How Do I Shut Off TCP on My Computer? A Complete Security-Focused Guide
Updated on February 6, 2026, by Xcitium
Have you ever asked yourself, how do I shut off TCP on my computer, and wondered whether it’s even a good idea? You’re not alone. As cybersecurity awareness grows, more users and IT leaders are questioning which network services really need to be enabled—and which ones increase risk.
TCP (Transmission Control Protocol) is fundamental to how computers communicate. However, there are situations where disabling or restricting TCP can reduce exposure, limit attack surfaces, or support troubleshooting and compliance goals. In this guide, we’ll explain what TCP is, when it makes sense to disable it, how to do so safely, and what alternatives may be better for security.
What Is TCP and Why Is It Enabled by Default?
Before answering how do I shut off TCP on my computer, it’s important to understand what TCP does.
TCP is a core communication protocol used by most applications on the internet. It ensures reliable data transmission by:
-
Establishing connections between systems
-
Confirming data delivery
-
Retransmitting lost packets
-
Managing traffic flow
Without TCP, common services like web browsing, email, file transfers, and remote access would not function properly.
Because of its importance, TCP is enabled by default on all major operating systems.
Why Would Someone Want to Shut Off TCP?
Shutting off TCP entirely is uncommon, but there are valid reasons users ask how do I shut off TCP on my computer.
Common reasons include:
-
Reducing attack surface during incident response
-
Troubleshooting network conflicts
-
Securing isolated or air-gapped systems
-
Limiting unnecessary inbound connections
-
Testing application behavior
In enterprise environments, the goal is usually control, not complete shutdown.
Important Warning Before Disabling TCP
TCP is deeply integrated into modern operating systems. Disabling it completely can:
-
Break internet connectivity
-
Disable essential applications
-
Interrupt system updates
-
Cause management tools to fail
For most users, restricting TCP traffic is safer than fully disabling it. Always document changes and test in controlled environments first.
How Do I Shut Off TCP on My Computer? (Conceptual Overview)
Instead of a single “off switch,” TCP can be disabled or restricted in several ways:
-
Disabling TCP/IP bindings
-
Blocking TCP traffic with a firewall
-
Disabling TCP-based services
-
Removing network adapters (advanced use cases)
Each method has different security and usability impacts.
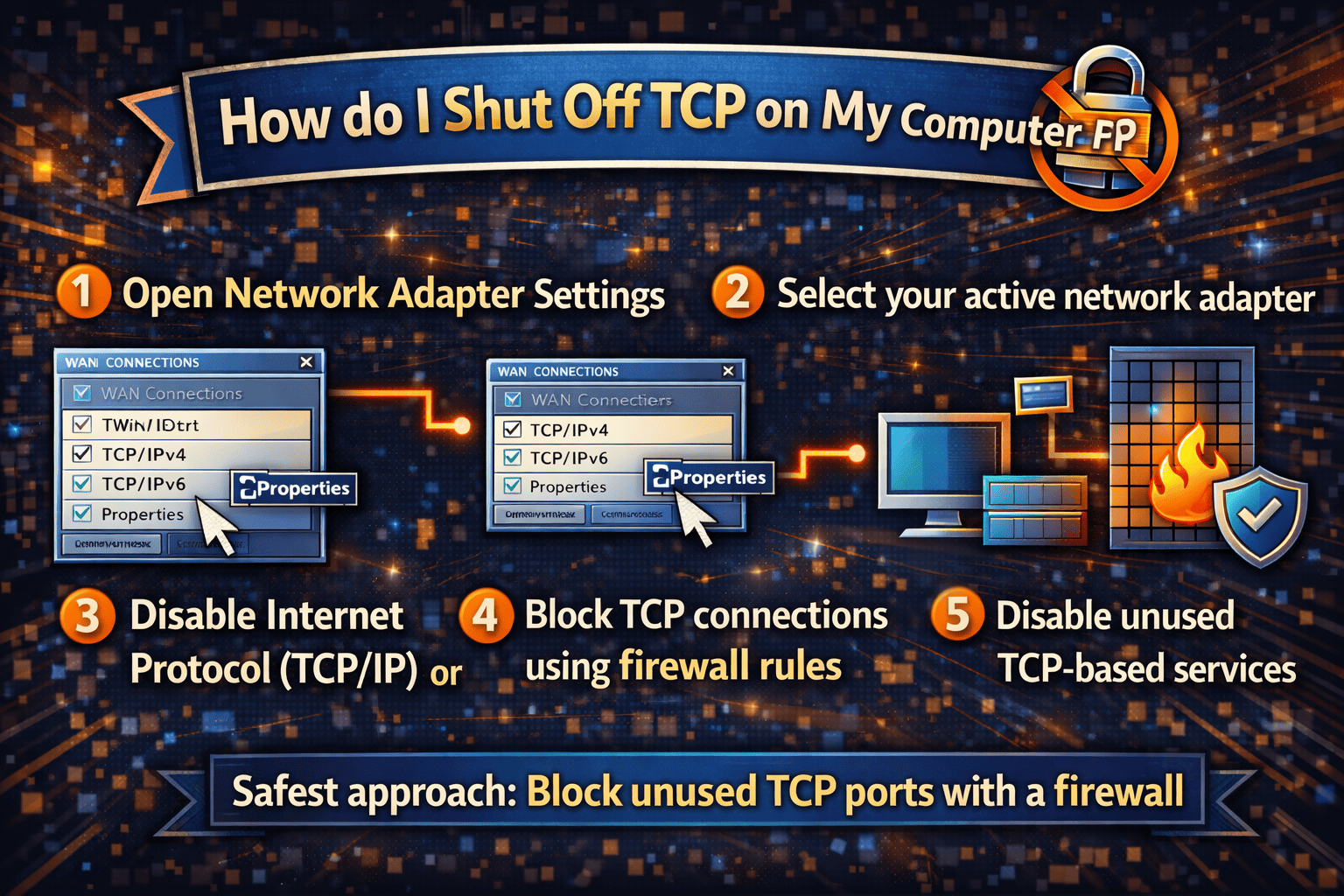
How to Disable TCP/IP Using Network Settings
On Windows Systems
If you’re asking how do I shut off TCP on my computer running Windows, this method affects network bindings.
