What Is the Deep Web? A Clear Guide for Cybersecurity and Business Leaders
Updated on February 2, 2026, by Xcitium
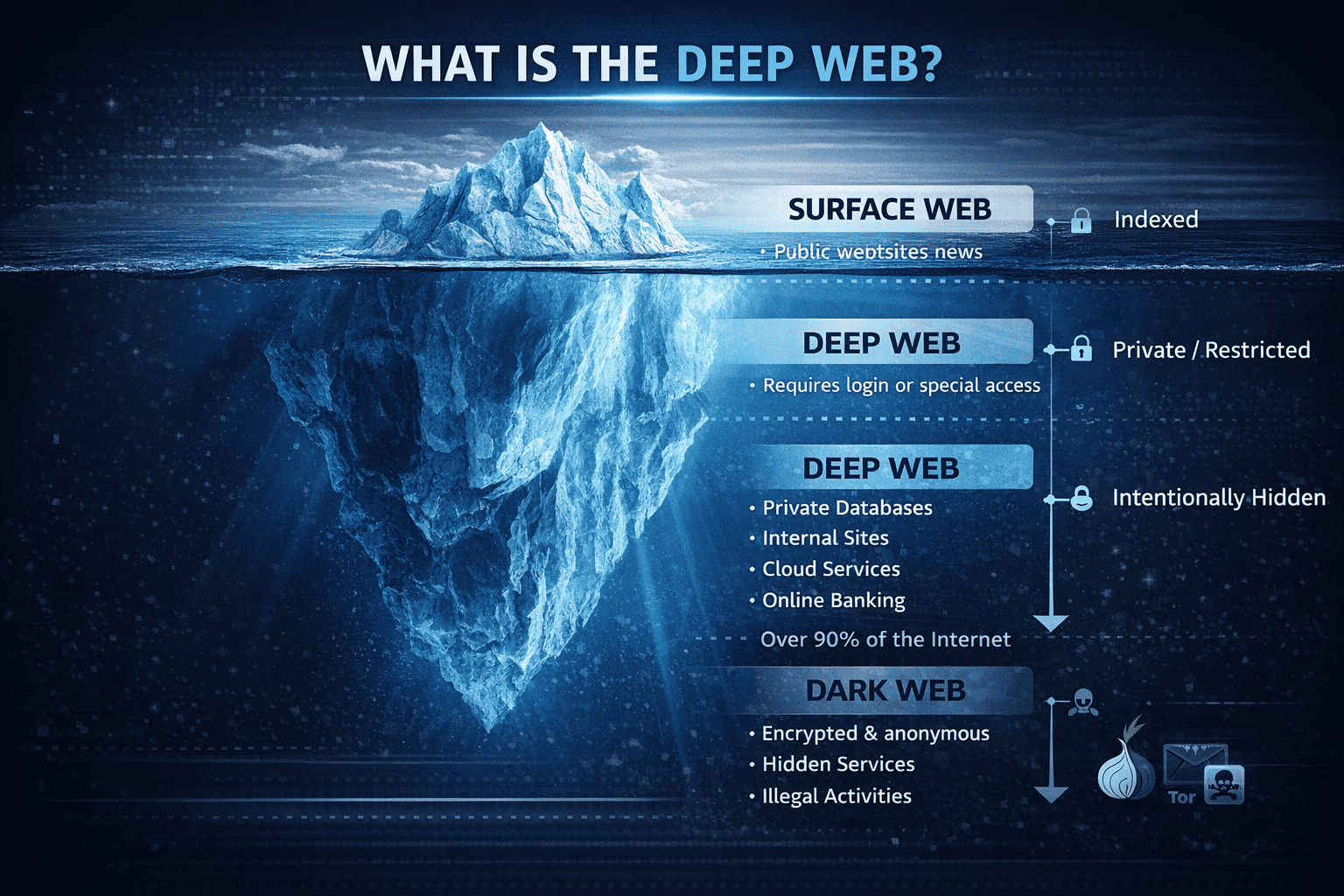
Have you ever searched for something online and wondered what exists beyond Google results? If so, you’ve already brushed up against a much larger part of the internet. To understand today’s digital risk landscape, it’s essential to answer one key question: what is the deep web?
The deep web makes up the vast majority of the internet, yet it’s often misunderstood—or confused with the dark web. For cybersecurity professionals, IT managers, and executives, understanding what the deep web is (and what it isn’t) is critical for data protection, compliance, and threat awareness.
In this guide, we’ll break down what is the deep web, how it works, how it differs from the dark web, and why it matters for modern organizations.
What Is the Deep Web? (Plain-English Definition)
The deep web refers to all parts of the internet that are not indexed by traditional search engines like Google or Bing. This content exists online but requires authentication, permissions, or specific access to view.
When people ask what is the deep web, the simplest answer is:
The deep web includes private, protected, or restricted online content that search engines cannot crawl.
