What Is DoH? A Complete Guide for Modern Cybersecurity Leaders
Updated on February 11, 2026, by Xcitium
Have you ever wondered how exposed your DNS traffic really is? If you’re asking what is DoH, you’re already thinking like a cybersecurity leader. DNS queries often travel unencrypted, leaving organizations vulnerable to monitoring, spoofing, and manipulation.
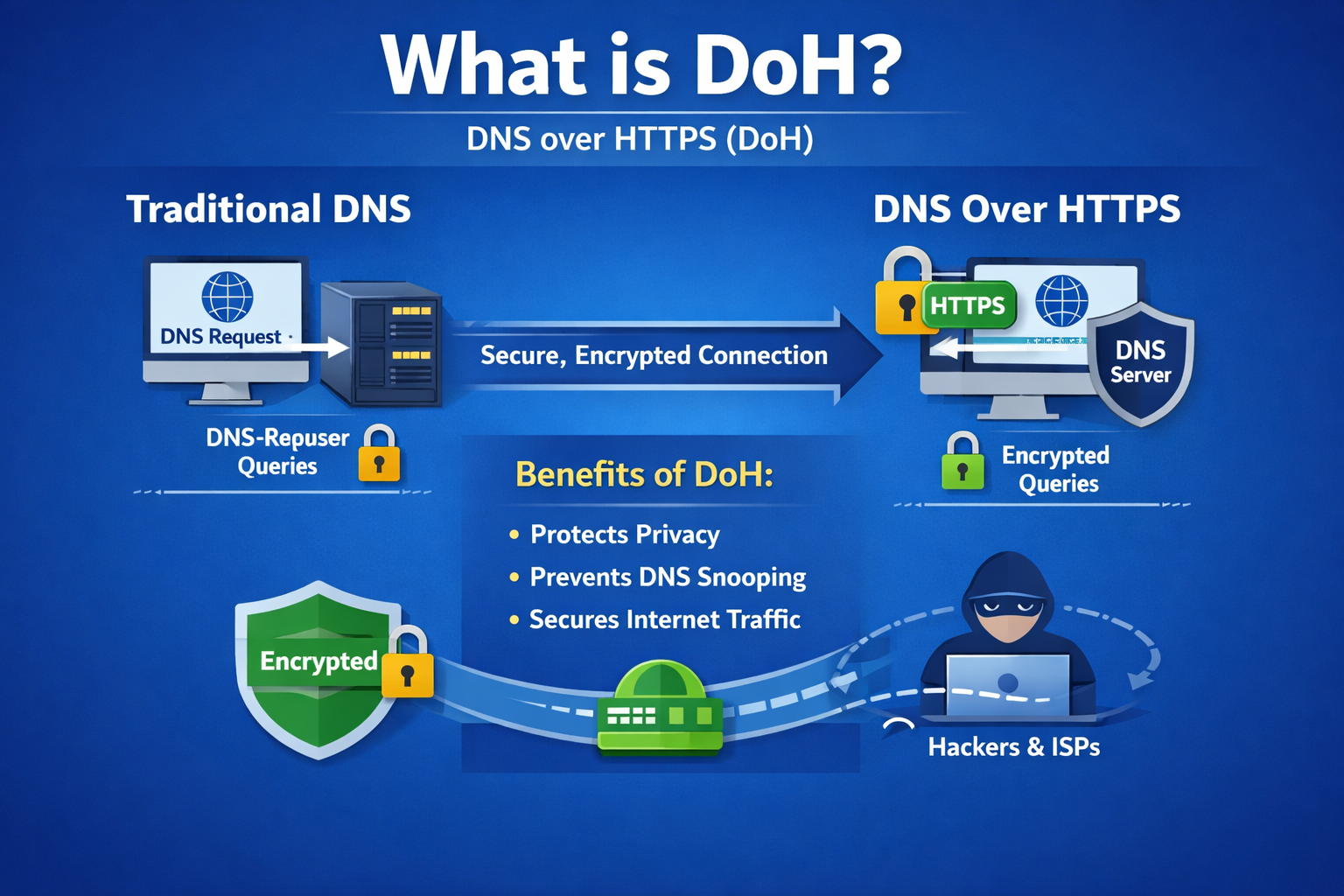
So, what is DoH and why does it matter to IT managers, cybersecurity professionals, and CEOs? In simple terms, DNS over HTTPS (DoH) encrypts DNS requests using HTTPS, the same protocol that secures websites. This adds a critical layer of privacy and protection to one of the internet’s most essential services.
