What Is a USB Flash Drive? Definition, Uses, and Security Risks
Updated on October 28, 2025, by Xcitium
Have you ever transferred files between computers without the internet? You’ve probably used a USB flash drive, one of the simplest and most convenient tools for storing and moving data. Despite their small size, these devices hold immense power — and potential risk.
In today’s digital landscape, USB flash drives are not only storage tools but also a security concern. Whether you’re a business executive, IT manager, or cybersecurity professional, understanding how USB drives work — and how to secure them — is essential to protecting your organization’s data.
Let’s dive into what is a USB flash drive, how it functions, its advantages, and the best practices to keep your data safe.
What Is a USB Flash Drive?
A USB flash drive (also called a thumb drive, pen drive, or memory stick) is a portable data storage device that uses flash memory and connects to computers via a USB (Universal Serial Bus) interface.
These small, plug-and-play devices can store, read, and transfer data between different devices — without needing internet or external power.
In essence, a USB flash drive serves as your digital briefcase — compact, reliable, and capable of storing gigabytes (even terabytes) of data in your pocket.
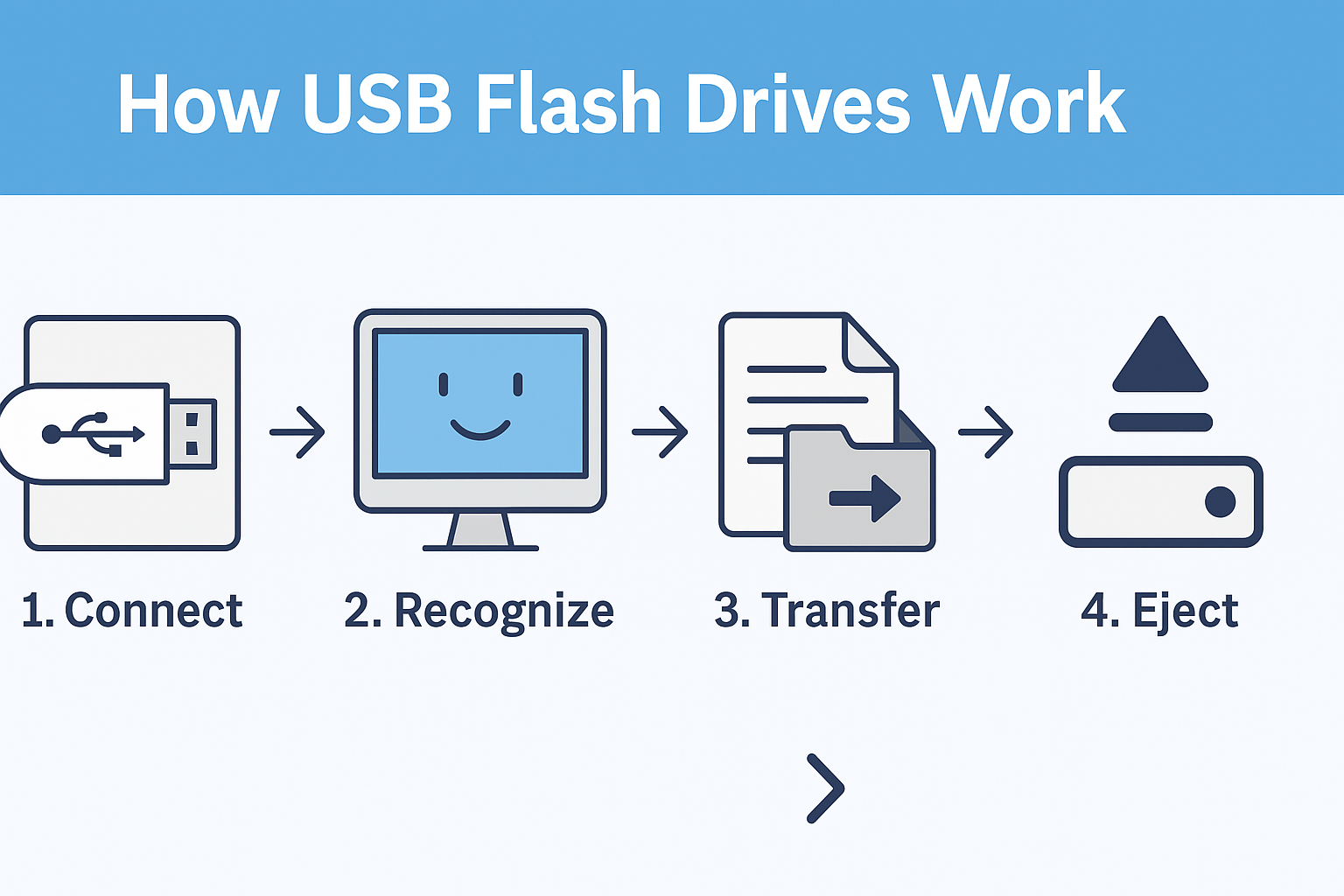
How Does a USB Flash Drive Work?
