Offering feature-rich, autonomous security that harnesses the power of data and AI across the enterprise.
| Essential EDR | Pro EDR | Enterprise EDR with EXDR | |
|---|---|---|---|
| Get a demo | Get a demo | Get a demo | |
| Platform Technology Stack | |||
| NGAV (1st Tech Stack on Endpoint) Next-Generation Antivirus leveraging AI and behavioral analysis to detect and prevent sophisticated threats. |
|||
| Award-winning Firewall Control (2nd Tech Stack on Endpoint) Advanced firewall capabilities to monitor and control incoming and outgoing network traffic effectively. |
|||
| EDR (EDR with HIPS) (3rd Tech Stack on Endpoint) Protects individual devices by monitoring, identifying, and auto-responding to potential intrusions at the endpoint level. |
|||
| Deception (4th Tech Stack on Endpoint) Xcitium delivers deception-like security by isolating unknown threats in a lightweight, non-persistent virtualised environment—no decoys, no assumptions, no impact. |
|||
| Zero Trust (5th Tech Stack on Endpoint) Proactively neutralize unknown threats by virtualizing their attack vectors, effectively preventing damage from emerging and undetected threats with Patented Zero Trust Containment technology. |
|||
| ITSM (6th Tech Stack on Endpoint) Tools and processes for managing IT services, incident response, and integration with security workflows. |
|||
| EXDR (Enhanced XDR) (7th Tech Stack on Endpoint) Extends endpoint detection and response by integrating network, cloud, and identity telemetry to deliver unified threat visibility and automated cross-domain response across the enterprise. |
|||
| SIEM - Security Information & Event Management (8th Tech Stack On cloud) Aggregates and analyzes security data across an organization for real-time threat detection and response. |
|||
| Platform Capabilities | |||
| Tri-Detection vs Uni-Detection Tri-detection employs multiple methods (e.g., static, behavioral, and AI), compared to a single-detection approach. |
|||
| Integrated AI/ML Threat Intel & Indicators Uses AI/ML to analyze threat intelligence and provide actionable insights for early threat detection. |
|||
| NGAV Static & Behavioral AI Threat Prevention Combines traditional static analysis with behavioral AI to identify and prevent known and emerging threats. |
|||
| Data Loss Prevention & Remediation Prevents sensitive data exfiltration and provides automated remediation strategies to reduce data breaches. |
|||
| Attack Surface Reduction Identifies and minimizes entry points for attackers, reducing overall exposure to threats. |
|||
| Viruscope Monitors application behavior to detect and block malicious activity in real time. |
|||
| Advanced EDR (AEDR) | |||
| Advanced Response Tools Provides centralized monitoring and control of endpoints for proactive management. |
|||
| Remote Scripting Capabilities Enables administrators to execute scripts remotely for remediation and system management. |
|||
| Quarantine and Removal of Files Isolates malicious files and removes them to prevent further infection or propagation. |
|||
| Kill Processes Remotely Terminates malicious or unauthorized processes on endpoints from a centralized location. |
|||
| File Retrieval Allows secure retrieval of files from endpoints for forensic analysis or investigation. |
|||
| CLI assess to the endpoint Allows secure command line and powershell access to endpoints for analysis or investigation. |
|||
| Remote windows event log Allows for secure remote access to windows event logs for for analysis or investigation. |
|||
| Network Isolation Segregates compromised endpoints from the network to contain threats and prevent spread. |
|||
| Enhanced XDR (EXDR) Detection | |||
| Interprocess Memory Access Monitors and detects unauthorized or suspicious access between processes to prevent malicious exploitation. |
|||
| Windows/WinEvent Hook Tracks hooks into Windows events, often used by attackers to monitor or manipulate system behavior. |
|||
| Device Driver Installations Detects installation of potentially malicious or unauthorized drivers to protect system integrity. |
|||
| File Access/Modification/Deletion Monitors changes to files for signs of tampering, unauthorized access, or data exfiltration attempts. |
|||
| Registry Access/Modification/Deletion Tracks interactions with the Windows Registry to identify unauthorized changes or potential persistence mechanisms. |
|||
| Network Connection Observes outgoing and incoming network traffic to identify malicious connections or data exfiltration. |
|||
| URL Monitoring Tracks access to URLs to detect phishing, malware downloads, or command-and-control (C2) communication. |
|||
| DNS Monitoring Monitors DNS queries to detect suspicious or anomalous domain resolution activity linked to attacks. |
|||
| Process Creation Tracks the creation of processes to identify unauthorized or suspicious execution patterns. |
|||
| Thread Creation Monitors thread-level activity for malicious behavior, such as injected or rogue threads. |
|||
| Inter-Process Communication (Named Pipes, etc) Observes inter-process communications like named pipes to detect covert data sharing or control signals. |
|||
| Telemetry data itself can be extended in real time Enables real-time expansion of telemetry data for deeper insights and rapid response to emerging threats. |
|||
| Event chaining and enrichment on the endpoints Correlates and enriches security events directly on endpoints for contextualized threat detection and response. |
|||
| Enhanced XDR (EXDR) Investigation | |||
| Adaptive Event Modeling Dynamically models events to identify anomalous patterns and detect evolving threats. |
|||
| Behavioral Analysis Examines active memory, OS activity, user behavior, and application processes for signs of malicious behavior. |
|||
| Static Analysis of Files Analyzes files using machine learning to detect threats, excluding traditional signature-based methods. |
|||
