What Is ZTNA? The Future of Secure Network Access
Updated on November 7, 2025, by Xcitium
Have you ever wondered why traditional VPNs are no longer enough to protect corporate data?
In an era of hybrid work and cloud transformation, perimeter-based security models are collapsing under the weight of complexity and remote threats. That’s where ZTNA (Zero Trust Network Access) steps in — a modern security approach that’s redefining how organizations protect data, users, and applications.
In this comprehensive guide, we’ll explore what ZTNA is, how it works, its benefits, and why it’s becoming the cornerstone of cybersecurity for enterprises worldwide.
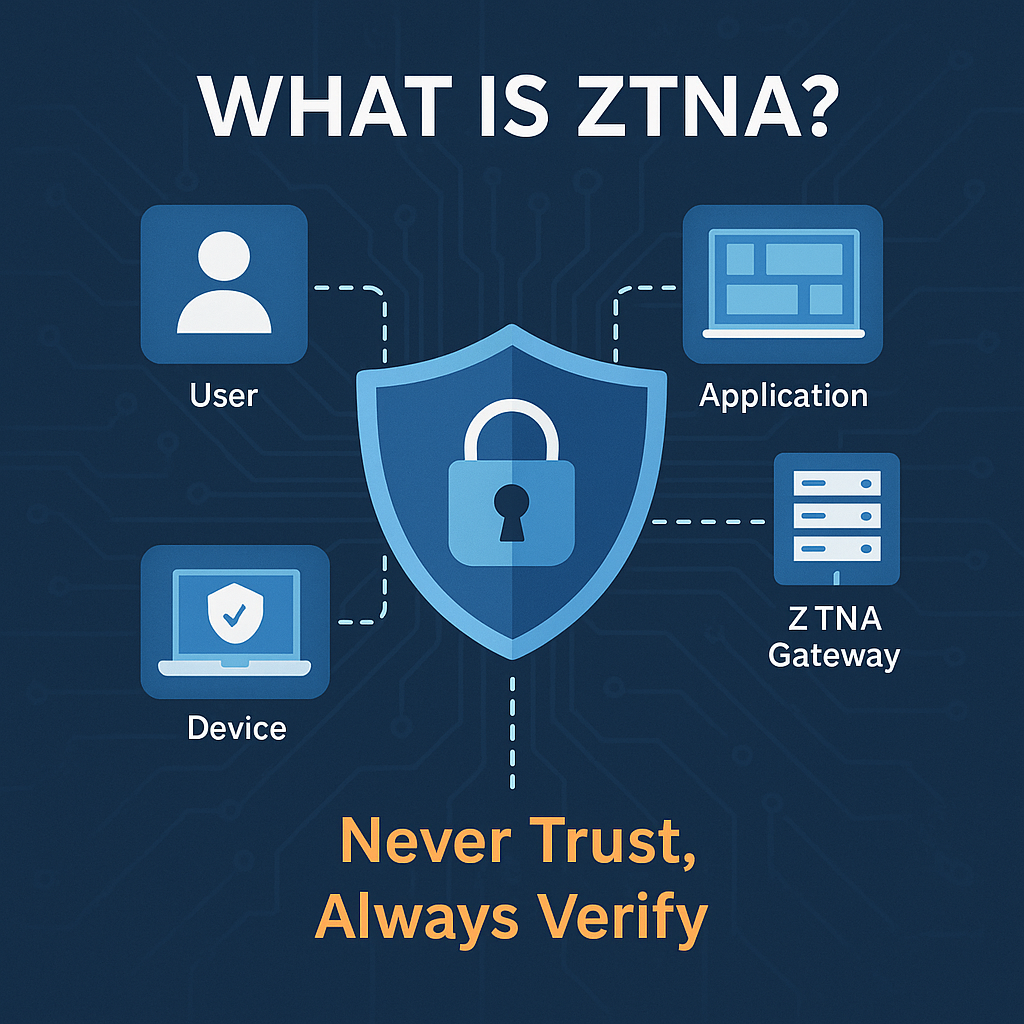
What Is ZTNA (Zero Trust Network Access)?
ZTNA, or Zero Trust Network Access, is a security model and technology framework designed to provide secure, identity-based access to applications and data — without ever implicitly trusting any user or device.
The principle behind ZTNA is simple yet powerful:
“Never trust, always verify.”
Unlike traditional security models that assume everything inside the corporate network is safe, ZTNA assumes no user or device is trustworthy by default — whether inside or outside the network.
Access is granted only after verification of multiple factors, including user identity, device posture, location, and security compliance.
