What Is NAT Networking? A Complete Guide for Secure Modern Networks
Updated on December 30, 2025, by Xcitium
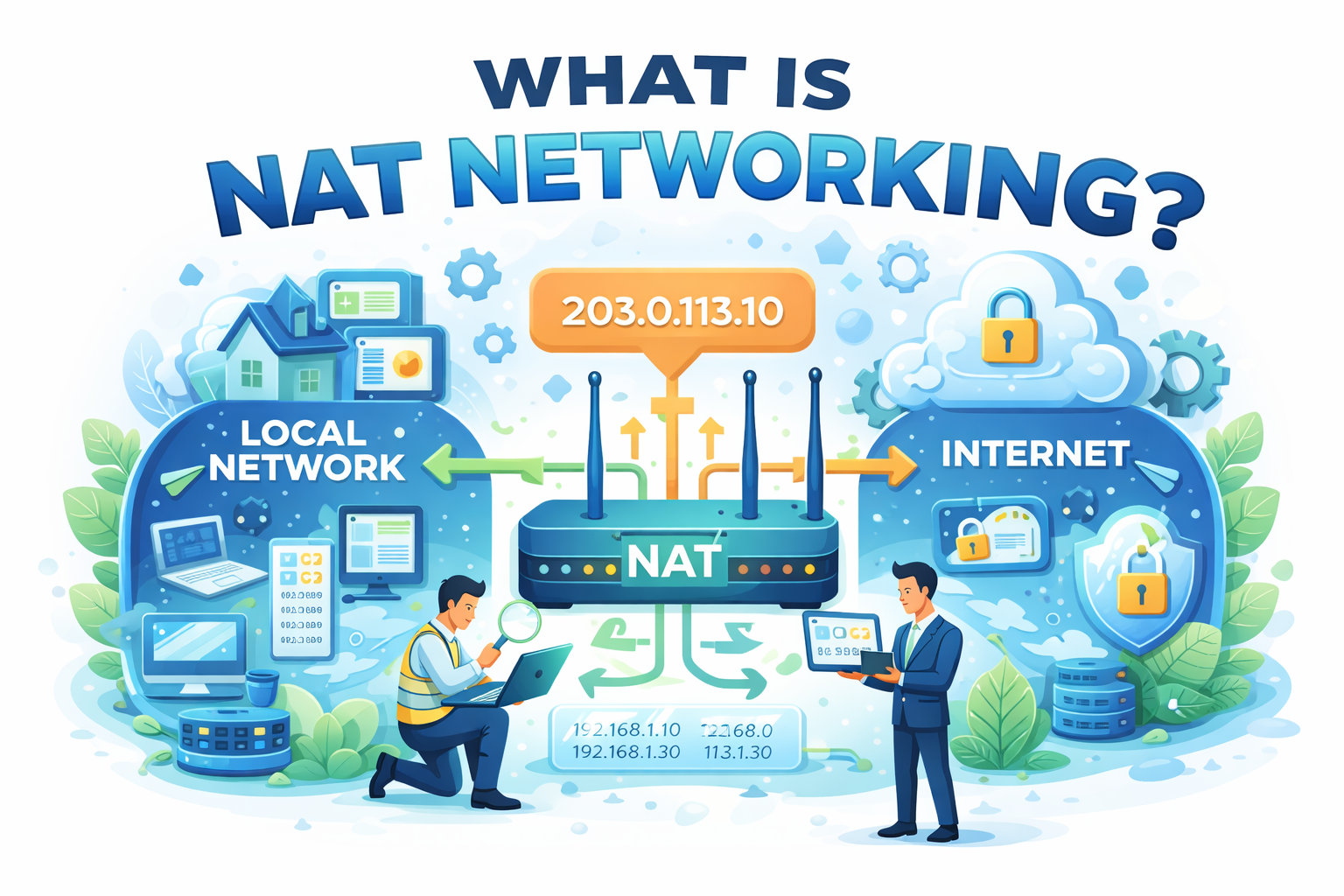
What is NAT networking, and why does almost every modern network depend on it? As organizations expand their digital footprint, the demand for IP addresses, security, and efficient traffic management continues to grow. Network Address Translation (NAT) solves a critical problem by allowing multiple devices to share a single public IP address while remaining hidden from the internet.
For cybersecurity professionals, IT managers, and business leaders, understanding NAT networking is essential. It plays a foundational role in network security, cloud environments, virtualization, and enterprise connectivity. This guide explains NAT networking in simple terms, explores how it works, and highlights why it remains vital in today’s connected world.
What Is NAT Networking?
NAT networking (Network Address Translation) is a networking technique that translates private IP addresses used within a local network into a public IP address used on the internet, and vice versa. This translation happens at a network device such as a router or firewall.
In simple terms, NAT allows many internal devices to communicate with external networks using a single public IP address. Without NAT networking, the global internet would have run out of IPv4 addresses long ago.
NAT networking also adds a layer of security by hiding internal IP addresses from external users, making it harder for attackers to target individual devices directly.
Why NAT Networking Is Important
NAT networking plays a critical role in both performance and security.
Conserves IP Addresses
IPv4 addresses are limited. NAT allows organizations to reuse private IP ranges internally while using fewer public IPs.
Enhances Network Security
By masking internal IP addresses, NAT networking reduces direct exposure to the internet.
Simplifies Network Design
Private networks can be built without coordination with internet service providers for public IP allocation.
