What Is SSO Login? A Complete Guide for Security Leaders
Updated on February 12, 2026, by Xcitium
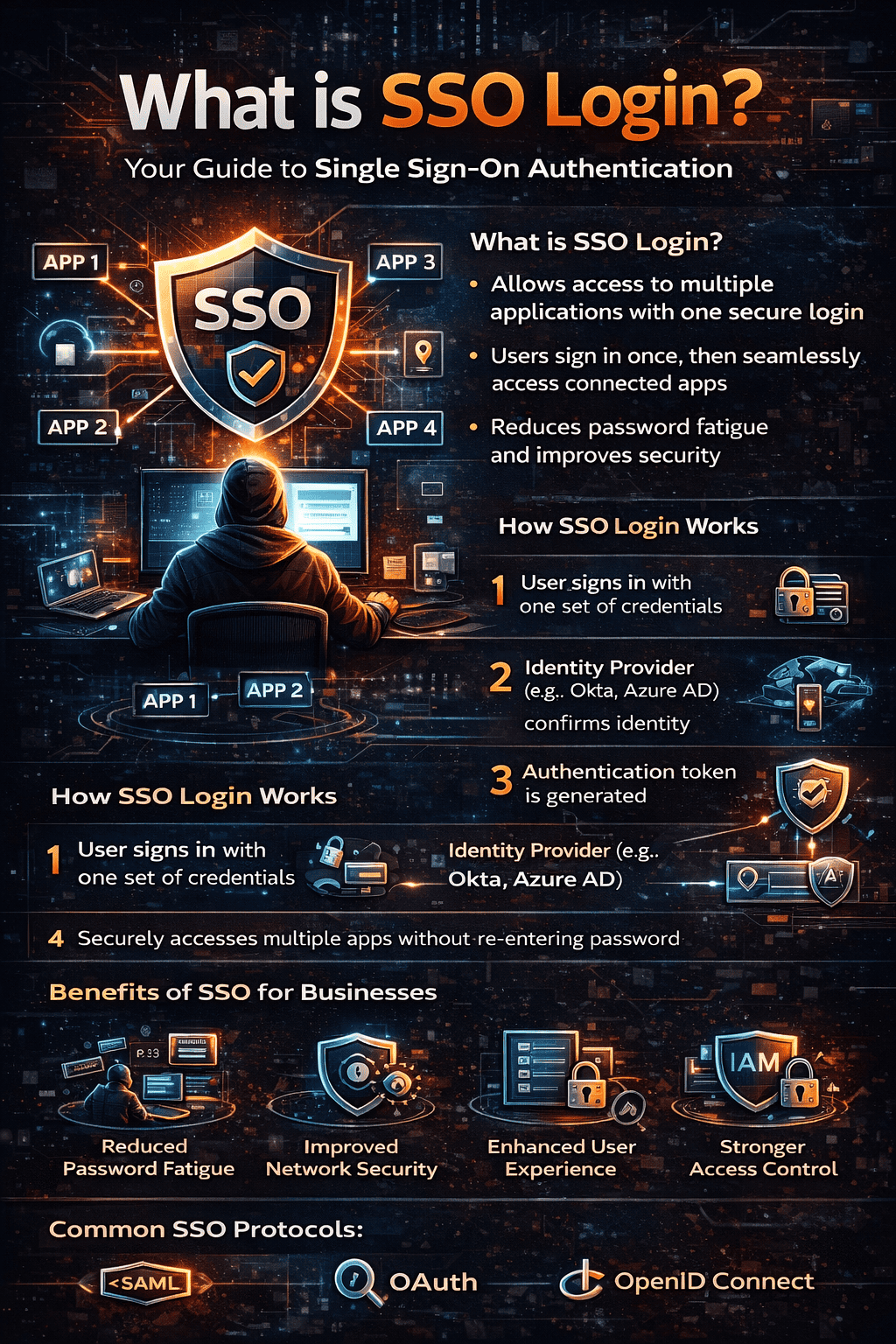
What is SSO login, and why are so many organizations adopting it? If your employees juggle multiple usernames and passwords daily, you’re not alone. Studies show that password fatigue increases security risks and lowers productivity. That’s where single sign-on (SSO) comes in.
So, what is SSO login in simple terms? SSO login, or single sign-on authentication, allows users to access multiple applications with one set of login credentials. Instead of signing in separately to each platform, users authenticate once and gain secure access to connected systems.
For IT managers, cybersecurity professionals, CEOs, and founders, understanding what is SSO login is essential for improving both security posture and operational efficiency.
What Is SSO Login and How Does It Work?
To fully understand what is SSO login, you need to know how authentication works behind the scenes.
When a user logs into an application, the system verifies identity using credentials such as a username and password. Without SSO, this process repeats for every application.
With single sign-on authentication:
-
The user logs in once.
-
An authentication token is generated.
-
The token grants access to other connected applications.
-
The user moves between systems without re-entering credentials.
In short, what is SSO login? It’s a centralized authentication system that simplifies access management while strengthening security controls.
Key Components of SSO Authentication
Understanding what is SSO login requires familiarity with several technical elements.
1. Identity Provider (IdP)
The Identity Provider verifies user credentials. Examples include Azure AD, Okta, or Google Identity.
2. Service Provider (SP)
These are the applications users access, such as SaaS tools or internal platforms.