General approach:
-
Open Network Connections
-
Access adapter properties
-
Disable Internet Protocol (TCP/IP)
This removes TCP/IP from the network adapter, effectively cutting off TCP communication.
Use with caution: This will disconnect the system from most networks.
On macOS Systems
macOS does not allow full TCP shutdown via the GUI, but TCP can be restricted.
Common methods include:
-
Disabling network interfaces
-
Using firewall rules to block TCP
-
Removing TCP-based services
macOS is designed to keep core networking intact, so restrictions are preferred.
On Linux Systems
Linux provides the most flexibility for users asking how do I shut off TCP on my computer.
Options include:
-
Disabling network interfaces
-
Blocking TCP with iptables or nftables
-
Modifying kernel networking parameters
Linux administrators typically block TCP ports instead of disabling the protocol itself.
Using Firewalls to Effectively “Shut Off” TCP
For most users, firewalls provide the safest answer to how do I shut off TCP on my computer.
Firewall-based TCP control allows you to:
-
Block inbound TCP connections
-
Restrict outbound TCP traffic
-
Allow only specific TCP ports
-
Log and monitor connection attempts
This approach preserves system stability while improving security.
Disabling TCP-Based Services Instead of TCP Itself
Many risks come from services—not the TCP protocol.
Examples of TCP-based services:
-
Remote Desktop (RDP)
-
FTP and file sharing
-
Database listeners
-
Web servers
Disabling unused services significantly reduces exposure without breaking core networking.
TCP and Cybersecurity: Why Control Matters
Understanding how do I shut off TCP on my computer is often part of a broader security strategy.
TCP-related risks include:
-
Open ports targeted by attackers
-
Exploitable services listening on TCP
-
Lateral movement opportunities
-
Data exfiltration paths
Security teams focus on visibility and control, not blind shutdowns.
When You Should NOT Disable TCP
There are many situations where disabling TCP is a bad idea.
Avoid disabling TCP if:
-
The system requires internet access
-
Remote management tools are needed
-
Security updates rely on TCP
-
The device is part of a business network
In these cases, segmentation and monitoring are better solutions.
Safer Alternatives to Shutting Off TCP
If your goal is security, there are better options than fully disabling TCP.
Recommended alternatives:
-
Close unused TCP ports
-
Implement host-based firewalls
-
Use intrusion detection systems
-
Apply Zero Trust networking
-
Monitor TCP connections continuously
These approaches balance security and functionality.
TCP in Enterprise and Industry Environments
For IT managers and executives, how do I shut off TCP on my computer often applies to specific systems.
Industry use cases include:
-
Isolated manufacturing equipment
-
Kiosk or POS systems
-
Forensic or incident response hosts
-
Testing and sandbox environments
In these scenarios, TCP restrictions are carefully planned and documented.
Logging and Monitoring TCP Activity
Before disabling TCP, it’s smart to understand how it’s being used.
Monitoring TCP activity helps:
-
Identify unnecessary connections
-
Detect suspicious behavior
-
Validate firewall rules
-
Support incident investigations
Visibility should always come before restriction.
Common Mistakes When Disabling TCP
Many users run into problems when attempting to shut off TCP.
Common mistakes include:
-
Disabling TCP without a rollback plan
-
Blocking all traffic instead of specific ports
-
Forgetting management and update needs
-
Ignoring application dependencies
Careful planning prevents outages.
FAQs: How Do I Shut Off TCP on My Computer?
1. Can I completely disable TCP on my computer?
Yes, but it is not recommended for most systems because it breaks essential network functions.
2. Is disabling TCP good for security?
Only in limited cases. Restricting TCP traffic is usually safer than disabling it entirely.
3. What’s the safest way to shut off TCP?
Using firewall rules to block unnecessary TCP ports and connections.
4. Will disabling TCP improve performance?
Not usually. It often causes application failures rather than performance gains.
5. Should businesses disable TCP on endpoints?
No. Businesses should manage TCP through firewalls, segmentation, and monitoring.
Final Thoughts: Should You Shut Off TCP?
If you’re asking how do I shut off TCP on my computer, the real question is why you want to do it.
TCP is essential to modern computing. Disabling it entirely is rarely necessary and often harmful. In most cases, controlling TCP is far more effective than shutting it off.
Smart security strategies focus on:
-
Reducing exposure
-
Monitoring activity
-
Blocking unnecessary services
-
Responding quickly to threats
That approach keeps systems secure without sacrificing usability.
Take the Next Step Toward Smarter Network Security
Want better visibility and control over network activity—without breaking critical systems?
👉 Request a demo today:
https://www.xcitium.com/request-demo/
See how advanced visibility and security controls help organizations manage network risk effectively.


 (1 votes, average: 4.00 out of 5)
(1 votes, average: 4.00 out of 5)