What Is Skybox? A Complete Guide for Cybersecurity Leaders
Updated on February 12, 2026, by Xcitium
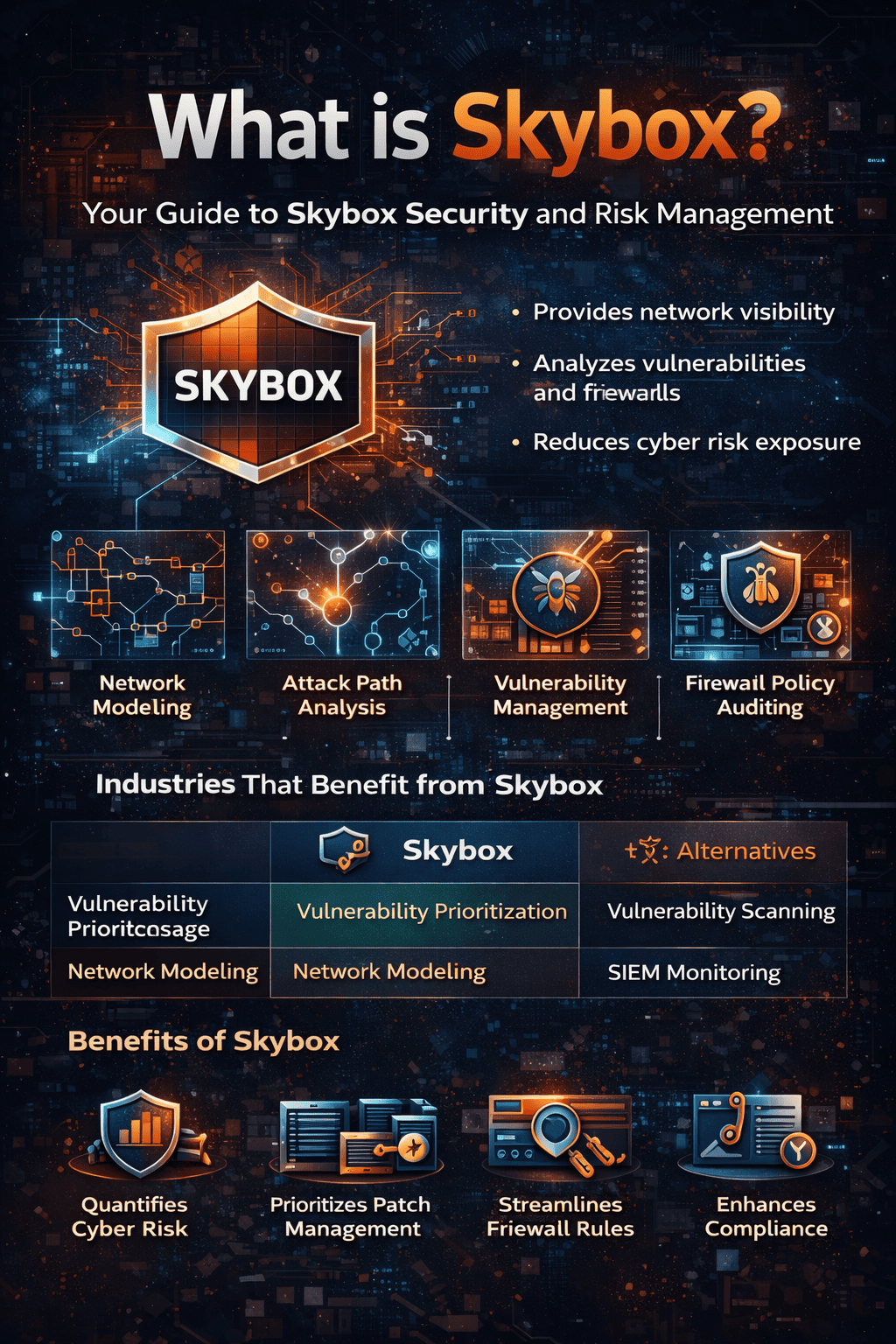
What is Skybox, and why are security teams and IT leaders talking about it? In today’s threat landscape, organizations face thousands of vulnerabilities, complex firewall rules, and expanding hybrid networks. Managing this risk manually is nearly impossible. That’s where solutions like Skybox come into the picture.
