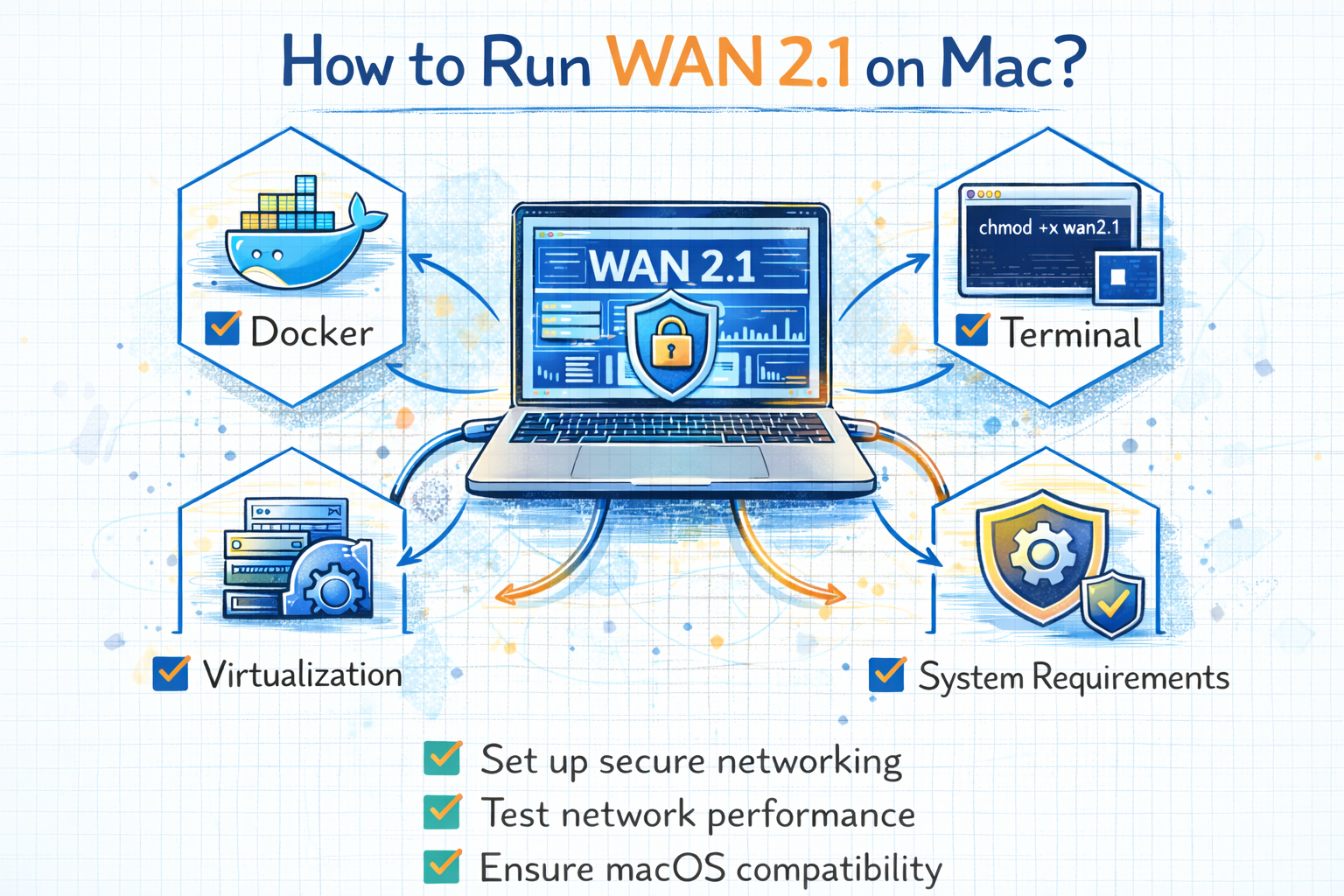
How to Run WAN 2.1 on Mac: A Complete Step-by-Step Guide
Updated on January 12, 2026, by Xcitium
Are you trying to figure out how to run WAN 2.1 on Mac but unsure where to start? You’re not alone. Many users—especially IT professionals and security teams—struggle with running WAN-based tools on macOS due to compatibility and configuration challenges.
Understanding how to run WAN 2.1 on Mac is essential for organizations that rely on wide area networking for secure access, testing, or performance monitoring. macOS has strong security controls, which is great—but it also means setup must be done correctly to avoid errors.
In this guide, you’ll learn exactly how to run WAN 2.1 on Mac, including system requirements, installation steps, common issues, and best practices for secure operation.
What Is WAN 2.1 and Why Use It on macOS?
Before diving into how to run WAN 2.1 on Mac, it’s important to understand what WAN 2.1 is and why it matters.
