What Is LoRa? The Complete 2026 Guide for IT Managers, Cybersecurity Teams & Business Leaders
Updated on November 24, 2025, by Xcitium
If you’re exploring modern IoT security or looking to scale low-power devices across your organization, you’ve likely encountered the term LoRa. But what is LoRa, and why has it become one of the most impactful wireless communication technologies in the world?
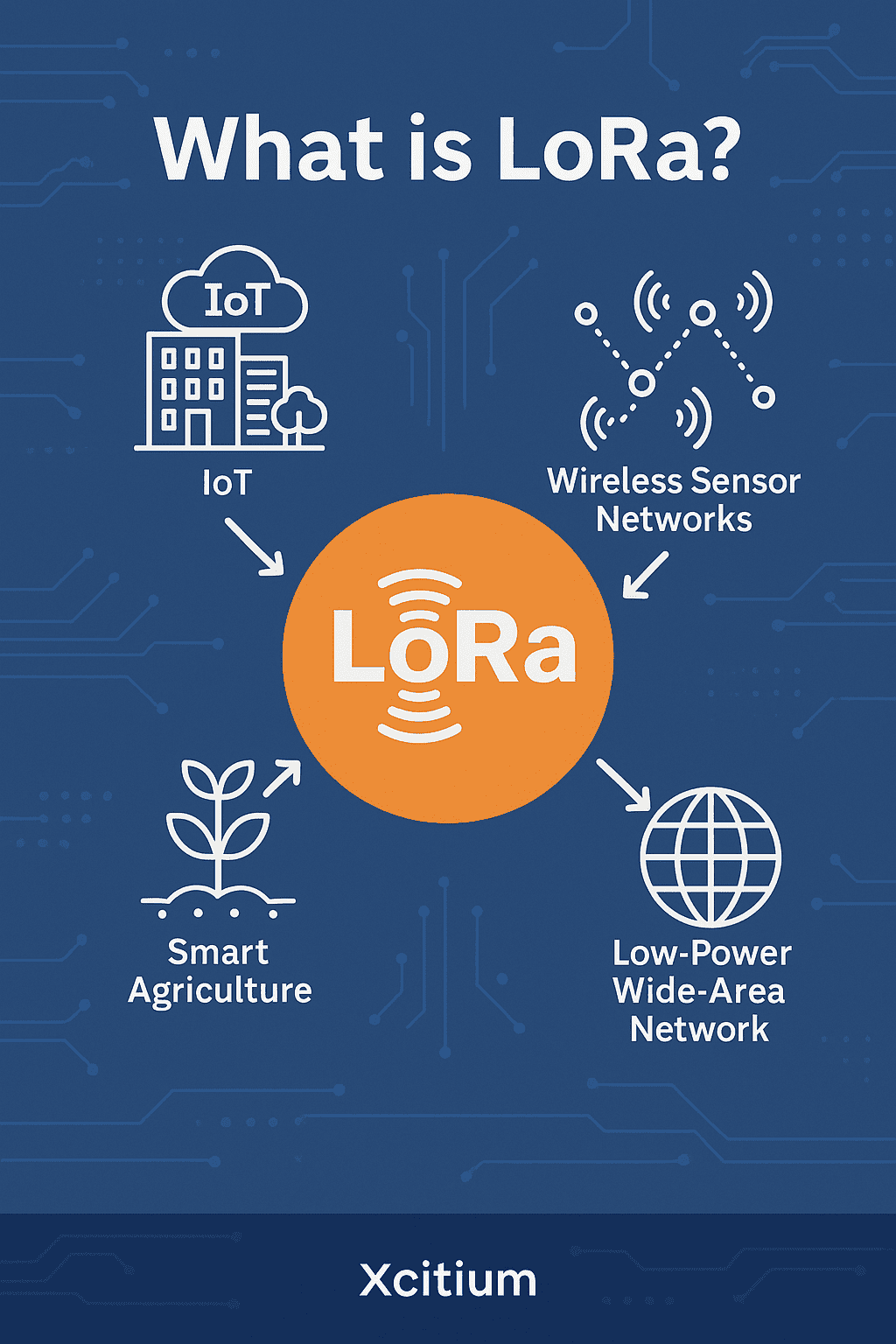
LoRa (Long Range Radio) is a low-power, long-range wireless communication technology designed to connect IoT devices across massive distances—up to 10+ miles—while consuming extremely low energy. Because of its unique characteristics, LoRa has become the backbone of smart cities, industrial IoT, environmental monitoring, logistics, agriculture, utilities, and enterprise security solutions.
