Incident Response Services: How Xcitium Helps Organizations Contain, Investigate, and Recover from Cyber Attacks
Updated on February 4, 2026, by Xcitium
Cyberattacks are no longer a question of if, but when. From ransomware and phishing campaigns to zero-day exploits and advanced persistent threats (APTs), organizations across every industry face escalating cyber risk. When an incident occurs, speed, expertise, and precision determine whether the situation is quickly contained or spirals into severe financial, operational, and reputational damage.
This is where Xcitium’s Incident Response (IR) Services play a critical role—helping organizations regain control during a cyber crisis and recover with confidence.
What Are Incident Response Services?
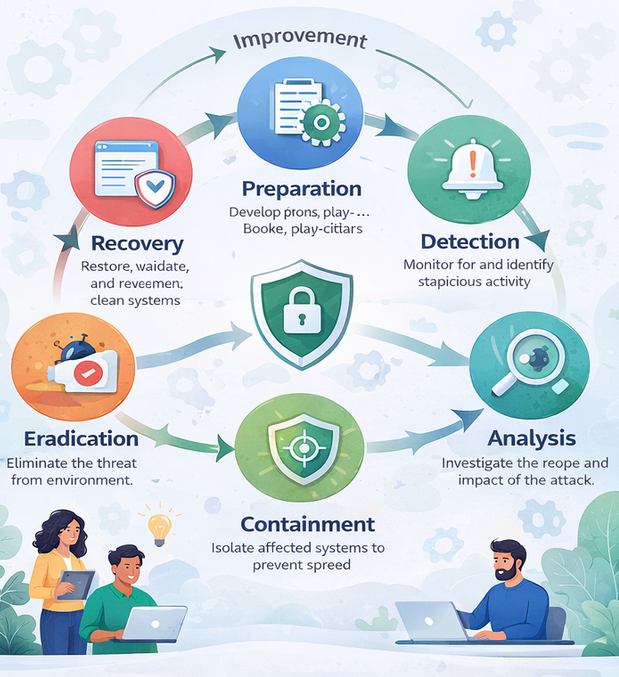
Incident Response (IR) services are specialized cybersecurity capabilities designed to help organizations detect, analyze, contain, eradicate, and recover from security incidents. A structured incident response approach minimizes downtime, limits data loss, and supports regulatory and legal compliance.
Xcitium delivers expert-led incident response services that combine advanced threat intelligence, real-time forensic investigation, and proven remediation strategies. This coordinated approach enables organizations to respond decisively, restore operations safely, and reduce the risk of future attacks.
Why Incident Response Is Critical in Today’s Threat Landscape
Modern cyberattacks are more dangerous than ever. Attackers now rely on highly sophisticated techniques such as fileless malware, living-off-the-land attacks, and zero-day vulnerabilities. These attacks move fast, often compromising systems within minutes, and the financial impact of breaches continues to rise year after year.
Without a professional incident response team, organizations face prolonged system outages, regulatory penalties, legal exposure, loss of sensitive data, and long-term damage to customer trust. Even worse, incomplete remediation can leave environments vulnerable to repeat attacks.

Xcitium’s Incident Response Services are designed to stop active threats, uncover the root cause, and prevent attackers from returning.
Xcitium Incident Response Services: Key Capabilities
Rapid Incident Containment
During a cyber incident, time is the most critical factor. Xcitium’s security experts act immediately to isolate affected systems, stop lateral movement, and prevent further data exfiltration. Malware and ransomware outbreaks are contained quickly to limit operational disruption and reduce overall business impact.
This rapid containment approach helps organizations stabilize their environment while deeper investigation and remediation take place.
Advanced Digital Forensics and Investigation
Understanding how an attack occurred is essential for a full and lasting recovery. Xcitium conducts comprehensive digital forensic investigations to identify the attack vector, determine the scope and impact, analyze malicious artifacts, and reconstruct attacker activity timelines.
These forensic insights support regulatory reporting, cyber insurance claims, and legal requirements while providing organizations with a clear picture of what happened and why.
Malware Analysis and Threat Intelligence
Xcitium leverages advanced malware analysis and threat intelligence to identify both known and unknown threats. This includes the analysis of zero-day exploits and custom malware, correlation of indicators of compromise (IOCs), and tracking attacker tactics, techniques, and procedures (TTPs).
By understanding the adversary’s behavior, Xcitium enables faster, more accurate containment and remediation decisions.
Complete Eradication and Remediation
Stopping an attack is only the first step. Xcitium ensures that malicious files, backdoors, and persistence mechanisms are fully removed from the environment. Vulnerabilities are identified and patched, misconfigurations are corrected, and security controls are strengthened.
This thorough eradication process prevents attackers from re-entering the environment and reduces the likelihood of repeat incidents.

Recovery and Business Continuity Support
Xcitium helps organizations safely restore normal operations by validating system integrity and supporting secure system recovery. Downtime is minimized, and systems are only reconnected once clean environments are confirmed.
The focus is on rapid recovery without reintroducing risk, ensuring business continuity while maintaining security.
Post-Incident Reporting and Strategic Recommendations
After the incident is resolved, Xcitium provides detailed post-incident reporting, including executive-level summaries and compliance-ready documentation. Organizations also receive actionable recommendations to improve their overall security posture.
These insights help strengthen defenses, close security gaps, and improve future incident readiness.
Proactive Incident Readiness with Xcitium
Incident response doesn’t start when an attack happens—it starts with preparation. Xcitium helps organizations improve readiness by developing incident response playbooks, conducting tabletop exercises, and enhancing detection and response maturity.
Response strategies are aligned with regulatory frameworks and industry best practices, helping organizations recover faster and suffer less damage when incidents occur.
Why Choose Xcitium for Incident Response?
Organizations trust Xcitium for incident response because of its 24/7 expert-led response capabilities, deep threat research and intelligence, and proven containment and remediation methodologies. Xcitium’s incident response services integrate seamlessly with its Zero Trust and SOC offerings, delivering comprehensive protection across the attack lifecycle.
Most importantly, Xcitium focuses on prevention—not just cleanup—helping organizations break the cycle of repeated attacks.
When Should You Engage Incident Response Services?
Organizations should engage Xcitium immediately if they experience ransomware or extortion attacks, suspected data breaches, malware outbreaks, unauthorized access, privilege escalation, compromised endpoints or servers, or regulatory and compliance-driven incident investigations.
Early engagement significantly reduces damage, recovery time, and long-term impact.
Strengthen Your Cyber Resilience with Xcitium Incident Response
Cyber incidents demand decisive action and trusted expertise. Xcitium’s Incident Response Services provide the speed, visibility, and control organizations need to contain attacks, recover safely, and emerge stronger.
By combining rapid response, deep investigation, and long-term prevention, Xcitium helps organizations stay resilient against today’s most advanced cyber threats.