What Is Network Address Translation? A Complete Guide for Modern Networks
Updated on January 5, 2026, by Xcitium
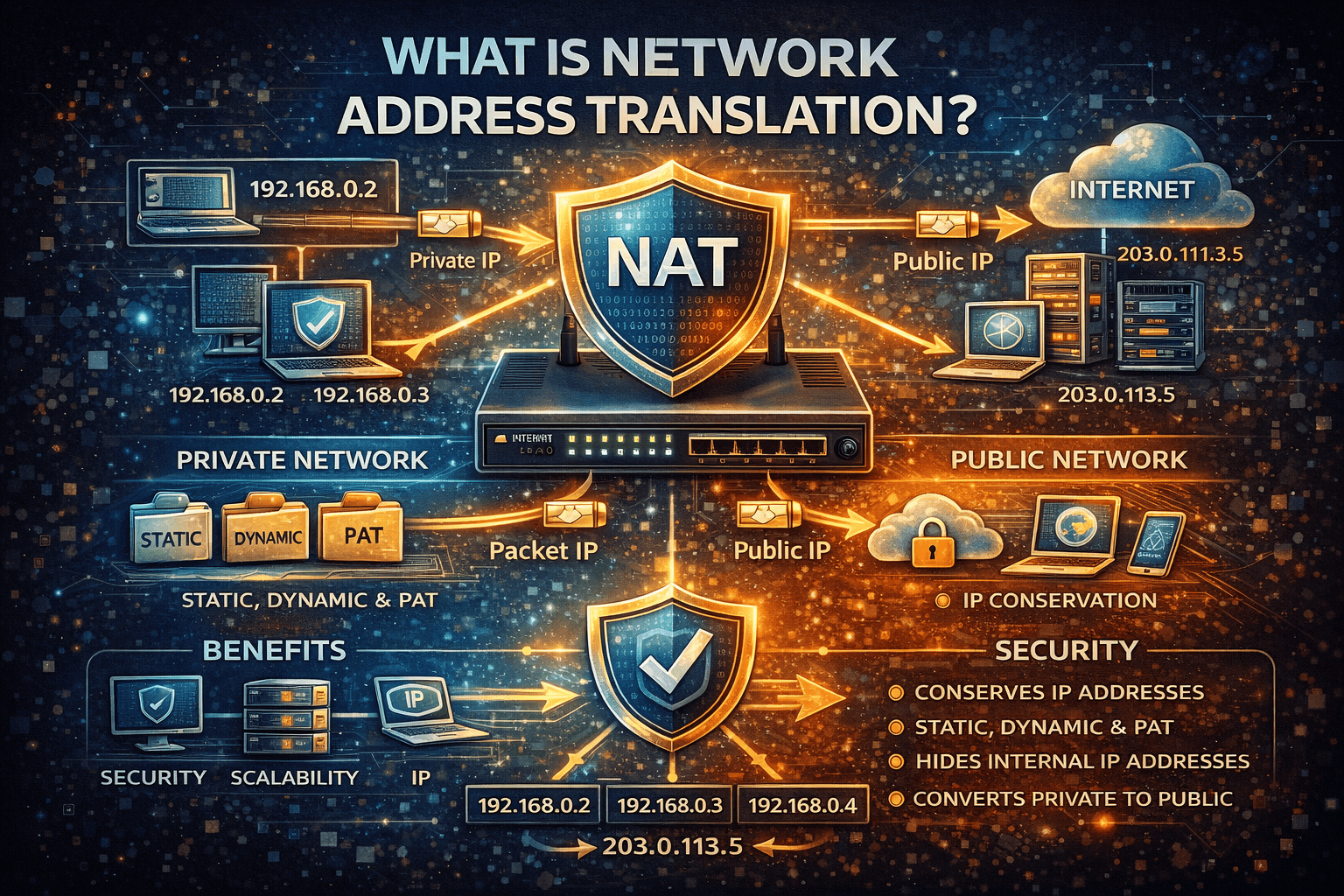
As organizations scale their networks, connect cloud services, and support remote users, IP address management becomes increasingly complex. This is where many IT and security professionals ask a foundational networking question: what is network address translation, and why is it so important?