For enterprises focused on secure DNS, data privacy, and network security, understanding what is DoH is no longer optional — it’s strategic.
What Is DoH and How Does It Work?
To fully understand what is DoH, we first need to revisit how DNS works.
The Domain Name System (DNS) acts like the internet’s phonebook. When users type a domain name (like example.com), DNS translates it into an IP address. Traditionally, these DNS queries are sent in plain text over port 53. Anyone monitoring the network can see or even alter them.
DNS Over HTTPS (DoH) Explained
DNS over HTTPS encrypts DNS queries by sending them through HTTPS connections (port 443). This means:
-
DNS requests are encrypted
-
Traffic blends in with regular web browsing
-
Third parties cannot easily intercept or manipulate queries
In short, what is DoH? It’s encrypted DNS traffic wrapped inside HTTPS.
Traditional DNS vs DoH
| Feature | Traditional DNS | DNS over HTTPS (DoH) |
|---|---|---|
| Encryption | No | Yes |
| Port Used | 53 | 443 |
| Privacy | Low | High |
| Attack Resistance | Vulnerable to spoofing | Stronger protection |
For organizations serious about cybersecurity infrastructure, this shift matters.
Why DoH Is Critical for Enterprise Security
Understanding what is DoH is only half the story. The real value lies in its security impact.
1. Protection Against DNS Spoofing
Attackers often manipulate DNS responses to redirect users to malicious websites. This is known as DNS spoofing or cache poisoning.
DoH prevents attackers from easily tampering with DNS responses because the data is encrypted.
2. Enhanced Data Privacy
DNS queries reveal user behavior. They show which domains employees access, which SaaS tools are used, and sometimes even internal systems.
With DNS encryption:
-
ISPs cannot monitor DNS traffic
-
Network eavesdroppers cannot track browsing
-
Man-in-the-middle attacks become harder
For CEOs concerned about compliance and privacy laws, DoH strengthens corporate governance.
3. Reduced Risk of Surveillance
In industries like finance, healthcare, and defense, DNS metadata can be sensitive. DoH limits exposure to external monitoring.
When evaluating secure DNS solutions, DoH plays a major role.
DoH vs DoT: What’s the Difference?
Many security leaders confuse DNS over HTTPS (DoH) with DNS over TLS (DoT). While both encrypt DNS traffic, they differ in deployment and visibility.
DNS over TLS (DoT)
-
Uses port 853
-
Dedicated DNS encryption channel
-
Easier for enterprises to monitor and control
DNS over HTTPS (DoH)
-
Uses port 443 (HTTPS)
-
Harder to distinguish from normal web traffic
-
Improves privacy but may reduce visibility
If you’re evaluating enterprise network security policies, the question isn’t just what is DoH — it’s how it compares with alternatives.
The Benefits of DoH for IT Managers
For IT managers and security teams, what is DoH becomes a practical deployment question.
Key Advantages
-
Encrypted DNS queries
-
Protection against DNS hijacking
-
Improved user privacy
-
Reduced DNS manipulation risks
-
Stronger remote workforce security
In hybrid work environments, remote endpoints are vulnerable to public Wi-Fi attacks. DoH ensures DNS security outside corporate firewalls.
Potential Risks and Concerns with DoH
While DoH improves security, it also introduces operational considerations.
1. Reduced Network Visibility
Security teams rely on DNS logs for:
-
Threat detection
-
Malware domain blocking
-
Data exfiltration monitoring
If endpoints use external DoH providers, internal security tools may lose visibility.
2. Policy Enforcement Challenges
Organizations that rely on DNS filtering for compliance may struggle if browsers bypass corporate DNS servers.
This is why managed cybersecurity services often combine DoH with endpoint protection and centralized monitoring tools.
How Cybercriminals Exploit DNS
To understand what is DoH, it helps to examine common DNS-based attacks.
Common DNS Threats
-
DNS spoofing
-
DNS tunneling (data exfiltration)
-
Command-and-control communications
-
Domain generation algorithms (DGA)
DNS remains one of the most abused attack vectors in cybersecurity.
By encrypting DNS traffic, DoH makes passive interception harder. However, organizations still need advanced threat detection at the endpoint level.
