What Are Proxies? A Complete Guide for Cybersecurity and Business Leaders
Updated on December 24, 2025, by Xcitium
Have you ever wondered what happens behind the scenes when you browse the internet securely?
In a world filled with cyber threats, data tracking, and privacy concerns, understanding what are proxies is no longer optional—it’s essential.
From shielding corporate networks to enabling secure web access, proxies play a critical role in modern cybersecurity strategies. Whether you’re an IT manager, security professional, or CEO making technology decisions, this guide will help you understand proxies clearly, practically, and confidently.
What Are Proxies? (Simple Definition)
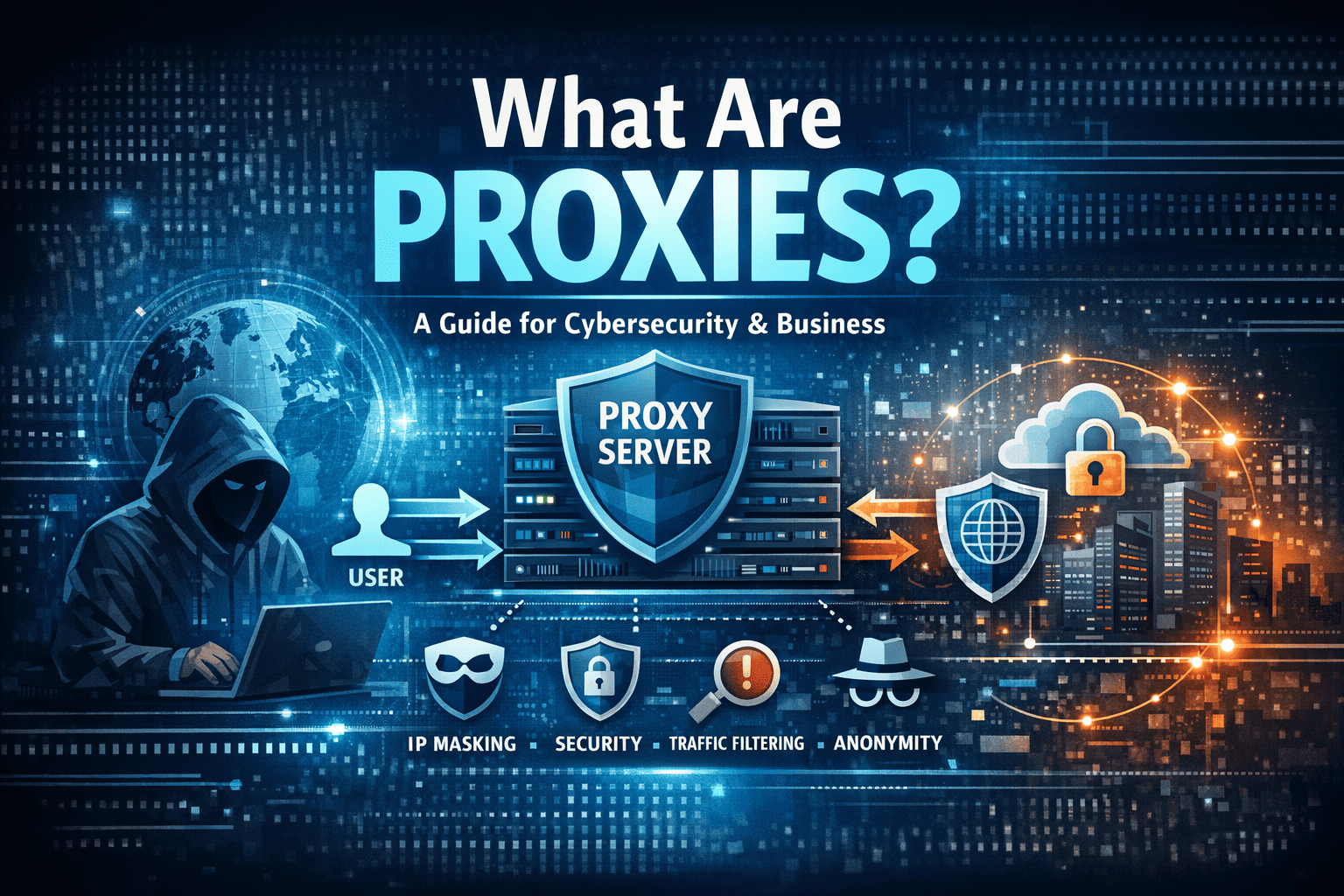
At its core, a proxy is an intermediary server that sits between a user and the internet.
Instead of connecting directly to a website, your request first goes through a proxy server, which then communicates with the destination site on your behalf. The website sees the proxy’s IP address—not yours.
In simple terms, proxies act as a protective middle layer that controls, filters, or secures internet traffic.
What are proxies used for?
-
Hiding IP addresses
-
Improving security
-
Enforcing access controls
-
Monitoring traffic
-
Bypassing restrictions
-
Enhancing performance
How Do Proxy Servers Work?
Understanding what are proxies becomes easier when you see how they operate step by step:
-
A user requests access to a website or service.
-
The request is sent to a proxy server instead of directly to the site.
-
The proxy evaluates the request (security rules, filters, permissions).
-
The proxy forwards the request to the destination server.
-
The response returns to the proxy.