Examples include:
-
Online banking portals
-
Corporate intranets
-
Email accounts
-
Cloud storage dashboards
-
Subscription-based platforms
In fact, most of the internet you use daily lives on the deep web.
How Big Is the Deep Web?
The surface web—the part indexed by search engines—accounts for only a small fraction of online content. Estimates suggest the deep web represents over 90% of the internet.
This scale explains why understanding what is the deep web is crucial for cybersecurity teams. Sensitive business data, customer records, and intellectual property often reside there.
Deep Web vs Surface Web vs Dark Web
One of the biggest sources of confusion around what is the deep web is its relationship to the dark web.
Key Differences Explained
| Web Layer | Description | Access |
|---|---|---|
| Surface Web | Public websites indexed by search engines | Open |
| Deep Web | Private or restricted content | Login or permissions |
| Dark Web | Intentionally hidden networks | Special software (Tor) |
The deep web is not illegal or malicious by default. Unlike the dark web, it exists primarily to protect privacy and security.
Why the Deep Web Exists
The deep web exists for legitimate and necessary reasons.
Core Purposes Include:
-
Protecting personal data
-
Securing business operations
-
Enforcing access controls
-
Supporting compliance requirements
-
Preventing unauthorized access
Without the deep web, sensitive systems would be exposed to massive risk.
Common Examples of the Deep Web
Understanding what is the deep web becomes clearer when you see everyday examples.
Personal Use
-
Email inboxes
-
Social media accounts
-
Online banking
-
Medical portals
Business and Enterprise Use
-
Internal dashboards
-
CRM and ERP systems
-
Cloud management consoles
-
Security monitoring tools
These systems are intentionally hidden from public indexing.
Why the Deep Web Matters for Cybersecurity
For security teams, the deep web is both a defensive asset and a potential attack surface.
Security Implications
-
Sensitive data exposure if access controls fail
-
Credential theft leading to deep web access
-
Insider threats exploiting private systems
-
Compliance risks if data is mismanaged
Understanding what is the deep web helps organizations prioritize identity management, access monitoring, and zero-trust security models.
Deep Web Risks Organizations Should Know
While the deep web itself is not dangerous, misconfigurations can create serious vulnerabilities.
Common Risks Include:
-
Weak authentication controls
-
Exposed admin portals
-
Stolen credentials reused across systems
-
Lack of monitoring for abnormal access
Attackers often target deep web systems because they contain high-value data.
Deep Web vs Dark Web: A Critical Security Distinction
Many executives hear “deep web” and assume criminal activity. This misunderstanding can lead to poor security decisions.
Key Clarification
-
Deep web = private but legitimate
-
Dark web = intentionally anonymous and often criminal
Security teams must monitor both, but strategies differ significantly.
How Attackers Exploit the Deep Web
Attackers don’t need dark web tools to cause damage. Often, they aim directly at deep web assets.
Common Attack Methods
-
Phishing to steal login credentials
-
Credential stuffing attacks
-
Exploiting exposed cloud interfaces
-
Abusing misconfigured APIs
Once inside, attackers can move laterally and escalate privileges.
How Organizations Can Secure the Deep Web
Protecting deep web assets requires layered defenses.
Best Practices
-
Enforce multi-factor authentication (MFA)
-
Implement role-based access control
-
Monitor login behavior continuously
-
Encrypt data at rest and in transit
-
Audit access logs regularly
These steps reduce the likelihood of unauthorized access.
Actionable Tips for IT Managers and Executives
-
Inventory all deep web systems
-
Identify who has access—and why
-
Remove unused or excessive privileges
-
Align deep web security with compliance standards
-
Integrate monitoring into SOC workflows
Understanding what is the deep web helps leadership allocate resources more effectively.
FAQ: The Deep Web Explained
1. What is the deep web used for?
The deep web is used to store and protect private information such as emails, financial data, and internal business systems.
2. Is the deep web illegal?
No. The deep web is legal and essential for privacy and security.
3. How is the deep web different from the dark web?
The deep web requires authentication, while the dark web uses anonymity tools like Tor.
4. Can hackers access the deep web?
Yes, if credentials are stolen or systems are misconfigured.
5. Do businesses need to monitor deep web activity?
Absolutely. Monitoring access and behavior helps prevent breaches.
Why Understanding the Deep Web Is a Business Advantage
Knowing what is the deep web empowers organizations to protect sensitive data, meet compliance requirements, and reduce cyber risk. For IT leaders and executives, it’s a foundation for informed security strategy—not a mystery to fear.
Organizations that secure their deep web assets are far better prepared to withstand modern cyber threats.
Strengthen Visibility and Control Over Your Digital Assets
Protecting deep web systems requires continuous monitoring, automation, and intelligent threat prevention.
👉 Request a demo today:
https://www.xcitium.com/request-demo/
Discover how advanced cybersecurity solutions help safeguard your organization’s most sensitive environments.