Should Enterprises Enable DoH?
The decision depends on your security architecture.
When DoH Makes Sense
-
Remote workforce environments
-
BYOD policies
-
Public network usage
-
Privacy-focused industries
When Caution Is Needed
-
Strict DNS filtering environments
-
Regulatory compliance frameworks
-
Legacy monitoring systems
The best approach is controlled deployment using enterprise-grade cybersecurity platforms.
How to Implement DoH in an Organization
If you’re evaluating what is DoH from a deployment standpoint, here are actionable steps:
Step 1: Audit Current DNS Infrastructure
-
Identify DNS servers in use
-
Review logging capabilities
-
Assess DNS filtering policies
Step 2: Define Security Objectives
Are you prioritizing privacy, monitoring, or both?
Step 3: Choose an Enterprise DoH Strategy
Options include:
-
Browser-level DoH configuration
-
OS-level DNS settings
-
Centralized DNS security providers
-
Managed cybersecurity services
Step 4: Maintain Visibility
Use endpoint detection and response (EDR) tools that monitor encrypted traffic behavior patterns.
Encryption alone does not equal security.
Industry Impact: Why CEOs Should Care About DoH
For leadership teams, the question what is DoH ties directly to risk management.
Financial Sector
-
Prevent DNS-based fraud
-
Protect online banking sessions
Healthcare
-
Safeguard patient data privacy
-
Strengthen HIPAA compliance posture
Manufacturing
-
Reduce supply chain cyber risks
-
Protect industrial control systems
SaaS & Tech Companies
-
Secure developer environments
-
Prevent intellectual property theft
DNS attacks often serve as entry points for ransomware campaigns. Encrypting DNS is one defensive layer — but it must integrate into a broader cybersecurity framework.
DoH and Zero Trust Security
Modern enterprises adopt Zero Trust models. In this architecture:
-
No device is trusted by default
-
Continuous verification is required
-
Network traffic is encrypted
DoH aligns with Zero Trust principles by encrypting DNS lookups. However, Zero Trust also demands:
-
Endpoint visibility
-
Behavior-based detection
-
Automated response capabilities
DoH supports privacy — but it must coexist with advanced threat intelligence systems.
The Future of DNS Security
DNS security is evolving rapidly.
Emerging trends include:
-
AI-powered DNS threat detection
-
Secure access service edge (SASE)
-
DNS-layer malware blocking
-
Encrypted DNS standardization
Understanding what is DoH prepares organizations for this shift.
But encryption alone does not stop modern attacks. Attackers now use encrypted channels too.
This is why DNS protection must combine:
-
Encryption
-
Monitoring
-
Behavioral analysis
-
Managed security operations
Frequently Asked Questions (FAQ)
1. What is DoH in simple terms?
What is DoH? It stands for DNS over HTTPS. It encrypts DNS queries using HTTPS to improve privacy and protect against DNS-based attacks.
2. Is DoH better than traditional DNS?
Yes, in terms of privacy and encryption. Traditional DNS sends queries in plain text, while DoH encrypts them.
3. Does DoH improve cybersecurity?
DoH improves DNS privacy and reduces certain attack risks. However, it should be combined with endpoint security and monitoring tools for full protection.
4. Can DoH bypass enterprise security controls?
Yes, if not configured properly. Browser-level DoH can bypass internal DNS filters unless centrally managed.
5. Should my company enable DNS over HTTPS?
It depends on your security strategy. Organizations with remote workers often benefit, but controlled deployment is essential.
Final Thoughts: Is DoH Enough?
So, what is DoH really? It’s a privacy-enhancing protocol that encrypts DNS traffic using HTTPS. It protects against interception, spoofing, and surveillance.
But encryption alone does not stop ransomware, phishing, or zero-day exploits.
Modern enterprises need layered cybersecurity strategies that combine:
-
DNS encryption
-
Endpoint protection
-
Threat intelligence
-
24/7 monitoring
-
Incident response
If your organization is evaluating DNS security or strengthening its cybersecurity posture, now is the time to act.
👉 See how Xcitium helps organizations protect endpoints, networks, and DNS traffic with advanced, managed cybersecurity services.
Request a personalized demo today:
https://www.xcitium.com/request-demo/
Your DNS layer is a frontline defense. Make sure it’s protected.