In 2025, LoRa plays a critical role in cybersecurity, cloud monitoring, smart sensors, and connected devices. This guide breaks down everything business and IT leaders need to know, including how LoRa works, its benefits, vulnerabilities, use cases, and how to implement it securely.
Use a royalty-free IoT/LoRaWAN network illustration such as:
Search at Unsplash.com → “IoT network abstract,” “wireless nodes,” “communication technology graphic.”
What Is LoRa? A Simple Explanation
At its core, LoRa is a long-range wireless communication protocol that allows battery-powered devices (like sensors) to transmit small packets of data over long distances without requiring cellular or Wi-Fi networks.
LoRa is part of a broader category called LPWAN (Low-Power Wide-Area Networks), designed for:
-
Long-range communication
-
Minimal energy consumption
-
Very low data rates
-
Massive device scalability
What makes LoRa unique is its ability to deliver:
-
Long distance (2–15 miles)
-
Ultra-low power usage (battery life 5–10 years)
-
Low cost
-
Strong interference resistance
-
Scalability for thousands of devices
This makes LoRa ideal for large-scale IoT deployments.
Difference Between LoRa and LoRaWAN
Many people confuse LoRa with LoRaWAN, but they are not the same.
✔ LoRa
A physical radio layer (the modulation technology).
✔ LoRaWAN
A communication protocol and network architecture built on top of LoRa.
An easy way to understand it:
| Component | Purpose |
|---|---|
| LoRa | Determines how data travels through the air |
| LoRaWAN | Determines how devices authenticate, communicate, and connect to the cloud |
Think of LoRa as the “radio,” and LoRaWAN as the “network rules.”
Both work together to create a secure, scalable IoT communication system.
How LoRa Technology Works (Explained Simply)
LoRa uses chirp spread spectrum modulation—a method that spreads data across frequency variations, enabling extremely long-distance communication even in noisy environments.
Here’s the basic flow:
-
IoT sensors collect data (temperature, gas levels, movement, etc.).
-
Sensors transmit data via LoRa radio signals.
-
LoRa gateways receive the data.
-
Gateways forward it to a network server via Wi-Fi, Ethernet, or cellular.
-
The network server authenticates the device and passes data to cloud apps.
-
Businesses use dashboards, APIs, or analytics tools to visualize insights.
The entire system is optimized for low energy usage—so devices can run for years without battery replacements.
Key Features of LoRa Technology
LoRa’s rapid global adoption is driven by several standout features:
1. Long-Range Capability
LoRa can transmit data across:
-
2–5 miles in urban areas
-
10–15 miles in rural or open environments
This makes it ideal for large properties, cities, or industrial locations.
2. Ultra-Low Power Consumption
Sensors can run up to 10 years on a single battery.
Perfect for:
-
Remote areas
-
Hard-to-reach installations
-
Energy-restricted environments
3. Low Data Rate Transmission
LoRa is not designed for video or high-speed transfer.
Instead, it excels at:
-
Small sensor readings
-
Trigger alerts
-
Periodic data updates
4. Secure Communication
LoRaWAN uses:
-
AES-128 encryption
-
End-to-end authentication
-
Secure device identification
This is crucial for enterprise cybersecurity.
5. Highly Scalable
A single LoRa gateway can handle thousands of IoT devices.
Top Use Cases of LoRa in 2026
LoRa has grown far beyond basic IoT sensors. Today, it powers enterprise-scale systems in countless industries.
1. Smart Cities
-
Streetlights
-
Traffic systems
-
Waste monitoring
-
Parking sensors
-
Water distribution
2. Agriculture
-
Soil moisture
-
Livestock tracking
-
Irrigation automation
-
Weather stations
3. Industrial Manufacturing
-
Asset tracking
-
Temperature & vibration monitoring
-
Predictive maintenance
4. Supply Chain & Logistics
-
Fleet tracking
-
Cargo conditions
-
Warehouse optimization
5. Environmental Monitoring
-
Air quality
-
Water quality
-
Forest fire detection
6. Healthcare
-
Patient monitoring sensors
-
Medical equipment tracking
7. Corporate Security & Compliance
-
Facility access sensors
-
Perimeter monitoring
-
Server room environment sensors
LoRa Security Explained (What Cybersecurity Teams Must Know)
Since LoRa connects thousands of devices, security must be a core priority.