3. Authentication Protocols
Common protocols include:
-
SAML (Security Assertion Markup Language)
-
OAuth
-
OpenID Connect
These standards enable secure token exchange between systems.
Benefits of SSO Login for Businesses
Many executives ask, what is SSO login really improving? The answer spans productivity and cybersecurity.
1. Reduced Password Fatigue
Employees no longer manage dozens of passwords. This reduces risky behavior like password reuse.
2. Stronger Access Control
Centralized authentication improves identity and access management (IAM).
3. Improved User Experience
Users log in once and move seamlessly across systems.
4. Enhanced Security Monitoring
IT teams can monitor authentication attempts from a single dashboard.
When properly configured, SSO login reduces both security risks and administrative burden.
SSO Login and Cybersecurity Risk Reduction
Understanding what is SSO login also means understanding its security value.
How SSO Strengthens Security
-
Centralized authentication policies
-
Easier enforcement of multi-factor authentication (MFA)
-
Faster revocation of user access
-
Reduced phishing risk from password reuse
If an employee leaves, IT can disable one account rather than dozens.
This limits insider threats and unauthorized access.
SSO vs Multi-Factor Authentication (MFA)
A common misconception arises when discussing what is SSO login.
SSO and MFA are not the same.
-
SSO simplifies access with one login.
-
MFA adds additional verification steps.
The best practice is combining SSO login with MFA authentication for maximum security.
For example:
-
User logs in via SSO.
-
System prompts for a second factor (OTP, biometric, hardware key).
-
Access is granted securely.
This layered approach strengthens enterprise security posture.
Risks and Challenges of SSO Login
While beneficial, SSO login introduces certain considerations.
1. Single Point of Failure
If the SSO system is compromised, multiple systems may be at risk.
2. Dependency on Identity Provider
System outages can affect all connected applications.
3. Complex Implementation
Integrating legacy systems may require customization.
Therefore, understanding what is SSO login must include awareness of these trade-offs.
SSO Login in Cloud and Hybrid Environments
Modern enterprises operate in hybrid ecosystems.
Employees use:
-
Cloud SaaS applications
-
On-premises servers
-
Remote work devices
-
Mobile endpoints
SSO login bridges these environments through centralized authentication.
For IT managers, this reduces complexity. For CEOs, it improves governance and compliance oversight.
Industry Use Cases for SSO Login
Financial Services
Banks use SSO login to control secure access to internal financial systems.
Healthcare
Hospitals rely on single sign-on authentication to access electronic health records efficiently.
Manufacturing
Production systems require secure, role-based access.
SaaS and Technology Firms
Developers access multiple tools daily. SSO login streamlines productivity.
Understanding what is SSO login helps leaders evaluate operational impact across industries.
How to Implement SSO Login Successfully
If you’re considering deployment, here are actionable steps.
Step 1: Assess Current Identity Infrastructure
Inventory applications, user roles, and access levels.
Step 2: Choose the Right Identity Provider
Select an IdP that supports SAML, OAuth, or OpenID Connect.
Step 3: Enforce MFA
Combine SSO login with strong authentication policies.
Step 4: Monitor Continuously
Track login attempts, failed authentications, and suspicious activity.
Step 5: Train Employees
Human error remains a top cybersecurity risk.
A structured rollout reduces friction and security gaps.
SSO Login and Zero Trust Architecture
Modern cybersecurity strategies embrace Zero Trust.
Zero Trust assumes no device or user is trusted by default.
SSO login supports Zero Trust by:
-
Centralizing authentication
-
Enforcing least privilege access
-
Integrating with conditional access policies
However, Zero Trust requires continuous verification beyond initial login.
Therefore, SSO login should integrate with endpoint detection and response (EDR) solutions.
Common SSO Authentication Protocols Explained
SAML
Widely used in enterprise environments. Exchanges authentication data securely between IdP and SP.
OAuth
Often used for API authorization and delegated access.
OpenID Connect
Built on OAuth. Adds identity verification features.
Choosing the right protocol depends on your organization’s architecture.
Understanding what is SSO login includes knowing how these standards secure authentication.
Frequently Asked Questions (FAQ)
1. What is SSO login in simple terms?
What is SSO login? It allows users to log in once and access multiple applications without signing in again.
2. Is SSO login secure?
Yes, especially when combined with MFA. It centralizes authentication and reduces password risks.
3. Does SSO eliminate passwords?
Not entirely. Users still log in once, but they avoid repeated credential entry across systems.
4. Can SSO login be hacked?
Like any system, it can be targeted. That’s why strong MFA, monitoring, and endpoint security are critical.
5. Is SSO suitable for small businesses?
Yes. Cloud-based SSO solutions scale well for both small and large enterprises.
Final Thoughts: Is SSO Login Enough?
So, what is SSO login in the bigger cybersecurity picture? It’s a powerful identity and access management solution that simplifies authentication and strengthens security controls.
However, authentication alone does not stop ransomware, phishing, or endpoint compromise.
Modern threats require layered defense, including:
-
Endpoint protection
-
Threat containment
-
Continuous monitoring
-
Managed detection and response
If your organization wants to strengthen authentication while protecting endpoints and networks from advanced threats, it’s time to take the next step.
👉 Discover how Xcitium helps businesses combine identity protection with real-time threat containment and advanced cybersecurity solutions.
Request your personalized demo today:
https://www.xcitium.com/request-demo/
Secure access starts with SSO login — but complete protection requires a smarter security strategy.