How ZTNA Works
ZTNA works by creating a secure gateway between users and applications. Instead of granting full network access (like a VPN), ZTNA provides application-level access — meaning users can only reach the specific apps and data they are authorized to use.
Here’s how it functions step-by-step:
1. Authentication and Verification
When a user requests access, the ZTNA system authenticates their identity using multi-factor authentication (MFA), SSO (Single Sign-On), and device posture checks.
2. Policy Evaluation
The system then evaluates the request against pre-defined access policies — based on role, device security, time of access, and location.
3. Context-Aware Access
Only after successful verification does the ZTNA broker connect the user to the requested application — without exposing the rest of the network.
4. Continuous Monitoring
ZTNA doesn’t stop at login. It continuously monitors user behavior and network activity to detect anomalies or suspicious behavior in real time.
This dynamic verification process ensures maximum protection — even against insider threats and credential-based attacks.
Key Principles of ZTNA
ZTNA operates on several foundational principles that make it a more secure alternative to legacy access controls:
1. Zero Implicit Trust
No user or device — internal or external — is trusted by default.
2. Least Privilege Access
Users are granted access only to the resources they need, minimizing potential attack surfaces.
3. Micro-Segmentation
ZTNA isolates applications and systems into smaller “segments” to prevent lateral movement by attackers.
4. Continuous Verification
User and device trust is re-evaluated dynamically, based on changing context and behavior.
5. Secure, Encrypted Connections
All communication between users and applications is end-to-end encrypted, reducing data interception risks.
Traditional VPN vs. ZTNA: What’s the Difference?
| Feature | VPN (Virtual Private Network) | ZTNA (Zero Trust Network Access) |
|---|---|---|
| Access Scope | Grants full network access | Application-level access only |
| Trust Model | Implicit trust (inside network) | Zero trust (continuous validation) |
| Security | Vulnerable to credential theft and lateral attacks | Context-aware, identity-based security |
| Scalability | Difficult in hybrid and cloud environments | Designed for cloud and remote users |
| User Experience | Slower, network-based | Seamless, app-based access |
ZTNA essentially modernizes the VPN, removing its biggest weaknesses — excessive trust and poor visibility.
Why ZTNA Matters in Modern Cybersecurity
With the rise of remote work, SaaS applications, and hybrid cloud environments, the traditional network perimeter has dissolved. Cyber attackers exploit this by targeting VPNs, endpoints, and unmanaged devices.
ZTNA solves these challenges by implementing identity-first, adaptive access controls, ensuring that only verified users on secure devices can reach enterprise resources.
ZTNA in Numbers:
-
61% of organizations have adopted or plan to adopt Zero Trust security models (Gartner).
-
80% of data breaches involve compromised credentials (Verizon DBIR).
-
ZTNA adoption is expected to grow by over 25% annually through 2028.
These statistics make one thing clear — ZTNA is not a trend; it’s the future of network security.
Core Components of a ZTNA Architecture
A strong ZTNA solution includes multiple layers of security and orchestration.
1. Identity Provider (IdP)
Handles authentication through SSO, MFA, and identity federation.
2. Policy Engine
Defines and enforces access policies based on risk factors and contextual data.
3. Connector or Gateway
Establishes a secure tunnel between users and applications, often deployed on-premises or in the cloud.
4. Endpoint Security Agent
Monitors device posture, ensuring that endpoints meet compliance before access is granted.
5. Continuous Monitoring
Uses AI and analytics to detect behavioral anomalies and revoke access dynamically.
Benefits of Implementing ZTNA
ZTNA offers multiple benefits that align with the security, scalability, and performance needs of modern enterprises.
1. Stronger Security
ZTNA enforces least privilege access and isolates applications, reducing attack surfaces and preventing lateral movement.
2. Improved User Experience
Users enjoy fast, seamless, and secure access to applications — without slow VPN tunnels or complex configurations.
3. Cloud-Native Integration
ZTNA supports hybrid and multi-cloud environments, ensuring consistent protection across on-premises and cloud workloads.
4. Reduced Risk of Breaches
By continuously verifying identities and device health, ZTNA prevents unauthorized access and data exfiltration.
5. Simplified Compliance
ZTNA supports regulatory compliance frameworks such as GDPR, HIPAA, and ISO 27001 by enforcing data access controls.
6. Lower Operational Costs
ZTNA reduces dependency on legacy VPN hardware and network maintenance costs.