Network Address Translation (NAT) plays a critical role in modern networking. It allows multiple devices to share limited IP address space while improving efficiency and adding a layer of security. In this guide, we’ll break down what is network address translation, how it works, its different types, real-world use cases, security implications, and best practices for enterprise environments.
What Is Network Address Translation?
Network address translation (NAT) is a networking technique that modifies IP address information in packet headers while traffic is in transit. It enables devices on a private network to communicate with external networks—such as the internet—using a different, typically public, IP address.
In simple terms, when you ask what is network address translation, the answer is:
A method that allows many internal devices to share one or more public IP addresses.
NAT is commonly implemented on routers, firewalls, and gateways, and it is fundamental to how modern networks operate.
Why Network Address Translation Is Necessary
The original design of the internet did not anticipate billions of connected devices. IPv4 address space is limited, which led to widespread IP address exhaustion.
Network address translation solves this problem by:
-
Conserving public IP addresses
-
Enabling private networks to access the internet
-
Simplifying internal IP management
-
Supporting network scalability
Without NAT, organizations would struggle to connect large networks using IPv4.
How Network Address Translation Works
To fully understand what is network address translation, it helps to look at how traffic flows.
Basic NAT Process
-
A device on a private network sends a request to the internet
-
The NAT device replaces the private IP with a public IP
-
The NAT device tracks the connection in a translation table
-
The response returns to the NAT device
-
The NAT device forwards the response to the correct internal device
This translation happens transparently and in real time.
Private vs Public IP Addresses
NAT works by separating private and public address spaces.
Private IP Ranges
-
10.0.0.0 – 10.255.255.255
-
172.16.0.0 – 172.31.255.255
-
192.168.0.0 – 192.168.255.255
These addresses are not routable on the public internet and rely on NAT for external communication.
Types of Network Address Translation
Understanding what is network address translation also means knowing its different types.
1. Static NAT
Static NAT maps one private IP address to one public IP address.
Key characteristics:
-
One-to-one mapping
-
Consistent external address
-
Common for servers and hosted services
Static NAT is predictable but consumes more public IP addresses.
2. Dynamic NAT
Dynamic NAT maps private IP addresses to a pool of public IP addresses.
Key characteristics:
-
One-to-many mapping (from a pool)
-
Temporary assignments
-
More efficient than static NAT
Once the pool is exhausted, new connections may fail.
3. Port Address Translation (PAT)
Also known as NAT overload, PAT is the most common form of NAT.
Key characteristics:
-
Many private IPs share one public IP
-
Uses port numbers to track sessions
-
Highly efficient
When most people ask what is network address translation, they’re usually referring to PAT.
Network Address Translation vs Proxy Servers
NAT is sometimes confused with proxies.
| Feature | NAT | Proxy |
|---|---|---|
| OSI Layer | Network layer | Application layer |
| Transparency | Transparent to users | Often visible |
| Security | Basic isolation | Advanced filtering |
| Performance | High | Moderate |
NAT handles addressing, while proxies handle content and application traffic.
Benefits of Network Address Translation
NAT offers several advantages beyond address conservation.
Key Benefits
-
Reduces public IP usage
-
Simplifies internal network design
-
Enables private addressing
-
Adds a basic security layer
-
Supports large-scale connectivity
For enterprises, NAT is both a technical and economic necessity.
Network Address Translation and Security
From a cybersecurity perspective, understanding what is network address translation is essential.
Security Advantages
-
Hides internal IP addresses
-
Reduces direct exposure to the internet
-
Blocks unsolicited inbound traffic by default
While NAT is not a firewall, it does provide basic network isolation.
Limitations of Network Address Translation
Despite its benefits, NAT has limitations.
Common Challenges
-
Breaks end-to-end connectivity
-
Complicates peer-to-peer applications
-
Requires special handling for VoIP and VPNs
-
Adds troubleshooting complexity
These challenges must be considered during network design.
NAT and Modern Applications
Some applications struggle with NAT.
Examples
-
Voice over IP (VoIP)
-
Video conferencing
-
Online gaming
-
Remote desktop connections
Technologies like NAT traversal, STUN, TURN, and ICE help overcome these limitations.