-
The proxy sends the response back to the user.
This process allows organizations to inspect, log, block, cache, or anonymize traffic in real time.
Why Are Proxies Important for Cybersecurity?
In today’s threat landscape, knowing what are proxies is critical for building a secure digital perimeter.
Key Security Benefits of Proxies
-
IP address masking reduces exposure to targeted attacks
-
Traffic inspection blocks malicious content
-
Access control prevents unauthorized usage
-
Data loss prevention protects sensitive information
-
Attack mitigation helps stop DDoS and intrusion attempts
Proxies often serve as the first line of defense before traffic reaches internal networks.
Types of Proxies You Should Know
Not all proxies are created equal. Let’s break down the most common types used in enterprise environments.
1. Forward Proxy
A forward proxy handles requests from internal users going out to the internet.
Use cases:
-
Employee internet access control
-
Content filtering
-
Activity logging
This is one of the most common answers to what are proxies used for in businesses.
2. Reverse Proxy
A reverse proxy sits in front of servers and handles incoming requests from users.
Benefits include:
-
Load balancing
-
DDoS protection
-
Hiding backend infrastructure
Reverse proxies are critical for web application security and performance.
3. Transparent Proxy
A transparent proxy intercepts traffic without user configuration.
Common uses:
-
Network monitoring
-
Policy enforcement
-
Compliance auditing
Users may not even know the proxy exists.
4. Anonymous and Elite Proxies
These proxies focus on privacy and anonymity.
-
Anonymous proxies hide the user’s IP
-
Elite proxies hide both IP and proxy usage
They’re often discussed when people ask what are proxies for online privacy.
5. Residential vs. Datacenter Proxies
-
Residential proxies use real ISP IPs (harder to detect)
-
Datacenter proxies use cloud IPs (faster, cheaper)
Each has different security and compliance implications.
What Are Proxies Used for in Business Environments?
For enterprises, proxies are not just tools—they are strategic assets.
Common Enterprise Use Cases
-
Secure remote work access
-
Web traffic monitoring
-
Threat prevention
-
Policy enforcement
-
Regulatory compliance
-
Cloud security integration
For IT managers and CISOs, understanding what are proxies helps align security with operational goals.
Proxies vs VPNs: What’s the Difference?
This is one of the most searched questions related to what are proxies.
| Feature | Proxy | VPN |
|---|---|---|
| Encrypts traffic | ❌ Usually No | ✅ Yes |
| Hides IP address | ✅ Yes | ✅ Yes |
| Network-wide protection | ❌ No | ✅ Yes |
| Speed | Faster | Slightly slower |
| Use case | Traffic control | Full privacy |
Key takeaway:
Proxies manage traffic. VPNs secure tunnels. Many enterprises use both together.
Are Proxies Safe?
When properly configured, proxies are extremely safe. However, risks arise when:
-
Using free or unknown proxy services
-
Skipping encryption layers
-
Failing to monitor logs
-
Misconfiguring access controls
For businesses, unmanaged proxies can introduce blind spots. That’s why modern organizations integrate proxies with endpoint protection and zero trust models.
How Proxies Support Zero Trust Security
Zero Trust assumes no user or device is automatically trusted.
Proxies support this by:
-
Authenticating every request
-
Inspecting traffic continuously
-
Enforcing least-privilege access
-
Blocking unknown or risky destinations
Understanding what are proxies is foundational to Zero Trust adoption.
Key Considerations When Choosing a Proxy Solution
Before implementing a proxy, decision-makers should evaluate:
-
Scalability and performance
-
Security inspection capabilities
-
Integration with endpoint protection
-
Visibility and logging
-
Compliance support (HIPAA, GDPR, SOC 2)
For CEOs and founders, proxies are not just IT tools—they are risk management investments.
Best Practices for Using Proxies Securely
To maximize value and safety:
-
Combine proxies with endpoint security
-
Enable SSL/TLS inspection where allowed
-
Monitor logs continuously
-
Apply least-privilege policies
-
Regularly update configurations
This ensures your proxy setup enhances security rather than complicating it.
Frequently Asked Questions (FAQs)
1. What are proxies in simple terms?
Proxies are servers that act as intermediaries between users and the internet, helping control, secure, and manage web traffic.
2. What are proxies used for in cybersecurity?
They are used to filter traffic, block threats, hide IP addresses, monitor activity, and protect internal networks.
3. Are proxies legal to use?
Yes. Proxies are legal when used for legitimate purposes such as security, privacy, and compliance.
4. What are proxies vs firewalls?
Firewalls block or allow traffic based on rules. Proxies inspect and manage traffic at the application level.
5. Do enterprises still need proxies today?
Absolutely. Proxies remain critical for zero trust, cloud security, and advanced threat prevention.
Final Thoughts: Why Proxies Still Matter
In an era of ransomware, phishing, and zero-day attacks, knowing what are proxies gives organizations a security advantage.
Proxies are no longer just networking tools—they are strategic cybersecurity controls that protect users, data, and infrastructure.
If you’re evaluating how to strengthen your organization’s security posture, it’s time to move beyond basic defenses.
Ready to See Enterprise-Grade Protection in Action?
Discover how advanced security platforms integrate proxy-level controls with real-time endpoint protection.
👉 Request a personalized demo today:
https://www.xcitium.com/request-demo/