Ransomware Virus Definition
Updated on October 11, 2022, by Xcitium

But is ransomware a virus? While most people have repeatedly used the term virus to describe computer attacks, not all attacks are caused by viruses. Computer viruses are malware, and so is ransomware.
Does Ransomware Virus Exist?
In reality, there is no ransomware virus. This term is commonly used by people without a profound knowledge of ransomware to describe ransomware attacks. As mentioned, most people are quick to say my computer is being infected with a virus when anything goes wrong. While this may not be the right term to use, it directly tells what the person is talking about.
So, ransomware virus as most people want to call it directly points to the ransomware malware. Like other malware, Ransomware attacks your computer through infected software and other attachments. Usually, the person behind the ransomware embed the codes in safe files, and you do allow the virus into your system when you accept the infected files into your computer.
However, ransomware takes a different approach after entering your computer. Instead of causing a bug or corrupting your files as other malware does, it encrypts them, locks you out and demands a ransom. You can now see why this malware is regarded as ransomware. The primary intent is to get money from its victims fraudulently. The attackers won’t release your data until you pay a ransom.
Still, puzzled about what ransomware entails? Here it is—this malware affects your system through phishing—emails and other methods. Once it finds its way into your system, it takes over your sensitive data and denies you access. This is followed by an on-screen notification asking you to pay a certain amount of money before your computer and data are released to you.
Most victims of ransomware have to pay the money before recovering their data.
Is Ransomware A New Malware?
Before the introduction of ransomware, other malware such as worms, Trojans and viruses were already in existence. However, available facts say ransomware has been around since 1989 but didn’t attract public attention until the mid-2000s when the first lethal attack was launched. This attack targeted more of healthcare industries and carted away huge sums from victims.
From the analysis, it’s not entirely wrong to say ransomware is a new malware. Though it’s been there for long, the major attacks started in the mid-2000s.
Since, then more and more ransomware attacks have affected both individuals, businesses and government parastatals.
Why Is It Difficult To Fish Out Ransomware Criminals?
Virtually everyone that hears about a cyber-attack that involves a ransom may think the culprits can be traced through the payment. But this has never happened. Ransomware assailants have continued to carry out successful attacks without traces, making it more worrisome to everyone, especially business owners.
But why is it so? The method of payment is one that leaves no traces. Almost all ransomware attacks are paid via Bitcoin. As you may know, Bitcoin is a decentralized digital currency–not regulated by the government or any third party. More so, the system allows anonymous transactions, which doesn’t record the identity of the users. This makes it hard to know those behind ransomware attacks.
Who Is A Target Of Malware?
Anyone can become a target. Ransomware attackers focus more on data-driven companies. Individuals who are figureheads in such companies are also targets of ransomware. So, both businesses, government and individuals are targets of ransomware attacks.
What Is The Way Out?
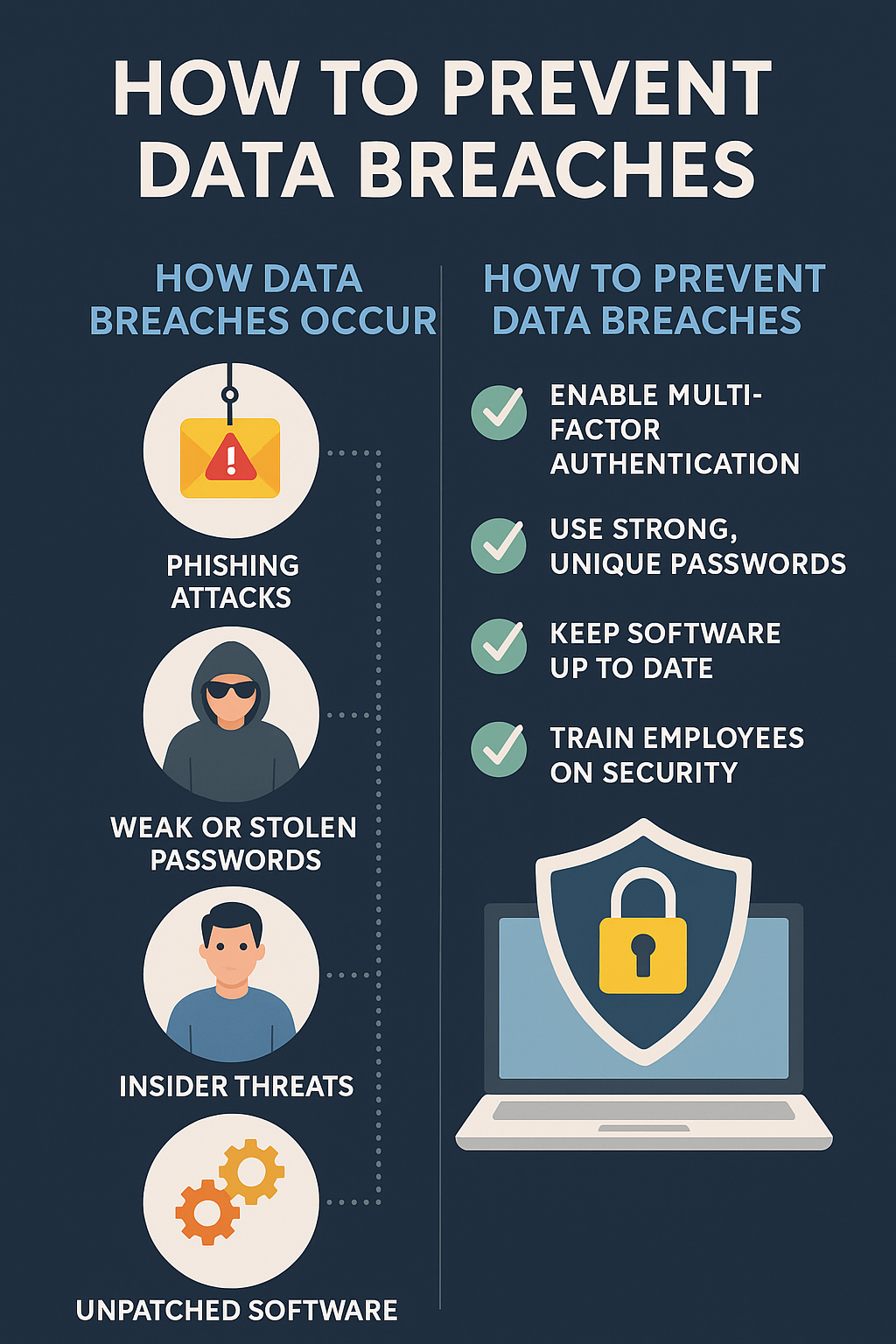
The only way out is to prevent ransomware attacks. Understanding how ransomware spreads can help you avoid its strikes.
As you may know, ransomware is spread through malicious codes, and these codes are hosted by software and attachments. You should be careful about opening any attachment sent to you via emails. Also, avoid downloading cracked software and do not use untrusted websites.
Social engineering is another method of spreading malware. Ensure you scrutinize any message that includes attachment before you open.
Other than the above, you want to ensure you keep to cybersecurity best practices:
- Update your operating system and all applications always
- Use strong passwords
- Do not use public Wi-Fi
- Get the best antivirus
- Use different passwords for different accounts
- Enable two-step authentication for your online accounts
- Ensure your staff are trained and retrained on cybersecurity ethics
More so, you need an advanced security system to stop difficult to block malware. Ransomware and other fileless malware are usually deceptive and may bypass antiviruses. Advanced Endpoint Protection (AEP) can help you defend against such malware as the system uses top security technology like AI, IoT, etc., to spot and block troublesome malware.