Network Address Translation in Enterprise Networks
In enterprise environments, NAT is everywhere.
Common Use Cases
-
Internet gateways
-
Branch office connectivity
-
Cloud networking
-
Remote access solutions
-
Data center perimeter security
NAT helps enterprises scale securely while managing limited address space.
NAT in Cloud and Hybrid Environments
Cloud computing heavily relies on NAT.
Cloud NAT Use Cases
-
Outbound internet access for private instances
-
Multi-tenant isolation
-
Hybrid connectivity
-
Secure cloud-to-internet traffic
Understanding what is network address translation is critical for cloud architects and security teams.
NAT and Firewalls: How They Work Together
NAT is often deployed alongside firewalls.
Key Differences
-
NAT modifies addresses
-
Firewalls enforce security policies
Together, they:
-
Control traffic flow
-
Limit attack surfaces
-
Enforce segmentation
Modern firewalls often integrate NAT directly into security policies.
Network Address Translation vs IPv6
IPv6 was designed to eliminate the need for NAT.
IPv6 Advantages
-
Vast address space
-
End-to-end connectivity
-
Simplified routing
However, IPv4 and NAT remain dominant due to:
-
Legacy systems
-
Compatibility requirements
-
Gradual IPv6 adoption
NAT will continue to exist for the foreseeable future.
Common NAT Misconceptions
Myth 1: NAT Is a Firewall
False. NAT does not inspect traffic content.
Myth 2: NAT Provides Full Security
False. It only offers basic isolation.
Myth 3: NAT Is Obsolete
False. NAT remains essential in IPv4 networks.
Clearing these misconceptions helps teams design better security architectures.
Best Practices for Using Network Address Translation
To maximize reliability and security, follow these best practices.
NAT Best Practices
-
Document NAT mappings clearly
-
Limit static NAT exposure
-
Monitor translation tables
-
Combine NAT with firewall rules
-
Regularly audit configurations
Proper management prevents outages and security gaps.
Troubleshooting NAT Issues
NAT problems can be difficult to diagnose.
Common Symptoms
-
One-way traffic
-
Failed inbound connections
-
Application timeouts
-
VPN connection failures
Packet captures, logs, and translation tables are essential troubleshooting tools.
Network Address Translation and Zero Trust
Zero Trust architectures assume no network is inherently trusted.
NAT supports Zero Trust by:
-
Reducing network visibility
-
Limiting direct access paths
-
Enforcing controlled entry points
However, NAT must be combined with identity-based controls for full Zero Trust security.
Performance Impact of Network Address Translation
NAT introduces minimal latency but can impact performance at scale.
Performance Considerations
-
Translation table size
-
CPU utilization
-
Session timeouts
-
Hardware acceleration
Enterprise-grade devices are designed to handle NAT efficiently.
The Future of Network Address Translation
While IPv6 adoption grows, NAT is not disappearing anytime soon.
Future Trends
-
Continued IPv4 coexistence
-
Cloud-managed NAT services
-
Integration with security analytics
-
Automation and orchestration
Understanding what is network address translation will remain relevant for years to come.
Frequently Asked Questions (FAQs)
1. What is network address translation used for?
Network address translation allows private networks to access public networks using shared IP addresses.
2. Is NAT secure?
NAT provides basic isolation but should not replace a firewall.
3. What is the most common type of NAT?
Port Address Translation (PAT) is the most widely used form.
4. Does IPv6 eliminate the need for NAT?
In theory yes, but NAT is still widely used due to IPv4 dominance.
5. Can NAT cause connectivity issues?
Yes. Some applications require NAT traversal techniques to function correctly.
Final Thoughts: Why Understanding What Is Network Address Translation Matters
Network Address Translation is one of the most important—and often overlooked—components of modern networking. Understanding what is network address translation helps organizations build scalable networks, manage IP resources efficiently, and reduce exposure to external threats.
For IT managers, cybersecurity teams, and executives, NAT knowledge supports better network design, stronger security posture, and smoother digital operations.
Secure Network Traffic Beyond NAT
NAT helps manage addresses—but modern threats require deeper visibility and control. To gain real-time threat detection, zero-trust enforcement, and advanced network security:
👉 See how Xcitium protects enterprise networks
Request a Demo