WAN 2.1 typically refers to an updated Wide Area Network configuration or toolset designed to improve performance, reliability, and security across distributed networks. It is commonly used for:
-
Network testing and simulation
-
Secure remote connectivity
-
Performance monitoring
-
Enterprise networking environments
macOS users often need WAN 2.1 for development, testing, or secure access in hybrid or remote work setups.
System Requirements to Run WAN 2.1 on Mac
Meeting system requirements ensures a smooth setup.
Minimum macOS Requirements
-
macOS Monterey or later
-
Intel or Apple Silicon (M1/M2/M3) processor
-
At least 8 GB RAM (16 GB recommended)
-
Stable internet connection
-
Administrator access
If you’re serious about how to run WAN 2.1 on Mac, make sure your system is fully updated before proceeding.
How to Run WAN 2.1 on Mac: Pre-Installation Checklist
Preparation reduces errors during setup.
Before You Begin
-
Update macOS to the latest version
-
Install Xcode Command Line Tools
-
Disable conflicting network services
-
Verify firewall and security permissions
Many installation failures related to how to run WAN 2.1 on Mac happen because these steps are skipped.
How to Run WAN 2.1 on Mac Using Native Tools
Some WAN 2.1 implementations can run natively on macOS.
Step-by-Step Instructions
-
Download the WAN 2.1 package from the official source
-
Open Terminal
-
Grant execution permissions using:
-
Run the application:
-
Verify the service is active
This is the most direct method when learning how to run WAN 2.1 on Mac.
How to Run WAN 2.1 on Mac Using Virtualization
If native execution isn’t supported, virtualization is a reliable option.
Popular Virtualization Options
-
Parallels Desktop
-
VMware Fusion
-
VirtualBox
Steps Using Virtualization
-
Install virtualization software
-
Create a Linux or Windows VM
-
Install WAN 2.1 inside the VM
-
Configure network bridging
-
Test connectivity
Virtualization offers flexibility and compatibility when exploring how to run WAN 2.1 on Mac in complex environments.
How to Run WAN 2.1 on Mac with Docker
Docker is another powerful solution.
Why Use Docker?
-
Lightweight
-
Isolated environment
-
Easy to manage and scale
Basic Docker Workflow
-
Install Docker Desktop for Mac
-
Pull the WAN 2.1 container image
-
Configure network ports
-
Run the container
Docker is often preferred by DevOps teams focused on automation and security.
Common Issues When Running WAN 2.1 on Mac
Even with proper setup, issues can arise.
Frequent Problems
-
Permission denied errors
-
Network interface conflicts
-
Firewall blocking traffic
-
Incompatible binaries
Quick Fixes
-
Run Terminal with admin privileges
-
Allow WAN 2.1 in macOS Firewall
-
Disable VPNs temporarily
-
Check logs for errors
Understanding these issues makes how to run WAN 2.1 on Mac far less frustrating.
Security Best Practices for WAN 2.1 on macOS
Security should never be an afterthought.
Recommended Practices
-
Use strong authentication
-
Encrypt WAN traffic
-
Monitor logs regularly
-
Restrict access by role
-
Keep WAN 2.1 updated
macOS provides strong security features—use them to enhance WAN 2.1 protection.
Use Cases for WAN 2.1 on Mac
WAN 2.1 supports multiple business scenarios.
Common Use Cases
-
Secure remote workforce access
-
Network performance testing
-
Application deployment testing
-
Hybrid cloud connectivity
For IT managers and executives, mastering how to run WAN 2.1 on Mac improves operational efficiency.
Troubleshooting Tips for WAN 2.1 on Mac
If WAN 2.1 doesn’t start correctly:
-
Verify system architecture compatibility
-
Check Terminal error output
-
Confirm network permissions
-
Restart network services
Troubleshooting is a normal part of learning how to run WAN 2.1 on Mac.
Frequently Asked Questions (FAQ)
1. How to run WAN 2.1 on Mac without virtualization?
If a native macOS binary exists, you can run it directly via Terminal with proper permissions.
2. Can WAN 2.1 run on Apple Silicon Macs?
Yes, but compatibility depends on the build. Docker or virtualization often works best.
3. Is WAN 2.1 secure on macOS?
Yes, when combined with macOS firewall rules and encryption.
4. Do I need admin access to run WAN 2.1 on Mac?
Most setups require administrator privileges.
5. What is the easiest way to run WAN 2.1 on Mac?
Docker is often the simplest and most reliable option.
Final Thoughts: Mastering How to Run WAN 2.1 on Mac
Understanding how to run WAN 2.1 on Mac gives you greater control over networking, testing, and secure connectivity. Whether you choose native execution, virtualization, or Docker, the right approach depends on your environment and security needs.
For organizations focused on modern cybersecurity and network visibility, proper WAN configuration is essential.
👉 See how advanced security can support your network—request a demo today:
https://www.xcitium.com/request-demo/