What Is a Data Breach? Understanding, Preventing, and Responding to Cyber Threats
Updated on October 27, 2025, by Xcitium
Did you know that over 6.4 million data records are stolen or exposed every day worldwide? Whether it’s customer details, financial data, or trade secrets, every organization today faces the risk of a data breach.
If you’ve ever asked yourself, “What is a data breach, and how can my company prevent one?”, this guide has you covered. We’ll explain how data breaches happen, what causes them, their devastating impact, and—most importantly—how businesses can protect themselves using robust cybersecurity solutions.
What Is a Data Breach?
A data breach is an incident where unauthorized individuals gain access to confidential, sensitive, or protected information. This can happen accidentally or through deliberate cyberattacks.
These breaches often involve data like:
-
Personally identifiable information (PII) — names, addresses, Social Security numbers.
-
Financial data — credit card details or banking credentials.
-
Corporate information — trade secrets, passwords, or intellectual property.
Simply put, a data breach means information that should be private is now exposed—either to the public or malicious actors.
Common Data Breach Scenarios:
-
Hackers infiltrate company servers to steal customer data.
-
An employee accidentally sends confidential files to the wrong recipient.
-
A stolen laptop or smartphone contains unencrypted data.
How Data Breaches Happen: Common Causes
Understanding how data breaches occur helps IT managers and cybersecurity leaders create effective defenses. Here are the leading causes:
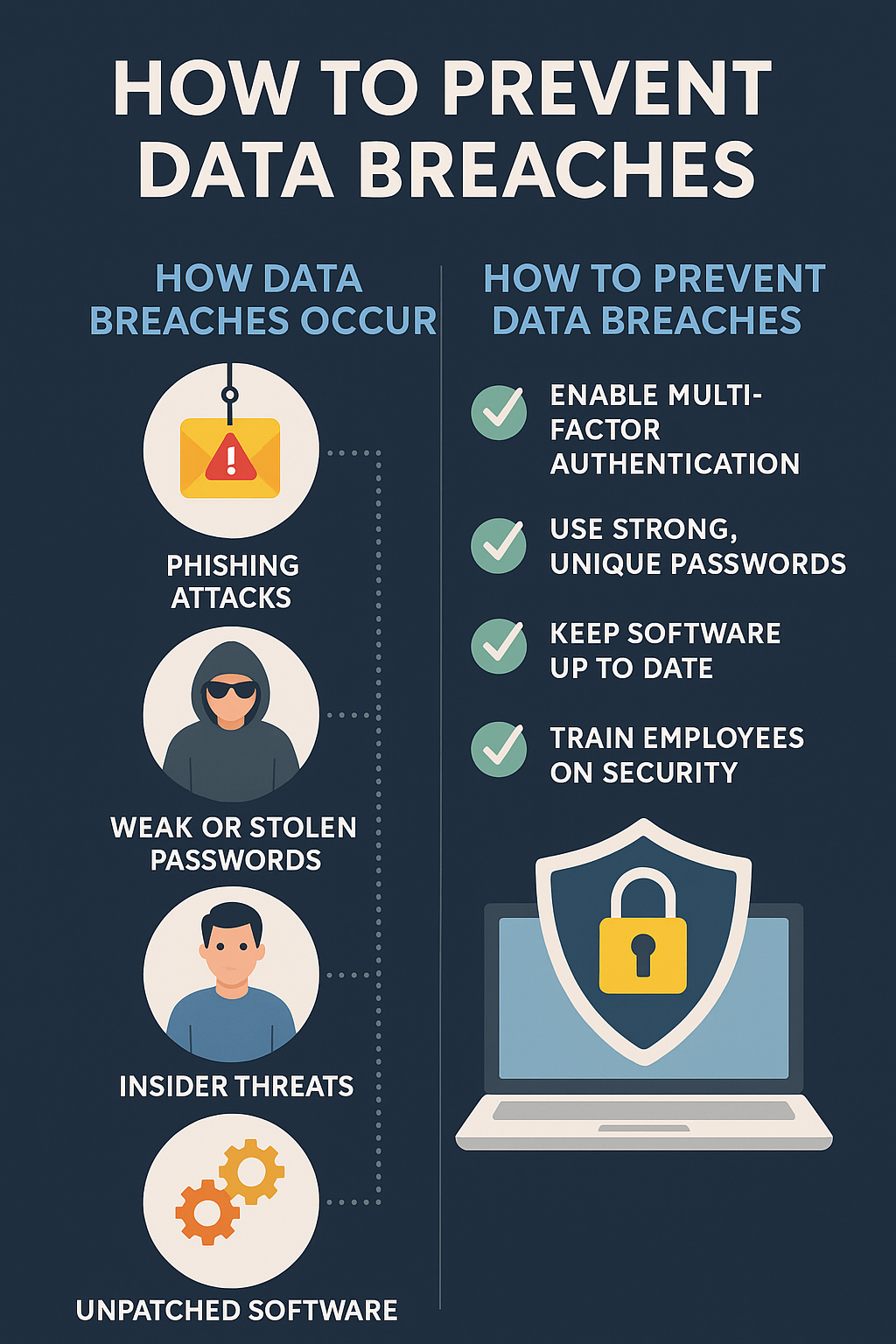
1. Phishing Attacks
Cybercriminals use fraudulent emails or messages to trick employees into revealing credentials or clicking malicious links.
2. Weak or Stolen Passwords
Using simple or reused passwords is a major security gap. Once compromised, hackers can gain entry to multiple systems.
3. Insider Threats
Not all breaches come from outside—disgruntled employees or careless insiders can expose sensitive data, intentionally or accidentally.
4. Unpatched Software and Systems
Outdated applications and operating systems can contain vulnerabilities that hackers exploit.
5. Malware and Ransomware