So, what is Skybox in cybersecurity terms? Skybox is a cybersecurity platform designed to provide network visibility, vulnerability management, and risk analysis. It helps organizations understand their attack surface, prioritize threats, and improve network security posture.
For IT managers, cybersecurity professionals, and CEOs, understanding what is Skybox is essential when evaluating risk management tools and security operations strategy.
What Is Skybox in Cybersecurity?
At its core, what is Skybox? Skybox (commonly known as Skybox Security) is a security management platform that focuses on:
-
Vulnerability management
-
Network security policy management
-
Threat exposure analysis
-
Attack path modeling
Unlike traditional security tools that operate in silos, Skybox aggregates data from firewalls, scanners, and other systems to create a unified risk view.
Key Capabilities of Skybox Security
When organizations ask what is Skybox used for, the answer typically includes:
-
Identifying network vulnerabilities
-
Prioritizing patch management
-
Visualizing attack paths
-
Auditing firewall rules
-
Supporting compliance reporting
It provides a map of your entire network infrastructure, highlighting weaknesses attackers could exploit.
How Skybox Works
To fully answer what is Skybox, you need to understand how it operates behind the scenes.
Skybox collects and analyzes data from:
-
Firewalls
-
Routers and switches
-
Vulnerability scanners
-
Cloud environments
-
Endpoint systems
It then builds a network model to simulate potential attack scenarios.
Attack Path Analysis
One of Skybox’s most powerful features is attack path analysis. Instead of listing vulnerabilities, it shows how an attacker could move through your network.
This helps security teams:
-
Identify high-risk pathways
-
Prioritize remediation
-
Reduce lateral movement risks
Understanding what is Skybox includes recognizing its ability to connect technical vulnerabilities with real-world risk.
Why IT Managers Use Skybox
Security teams often struggle with overwhelming vulnerability reports. Thousands of alerts do not automatically translate into action.
So, what is Skybox doing differently?
It prioritizes vulnerabilities based on:
-
Network exposure
-
Asset criticality
-
Threat intelligence
-
Business impact
This reduces noise and improves efficiency.
Practical Benefits for IT Leaders
-
Faster remediation decisions
-
Improved firewall rule management
-
Reduced manual audits
-
Better cross-team visibility
For CISOs and IT managers, this means better risk-based decision-making.
Skybox and Vulnerability Management
Vulnerability management is a core pillar of modern cybersecurity.
When evaluating what is Skybox, vulnerability prioritization is a major component.
Traditional vulnerability scanning tools may generate massive lists. However, not all vulnerabilities pose equal risk.
Skybox analyzes:
-
Which vulnerabilities are exploitable
-
Whether assets are reachable
-
How firewall configurations affect exposure
This contextual intelligence makes patch management more strategic.
Skybox for Network Security Policy Management
Firewall misconfigurations are one of the top causes of security breaches.
What is Skybox’s role here?
Skybox audits firewall policies to:
-
Detect redundant rules
-
Identify risky open ports
-
Ensure compliance alignment
-
Simulate rule changes before deployment
For enterprises with complex hybrid networks, this visibility is crucial.
Skybox in Hybrid and Cloud Environments
Modern businesses operate across:
-
On-premises data centers
-
Public cloud platforms
-
Remote endpoints
-
Multi-cloud infrastructure
Understanding what is Skybox also involves its ability to map hybrid networks.
It integrates with cloud environments to assess:
-
Cloud security posture
-
Access controls
-
Virtual firewall configurations
As digital transformation accelerates, centralized visibility becomes essential.
Industries That Benefit from Skybox
Financial Services
Banks use Skybox to manage compliance and protect sensitive transaction data.