At its core, a USB flash drive uses flash memory technology, a type of non-volatile memory that retains information even without power. Here’s how it works:
-
Connection: You plug the drive into a USB port.
-
Recognition: The operating system automatically detects the device.
-
Data Transfer: You can read, write, copy, or delete files directly from the drive.
-
Ejection: After completing tasks, safely remove the drive to prevent data corruption.
USB flash drives communicate using standard protocols like USB 2.0, USB 3.0, and USB 3.2, with transfer speeds ranging from 480 Mbps to over 5 Gbps.
Key Components of a USB Flash Drive
A typical USB flash drive includes:
-
USB Connector: The plug that connects to computers or devices.
-
Controller Chip: Manages data flow between the device and memory.
-
Flash Memory Chip: Stores all the data.
-
Crystal Oscillator: Maintains timing and signal consistency.
-
Protective Casing: Shields internal components from physical damage.
Together, these components make USB drives durable, portable, and universally compatible.
Common Uses of USB Flash Drives
USB drives have countless applications across industries and everyday life.
1. Data Storage and Backup
Used for saving important documents, photos, videos, and software for quick access.
2. File Transfer
Ideal for sharing data between offline systems without network dependency.
3. Operating System Installation
Bootable USBs are used to install or repair operating systems like Windows or Linux.
4. Secure Data Transport
Encrypted USB drives allow safe transfer of sensitive files.
5. Media Playback and Archiving
Used in cars, TVs, and sound systems for media playback.
6. Cybersecurity Testing and Digital Forensics
Penetration testers use USBs for vulnerability analysis, while forensic experts use them for data recovery.
Advantages of USB Flash Drives
Despite the rise of cloud storage, USB flash drives remain highly relevant. Here’s why:
✅ Portability
Their compact size makes them ideal for on-the-go professionals.
✅ High Data Transfer Speeds
Modern USB 3.2 and USB-C drives provide lightning-fast transfer rates.
✅ Compatibility
They work across desktops, laptops, servers, and even smart TVs.
✅ Reliability
Flash memory ensures data durability and stability even without power.
✅ No Internet Dependency
Data transfers can happen in isolated, secure environments — crucial for cybersecurity teams.
Security Risks of USB Flash Drives
While USB flash drives offer convenience, they also present serious cybersecurity risks.
1. Malware and Virus Transmission
Infected USB drives can spread malware across networks instantly.
Example: The Stuxnet worm, one of the most notorious cyberattacks, spread via USB drives.
2. Data Theft and Loss
Unencrypted drives can easily be lost or stolen, exposing sensitive data.
3. Unauthorized Access
If an employee plugs in an unknown or infected USB, it could lead to a data breach or ransomware attack.
4. Hardware Manipulation (BadUSB)
Hackers can reprogram a USB device’s firmware to act as a malicious keyboard or network adapter, compromising systems silently.
5. Human Error
Forgetting to eject the drive properly or plugging it into an infected system can corrupt data or trigger infections.
How to Protect Against USB Flash Drive Threats
To maintain security while using USB flash drives, organizations and individuals must follow strict cybersecurity practices.
🛡️ 1. Use Encrypted USB Drives
Always use hardware-encrypted USB drives that require PINs or passwords for access.
🧹 2. Scan USB Devices Automatically
Enable automatic antivirus or Endpoint Detection and Response (EDR) scans when connecting external devices.
⚙️ 3. Disable Auto-Run
Prevent systems from automatically executing files on newly connected drives.
🔒 4. Implement Data Loss Prevention (DLP) Policies
Control which USB devices can connect to corporate networks and monitor data transfers.