Malware can infect systems, giving attackers access to data or encrypting it for ransom.
6. Third-Party Vulnerabilities
Suppliers, contractors, or external service providers with access to your systems can become weak links.
Types of Data Breaches
Data breaches can vary depending on their scope and method.
1. Accidental Data Breaches
Human error causes data to be exposed unintentionally—such as emailing confidential files or misconfiguring a cloud database.
2. Malicious Data Breaches
These are deliberate attacks aimed at stealing valuable data, often for profit or espionage.
3. Physical Data Breaches
Theft of physical media like USB drives, laptops, or printed documents containing sensitive data.
4. Ransomware-Induced Breaches
When attackers encrypt an organization’s files and demand ransom, data exposure is often a side effect.
Real-World Examples of Data Breaches
To understand the gravity of the problem, let’s look at some well-known data breaches that shook industries:
-
Equifax (2017): 147 million customers’ personal data was compromised due to an unpatched vulnerability.
-
Yahoo (2013–2014): Over 3 billion accounts were exposed, making it one of the largest breaches ever.
-
LinkedIn (2021): Information from 700 million users was scraped and leaked online.
-
Target (2013): Attackers accessed 40 million credit card details via a third-party HVAC vendor.
Each of these breaches led to massive financial losses, regulatory fines, and irreparable brand damage.
The Cost and Consequences of a Data Breach
A data breach can devastate a business. According to IBM’s Cost of a Data Breach Report (2024), the average global cost per breach is $4.45 million, an all-time high.
Key impacts include:
-
Financial Loss: Direct theft, ransom payments, and regulatory penalties.
-
Reputational Damage: Loss of customer trust and brand credibility.
-
Operational Disruption: Downtime caused by containment, investigation, and recovery.
-
Legal Consequences: Violations of GDPR, HIPAA, or CCPA can result in hefty fines.
-
Customer Churn: Data breaches often drive customers toward competitors.
Data Breach Prevention: Best Practices for Cybersecurity
Preventing a data breach requires a layered, proactive approach. Below are actionable steps:
1. Implement Strong Access Controls
-
Use multi-factor authentication (MFA) for all user accounts.