Here are the main risks and protections:
LoRa Security Risks
-
Device spoofing
-
Gateway impersonation
-
Replay attacks
-
Key extraction
-
Firmware tampering
These vulnerabilities often arise from weak device management—not the LoRa protocol itself.
LoRa Security Protections
✔ End-to-End Encryption (AES-128)
Every LoRaWAN packet is encrypted so only servers can read data.
✔ Unique Keys per Device
LoRaWAN uses:
-
Network session key
-
Application session key
✔ Mutual Authentication
Prevents unauthorized devices from joining networks.
✔ Nonce-based Protection
Stops replay attacks.
✔ Frequency Hopping
Makes interception more difficult.
Benefits of LoRa for Enterprises & Cybersecurity Teams
✔ Massive scalability
✔ Low cost of deployment
✔ Strong encryption
✔ Long battery life reduces maintenance
✔ Works even in remote locations
✔ No reliance on cellular carriers
✔ Ideal for secure monitoring of physical assets
Comparing LoRa to Other IoT Technologies
| Technology | Range | Power | Speed | Use Case |
|---|---|---|---|---|
| LoRa | Very long | Very low | Low | Wide-area sensors |
| Wi-Fi | Short | High | High | Local networks |
| Bluetooth | Very short | Low | Medium | Wearables |
| 5G | Medium | Medium/High | Very high | High-bandwidth IoT |
| Sigfox | Long | Low | Low | Basic sensors |
| NB-IoT | Long | Medium | Low | Carrier-managed IoT |
LoRa is ideal for organizations needing wide coverage + low cost.
How to Implement LoRa in Your Organization
Here’s a simple roadmap for IT leaders:
1. Define Your Use Case
Examples:
-
Security sensors
-
Environmental monitoring
-
Smart infrastructure
2. Choose Your LoRa Network Model
Options include:
-
Private LoRaWAN network
-
Public LoRaWAN network
-
Hybrid network (common in enterprise)
3. Deploy LoRa Gateways
Install gateways in strategic areas:
-
Rooftops
-
Utility poles
-
High-elevation structures
4. Register Devices in the Network Server
Each device receives:
-
Unique device ID
-
Security keys
-
Configuration parameters
5. Integrate with the Cloud
Most companies use:
-
AWS IoT
-
Azure IoT Hub
-
Google Cloud IoT
-
On-premise servers
6. Build Dashboards & Alerts
Use:
-
Grafana
-
Kibana
-
Cloud dashboards
-
Custom APIs
7. Secure the Entire System
Implement:
-
Zero-Trust architecture
-
Endpoint detection
-
Firmware verification
-
Key rotation policies
Frequently Asked Questions (FAQ)
1. What is LoRa used for?
LoRa is used for long-range, low-power communication between IoT devices such as sensors, trackers, meters, and monitoring systems.
2. Is LoRa the same as LoRaWAN?
No. LoRa is the radio modulation technology; LoRaWAN is the network protocol built on top of it.
3. Is LoRa secure?
Yes—LoRaWAN uses industry-standard AES-128 encryption and authentication, though proper device management is essential.
4. How far can LoRa transmit?
Between 2 and 15 miles depending on environment, elevation, and gateway placement.
5. Is LoRa better than Wi-Fi?
Not for speed, but for long-range, low-data, battery-powered devices, LoRa is significantly more efficient.
Final Thoughts: LoRa Is Reshaping the Future of IoT and Secure Connectivity
Now that you understand what LoRa is, it’s easy to see why organizations across industries—from manufacturing to smart cities—are adopting it at scale. Its long range, low cost, strong security, and unmatched power efficiency make it an ideal solution for modern IoT deployments.
As threats to IoT environments rise, cybersecurity teams must ensure proper encryption, device onboarding, and network monitoring. LoRa is powerful, but its security depends heavily on implementation.
🚀 Strengthen Your IoT & Endpoint Security Today
Protect your enterprise devices and networks with advanced cybersecurity.
👉 Request a Demo: https://www.xcitium.com/request-demo/