Healthcare
Healthcare providers leverage attack path analysis to protect patient records.
Manufacturing
Industrial networks require segmentation and visibility to prevent operational disruption.
Government
Public sector agencies use risk modeling to secure critical infrastructure.
For executives, understanding what is Skybox helps align cybersecurity investments with regulatory requirements.
Limitations and Considerations
No platform is perfect. When exploring what is Skybox, it’s important to consider potential challenges.
Implementation Complexity
Large environments may require time to integrate fully.
Cost Considerations
Enterprise-grade security solutions can be significant investments.
Resource Requirements
Security teams need trained personnel to interpret analytics effectively.
That’s why many organizations combine platforms like Skybox with managed cybersecurity services.
Skybox vs Other Security Platforms
Security leaders often compare Skybox with:
-
Vulnerability scanners (e.g., Tenable, Qualys)
-
SIEM platforms
-
Firewall management tools
While scanners identify vulnerabilities, Skybox contextualizes them.
While SIEM tools monitor events, Skybox focuses on exposure modeling.
Understanding what is Skybox means recognizing its niche: risk-based vulnerability prioritization and network modeling.
How Skybox Supports Risk-Based Security
Modern cybersecurity strategy focuses on risk reduction, not just threat detection.
Skybox contributes by:
-
Mapping network attack surfaces
-
Quantifying exposure
-
Prioritizing critical risks
-
Supporting board-level reporting
CEOs and founders increasingly demand measurable cybersecurity ROI. Tools that quantify exposure help justify budgets.
Best Practices When Using Skybox
If your organization is evaluating what is Skybox for deployment, consider these tips:
1. Integrate with Existing Tools
Ensure it connects with vulnerability scanners and firewalls.
2. Focus on High-Value Assets
Prioritize critical business systems first.
3. Align With Compliance Goals
Map findings to regulatory frameworks.
4. Combine with Endpoint Security
Network visibility alone is not enough.
Comprehensive protection requires layered defense strategies.
The Bigger Picture: Skybox and Cyber Resilience
Cyber resilience is about surviving and recovering from attacks.
Understanding what is Skybox is only part of the equation.
Organizations must also:
-
Deploy endpoint protection
-
Monitor suspicious behavior
-
Implement Zero Trust architecture
-
Maintain incident response plans
Network modeling tools strengthen visibility, but prevention and containment remain essential.
Frequently Asked Questions (FAQ)
1. What is Skybox used for?
What is Skybox used for? It is used for vulnerability management, network security policy analysis, and attack path modeling to reduce cyber risk.
2. Is Skybox a vulnerability scanner?
No. Skybox integrates with vulnerability scanners but focuses on contextual risk analysis rather than simple scanning.
3. Does Skybox replace SIEM tools?
No. SIEM tools monitor real-time events. Skybox focuses on exposure modeling and risk prioritization.
4. Is Skybox suitable for small businesses?
Skybox is primarily designed for mid-sized to large enterprises with complex network environments.
5. How does Skybox improve cybersecurity posture?
It helps prioritize risks based on exploitability and network exposure, reducing attack surface efficiently.
Final Thoughts: Is Skybox Enough for Complete Protection?
So, what is Skybox in the broader cybersecurity ecosystem? It is a powerful risk visualization and vulnerability prioritization platform. It gives security teams insight into attack paths and firewall exposure.
However, no single tool can stop modern threats alone.
True protection requires:
-
Advanced endpoint security
-
Real-time threat containment
-
Managed detection and response
-
Continuous monitoring
If your organization is evaluating network risk management and wants a more comprehensive cybersecurity strategy, it’s time to look beyond isolated tools.
👉 Discover how Xcitium helps businesses contain threats in real time, protect endpoints, and strengthen overall cyber resilience.
Request a personalized demo today:
https://www.xcitium.com/request-demo/
Your network visibility matters — but proactive threat containment makes the difference.