Enables Cloud and Virtualization
NAT is widely used in cloud platforms, containers, and virtual machines to manage traffic efficiently.
For businesses of all sizes, NAT networking is a practical and cost-effective solution.
How NAT Networking Works
Understanding how NAT networking works helps clarify its value.
When a device inside a private network sends a request to the internet:
-
The internal device sends traffic using its private IP address.
-
The NAT-enabled router replaces the private IP with a public IP.
-
The router records the translation in a NAT table.
-
When the response returns, the router translates the public IP back to the private IP.
-
The response reaches the correct internal device.
This process happens in milliseconds and is invisible to users.
Types of NAT Networking
There are several types of NAT networking, each serving different use cases.
Static NAT
Maps one private IP address to one public IP address.
Use case: Hosting a server internally that must be accessible from the internet.
Dynamic NAT
Maps private IP addresses to a pool of public IP addresses.
Use case: Networks with multiple public IPs but fewer simultaneous connections.
Port Address Translation (PAT)
Also known as NAT overload, this allows many devices to share a single public IP using different ports.
Use case: Most home and enterprise networks.
Carrier-Grade NAT (CGNAT)
Used by ISPs to manage IP scarcity across large customer bases.
Each NAT type balances scalability, security, and performance differently.
NAT Networking vs Routing: What’s the Difference?
Although often confused, NAT networking and routing serve different purposes.
| Feature | NAT Networking | Routing |
|---|---|---|
| IP Address Change | Yes | No |
| Primary Purpose | Address translation | Path selection |
| Security Benefit | Masks internal IPs | No inherent masking |
| Common Device | Firewall/Router | Router |
NAT networking complements routing rather than replacing it.
NAT Networking and Security: Benefits and Limitations
Security Benefits
-
Hides internal IP addresses
-
Reduces unsolicited inbound traffic
-
Works well with firewalls and access controls
Security Limitations
-
Not a replacement for a firewall
-
Can complicate logging and visibility
-
Breaks some end-to-end security models
While NAT networking adds a layer of protection, it should always be paired with modern security controls.
NAT Networking in Cloud and Virtual Environments
NAT networking is heavily used in cloud platforms and virtual infrastructures.
Cloud NAT Use Cases
-
Allow private instances to access the internet securely
-
Prevent direct inbound access to workloads
-
Reduce public IP costs
Virtualization and Containers
-
Enables multiple virtual machines to share a host network
-
Supports microsegmentation and isolation
Major cloud providers rely on NAT networking to balance security and scalability.
Common NAT Networking Challenges
Despite its benefits, NAT networking introduces some challenges.
Performance Bottlenecks
Heavy NAT usage can impact throughput if not properly scaled.
Application Compatibility
Some applications struggle with NAT traversal, especially VoIP and peer-to-peer services.
Troubleshooting Complexity
IP translation can complicate traffic analysis and debugging.
Logging and Visibility
Tracking original IP addresses requires proper logging and monitoring.
Proactive design and monitoring help overcome these limitations.
Best Practices for NAT Networking
Following best practices ensures NAT networking remains secure and efficient.
Use Firewalls with NAT
Combine NAT with stateful firewalls for stronger protection.
Monitor NAT Tables
Avoid resource exhaustion by monitoring active translations.
Limit Inbound NAT Rules
Only expose services that are absolutely necessary.
Implement Logging
Capture both original and translated IPs for auditing and incident response.
Plan for IPv6
While NAT is common in IPv4, IPv6 reduces reliance on NAT networking over time.
NAT Networking and IPv6: The Future
IPv6 was designed to eliminate the need for NAT by providing a massive address space. However, NAT networking remains widely used due to:
-
Legacy IPv4 systems
-
Security preferences
-
Operational familiarity
In practice, many organizations run dual-stack environments, using both NAT networking and IPv6 simultaneously.
Real-World Use Cases of NAT Networking
Enterprise Networks
Protect internal systems while enabling internet access.
Remote Workforces
Secure VPN connections rely on NAT traversal.
Data Centers
Segment workloads while optimizing IP usage.
ISPs
Use CGNAT to support millions of customers.
NAT networking remains deeply embedded across industries.
FAQs About NAT Networking
1. What is NAT networking in simple terms?
NAT networking allows multiple devices to share a single public IP address while hiding their private IPs from the internet.
2. Is NAT networking secure?
NAT provides basic protection by masking IP addresses but should be combined with firewalls and security monitoring.
3. Does NAT affect performance?
NAT can introduce slight latency, but modern devices handle translations efficiently with minimal impact.
4. Is NAT still needed with IPv6?
IPv6 reduces the need for NAT, but many organizations still use NAT for security and compatibility reasons.
5. What is the most common type of NAT?
Port Address Translation (PAT) is the most widely used NAT method today.
Final Thoughts: Why NAT Networking Still Matters
Understanding what is NAT networking is essential for anyone responsible for modern IT infrastructure. From conserving IP addresses to improving security and enabling cloud connectivity, NAT networking remains a cornerstone of digital networks.
As cyber threats increase and networks grow more complex, pairing NAT with modern security platforms ensures visibility, control, and protection across your environment.
🔐 Ready to strengthen your network security and visibility?
See how a modern security platform can help protect your infrastructure.
👉 Request a demo today:
https://www.xcitium.com/request-demo/



 (3 votes, average: 3.67 out of 5)
(3 votes, average: 3.67 out of 5)