ZTNA and Zero Trust Security Framework
ZTNA is often seen as a building block of the broader Zero Trust Security model. While ZTNA focuses on access control, Zero Trust applies across the entire IT ecosystem — including users, devices, workloads, and data.
Together, they create a security posture where:
-
Every access request is verified.
-
Every action is monitored.
-
Every resource is protected.
In essence, ZTNA operationalizes Zero Trust, making it actionable and measurable for modern organizations.
Use Cases of ZTNA
ZTNA adoption spans industries and use cases, including:
1. Secure Remote Work
ZTNA allows employees to safely access corporate applications from anywhere, without exposing the internal network.
2. Third-Party Access Management
Organizations can grant controlled, temporary access to vendors and contractors without network-wide exposure.
3. Multi-Cloud Access Control
ZTNA centralizes security across AWS, Azure, and Google Cloud environments.
4. M&A Integrations
When merging organizations with different systems, ZTNA simplifies secure integration and access control.
5. Application Security
ZTNA protects both internal and external apps by hiding them from the public internet.
Challenges of Implementing ZTNA
While ZTNA provides superior protection, it also comes with certain challenges:
-
Complex Migration from VPNs – Transitioning from legacy systems requires planning and integration.
-
Visibility Gaps – Without centralized management, monitoring hybrid environments can be difficult.
-
Performance Dependencies – If deployed incorrectly, ZTNA can introduce latency.
-
Cultural Shift – Teams must embrace a “verify everything” mindset.
Organizations can mitigate these challenges through phased implementation, cloud-based ZTNA solutions, and robust endpoint protection like Xcitium ZeroDwell Containment Technology.
ZTNA vs. SASE: Are They the Same?
ZTNA is often part of a larger framework called SASE (Secure Access Service Edge) — a cloud-delivered model that integrates networking and security.
| Aspect | ZTNA | SASE |
|---|---|---|
| Scope | Focused on secure access | Combines network and security in one framework |
| Components | Identity-based access control | Includes ZTNA, CASB, SWG, and SD-WAN |
| Deployment | Application-level | Network-wide |
| Purpose | Secure user-to-app connections | Secure user-to-app and site-to-site connections |
In short, ZTNA is the security foundation of SASE — providing access control, while SASE expands it with broader network security capabilities.
Best Practices for Implementing ZTNA
-
Assess Your Current Security Posture – Identify gaps in remote access and data protection.
-
Adopt Identity-First Security – Use MFA, SSO, and behavioral analytics.
-
Start Small, Then Scale – Deploy ZTNA for critical applications first before expanding organization-wide.
-
Integrate with Endpoint Security – Ensure all devices meet compliance and are continuously monitored.
-
Choose Cloud-Native ZTNA Solutions – For scalability and global accessibility.
-
Educate Employees and Stakeholders – Build a culture of zero trust across teams.
The Future of ZTNA
As cyber threats become more advanced and decentralized, ZTNA is evolving to include AI-driven adaptive policies, real-time analytics, and integration with XDR (Extended Detection and Response) systems.
Gartner predicts that by 2026, 70% of organizations will replace VPNs with ZTNA as the primary remote access solution.
Future-ready ZTNA will be autonomous, contextual, and predictive — adjusting security dynamically based on risk scores and environmental changes.
Conclusion
So, what is ZTNA?
It’s more than a buzzword — it’s a paradigm shift in cybersecurity.
By eliminating implicit trust and focusing on identity, device health, and continuous verification, Zero Trust Network Access ensures that every connection is secure, every user is verified, and every session is monitored.
For organizations embracing digital transformation, ZTNA isn’t optional — it’s essential for safeguarding the modern enterprise.
Take the Next Step Toward Zero Trust Security
Protect your business from evolving threats with next-generation endpoint and network security.
👉 Request a Demo from Xcitium and see how ZTNA can transform your organization’s defense strategy.
FAQs: What Is ZTNA?
1. What does ZTNA stand for?
ZTNA stands for Zero Trust Network Access, a security model that provides identity-based access control to applications and data.
2. How is ZTNA different from a VPN?
VPNs grant broad network access, while ZTNA limits access to specific applications based on user verification and device compliance.
3. Is ZTNA cloud-based?
Yes. Modern ZTNA solutions are cloud-native, offering flexibility and scalability across hybrid and multi-cloud environments.
4. Does ZTNA replace firewalls?
ZTNA doesn’t replace firewalls; it complements them by providing secure access control at the user and application levels.
5. Who should implement ZTNA?
Any organization with remote workers, cloud applications, or compliance requirements should implement ZTNA for secure access management.