrastructure changes.
Final Thoughts: Don’t Let One Misconfiguration Cost You Millions
Cloud misconfigurations are preventable. Yet they remain one of the top causes of cloud data breaches.
The solution is not just better tools—it’s continuous visibility, proactive monitoring, and automated remediation.
If your organization operates in AWS, Azure, or Google Cloud, now is the time to evaluate your cloud security posture.
👉 Ready to strengthen your cloud security and eliminate misconfigurations before attackers exploit them?
Request a personalized demo today:
https://www.xcitium.com/request-demo/
Protect your cloud. Protect your business. Act now.