🧑💻 5. Educate Employees
Train staff to avoid using unverified USBs and report suspicious devices immediately.
💼 6. Use Managed Endpoint Security
Tools like Xcitium OpenEDR detect and isolate potential threats from USB connections in real-time.
USB Flash Drives vs. External Hard Drives
| Feature | USB Flash Drive | External Hard Drive |
|---|---|---|
| Storage Capacity | 8GB – 2TB | 500GB – 10TB+ |
| Portability | Very compact | Larger and heavier |
| Speed | Fast (USB 3.0/3.2) | Varies (SSD faster, HDD slower) |
| Durability | Shock-resistant | Fragile (especially HDD) |
| Price per GB | Slightly higher | More economical |
| Use Case | Quick data transfers | Large-scale backups |
Types of USB Flash Drives
-
Standard USB 2.0 / 3.0 / 3.2 Drives – Common for everyday use.
-
Encrypted USB Drives – Include built-in password protection or hardware encryption.
-
Bootable USB Drives – Used for OS installations or diagnostics.
-
Wireless USB Drives – Enable Wi-Fi-based transfers to mobile devices.
-
Custom/Corporate USBs – Used for branding or secure enterprise distribution.
Each type serves a unique purpose — from convenience to advanced security.
The Role of USB Flash Drives in Cybersecurity
Interestingly, USB drives play a dual role in cybersecurity — as both a threat vector and a defensive tool.
🔓 As a Threat Vector
-
Malicious drives can deploy ransomware or steal credentials.
-
Attackers can drop infected USBs in public spaces (known as “USB drop attacks”).
🔐 As a Security Tool
-
Cyber professionals use USBs for penetration testing, data recovery, and digital forensics.
-
Tools like Kali Linux Live USB or Rescue Disks are vital for incident response.
This dual nature makes it essential to control how USBs are managed within enterprise environments.
Best Practices for Secure USB Drive Management
Follow these industry-recommended best practices:
-
Restrict USB Port Access – Limit which devices can connect to critical systems.
-
Use Endpoint Protection Software – Monitor data transfers and block untrusted devices.
-
Label and Track Devices – Assign drives to specific users or departments.
-
Regularly Update Firmware – Prevent vulnerabilities in USB controllers.
-
Implement Encryption-by-Default Policies – Encrypt all portable storage devices organization-wide.
By integrating OpenEDR and Zero Trust principles, businesses can eliminate USB-based risks without losing productivity.
Emerging Technologies: The Future of USB Flash Drives
With the rise of cloud computing, AI, and IoT, USB technology continues to evolve.
🔹 USB 4.0 and USB-C
Faster transfer speeds and universal compatibility across laptops, servers, and mobile devices.
🔹 Secure USB with Biometric Authentication
Fingerprint-protected USBs enhance physical security for sensitive data.
🔹 Self-Destructing Drives
Some military-grade devices can erase data automatically after unauthorized access attempts.
🔹 Integration with Cloud Backups
Hybrid storage devices sync local files with encrypted cloud servers for redundancy.
The next generation of USB flash drives will merge portability with enterprise-grade data security.
Conclusion
In a connected world where data mobility equals productivity, USB flash drives remain indispensable. But convenience must never come at the cost of security.
Understanding what is a USB flash drive — and how to use it securely — empowers professionals and organizations to protect sensitive information effectively.
Whether you’re backing up data, deploying software, or sharing files, always pair your USB use with strong encryption, endpoint protection, and cybersecurity vigilance.
👉 Stay protected and proactive.
Explore how Xcitium helps businesses detect, isolate, and neutralize USB-borne threats in real time.
FAQs About USB Flash Drives
1. What is a USB flash drive used for?
A USB flash drive is used for storing, transferring, and backing up digital files between devices without internet access.
2. Are USB flash drives secure?
Standard drives aren’t fully secure. Always use encrypted USBs and endpoint protection to safeguard sensitive data.
3. Can a USB drive carry a virus?
Yes. Malware can hide in executable files or autorun scripts within a USB drive.
4. How do I make my USB drive safe?
Use password-protected or hardware-encrypted drives, disable autorun, and scan devices regularly.
5. What is the difference between a USB flash drive and a pen drive?
They’re essentially the same — “pen drive” is a common name for USB flash drives in some regions.