-
Follow the principle of least privilege (PoLP)—only give users the access they truly need.
2. Regular Software Updates and Patch Management
Keep all systems, applications, and firmware up-to-date to eliminate vulnerabilities.
3. Employee Security Training
Humans are the weakest link in cybersecurity. Conduct regular training to help staff spot phishing and handle data securely.
4. Encrypt Sensitive Data
Encryption ensures that even if data is stolen, it remains unreadable.
5. Deploy Endpoint Detection and Response (EDR)
Advanced EDR tools—like Xcitium’s —provide real-time threat monitoring, anomaly detection, and automatic incident response.
6. Network Security Measures
Use firewalls, intrusion detection systems (IDS), and secure network segmentation to limit attack impact.
7. Data Backup and Recovery Plans
Maintain secure, encrypted backups and regularly test recovery procedures to minimize downtime after incidents.
Detecting a Data Breach
Early detection minimizes damage. Watch for signs such as:
-
Unexpected system slowdowns or crashes.
-
Unauthorized logins or strange access patterns.
-
Sudden spikes in outbound traffic.
-
Alerts from intrusion detection systems.
Investing in Security Information and Event Management (SIEM) tools can automate detection and provide real-time insights into network behavior.
Responding to a Data Breach
Even with strong security, breaches can still occur. Having a Data Breach Response Plan is crucial.
Steps to Take Immediately:
-
Contain the Breach: Disconnect compromised systems to stop further data loss.
-
Assess the Damage: Identify what data was affected and how the breach occurred.
-
Notify Authorities and Affected Parties: Comply with regulations like GDPR that mandate disclosure.
-
Eradicate the Threat: Remove malware, reset credentials, and patch vulnerabilities.
-
Recover and Review: Restore systems from backups and strengthen security controls.
Legal and Regulatory Implications
Data privacy regulations such as GDPR (Europe), CCPA (California), and HIPAA (Healthcare) have strict rules for data protection.
Failing to comply can result in:
-
Fines up to €20 million or 4% of annual global revenue (under GDPR).
-
Mandatory reporting obligations.
-
Potential lawsuits from affected individuals.
Businesses must implement data governance frameworks that define how data is collected, stored, accessed, and destroyed.
Emerging Trends in Data Breach Prevention
The cybersecurity landscape evolves constantly. Here are key trends shaping the future of data protection:
-
Zero Trust Architecture: “Never trust, always verify” is the new security model for networks and users.
-
AI and Machine Learning: Modern EDR and SIEM systems use AI to predict and stop breaches before they happen.
-
Cloud Security Enhancements: Cloud providers are investing in encryption, tokenization, and advanced access controls.
-
Privacy by Design: Businesses are integrating data protection principles into product development and operations.
Conclusion: Staying Ahead of Data Breaches
Data breaches are no longer a question of if—but when. Every organization, large or small, must prepare to prevent, detect, and respond effectively.
Investing in modern cybersecurity tools, employee training, and continuous monitoring ensures your business remains resilient.
💡 Pro Tip: Combine strong data governance with advanced endpoint protection, like Xcitium, to gain 360° visibility and defense against breaches.
FAQs About Data Breaches
1. What is the main cause of data breaches?
Human error and phishing attacks are leading causes, followed by poor password management and unpatched vulnerabilities.
2. What’s the difference between a data breach and a data leak?
A breach involves unauthorized intrusion, while a leak is often accidental exposure of data without malicious intent.
3. How long does it take to detect a data breach?
On average, companies take over 200 days to detect a breach—highlighting the need for advanced monitoring tools.
4. What should I do if my company experiences a breach?
Immediately contain the threat, assess affected systems, notify regulators, and enhance your security policies.
5. Can small businesses experience data breaches?
Absolutely. In fact, 43% of cyberattacks target small and medium-sized businesses, as they often lack strong defenses.