| Time-Series Analysis Evaluates data over time to identify trends, anomalies, and patterns related to potential security events. |
|||
| Integration with Automated Malware Analysis Connects with sandboxing solutions to analyze malware in isolated environments and enhance investigations. |
|||
| Threat Hunting Interface or API Provides tools like YARA, REGEX, ElasticSearch, and IOC search capabilities for advanced threat hunting. |
|||
| Support for Matching Against Private IOC Allows comparison of observed data with private Indicators of Compromise (IOC) for tailored threat detection. |
|||
| Threat Intelligence Integration Insights and visibility into cyber threats and vulnerabilities |
|||
| Linking Telemetry to Recreate Events Connects observable data to reconstruct the sequence of events for detailed investigations. |
|||
| Process/Attack Visualization Visualizes attack paths and processes to simplify analysis and understanding of threats. |
|||
| Alert Prioritization Based on Confidence Ranks alerts by confidence level and allows threshold settings to avoid noise and improve response accuracy. |
|||
| Alert Prioritization Factors System Criticality Considers the criticality of affected systems when prioritizing alerts for response. |
|||
| Risk Exposure Monitoring Tracks risks across the environment and organizes them by logical asset groups for targeted action. |
|||
| Reporting on Frequent Alerts for Automation Identifies repetitive alerts suitable for automated responses to reduce manual workload. |
|||
| Enhanced XDR (EXDR) Remediation | |||
| Remote Scripting Capabilities Enables administrators to execute scripts remotely for remediation and system management. |
|||
| Quarantine and Removal of Files Isolates malicious files and removes them to prevent further infection or propagation. |
|||
| Kill Processes Remotely Terminates malicious or unauthorized processes on endpoints from a centralized location. |
|||
| File Retrieval Allows secure retrieval of files from endpoints for forensic analysis or investigation. |
|||
| Network Isolation Segregates compromised endpoints from the network to contain threats and prevent spread. |
|||
| Services | |||
| (CTRL) Xcitium Threat Research Labs Service Offers access to expert threat researchers for advanced analysis and threat intelligence. |
|||
| Automation Scripting Service Provides custom automation solutions to streamline and accelerate security operations. |
|||
| Baseling Pro Service Assists in creating system baselines for normal behavior to enhance anomaly detection. |
|||
| Cyber Transparency Service Delivers insights and visibility into cyber threats and vulnerabilities affecting the organization. |
|||
| Endpoint Compliancy & Management | |||
| Patch Management Automates the deployment of software updates and patches to reduce vulnerabilities. |
|||
| Vulnerability Reporting Identifies and reports on unpatched vulnerabilities, such as those tied to CVEs, to reduce risk exposure. |
|||
| Xcitium Custom Security Policies Enables creation of tailored security policies to address unique organizational needs. |
|||
| Device Asset Discovery Identifies and inventories all devices within the network to enhance visibility. |
|||
| Remote Monitoring and Management Provides centralized monitoring and control of endpoints for proactive management. |
|||
| Vulnerability Scanning Scans systems to identify and report on vulnerabilities that could be exploited. |
|||
| Device Enrollment Simplifies onboarding of devices into security and management systems. |
|||
| Incident Log Activity Tracks and records security incidents for auditing and investigative purposes. |
|||
| Application Control Manages and restricts application usage to prevent unauthorized or risky software. |
|||
| External Device Control Restricts access and usage of external devices like USB drives to prevent data loss. |
|||
| Compliance Reporting Generates reports to demonstrate adherence to security and regulatory requirements. |
|||
| Hosted Ticketing Provides a centralized ticketing system for managing security-related tasks and issues. |
|||
| Threat Intelligence | |||
| Monthly Threat Briefings Comprehensive summary of detected threats, containment actions, endpoint risk levels, and security trends across your environment. *Available with a minimum number of endpoints. Please contact sales for more information.*Available with a minimum number of endpoints. Please contact sales for more information. |
|||
| Incident Response | |||
| Automated Incident Containment Blocks malicious activity automatically to contain threats. |
|||
| Advanced Capabilities | |||
| AI and Machine Learning Enhances detection and response through advanced analytics. |
|||
| Cloud Sandbox Analyzes and isolates suspicious files in a secure virtual environment to detect and prevent advanced threats. |
|||
| Zero Trust Architecture Support Implements Zero Trust principles for better access control and security. |
|||
| Cross-Platform Protection Covers on-premises, cloud, and hybrid environments for comprehensive security. |
|||
| Platform SLA | |||
| 5x9 Customer Support Provides support during standard business hours. |
|||
| 7x24 Advanced Customer Support Offers continuous support for critical security operations. |
|||
| Data Security & Encryption | |||
| Data Encryption Ensures 100% encryption of data at rest and in transit. |
|||
| Data Retention 7 to 30 days by default, customization options are available. |
|||
| Breach Notification Customers notified of suspected data breaches within 4 hours of discovery. |
|||
| Cyber Insurance | |||
| Cyber Insurance | |||
| Add-Ons (*can be purchased seperately) | |||
| DNS and Web Filtering Blocks access to malicious websites. |
+ | + | + |
| Email Security Monitoring Protects email systems from phishing and spam attacks. |
+ | + | + |
| Cloud Compliance Secure your entire cloud infrastructure with Xcitium's Cloud-Native Application Protection Platform. |
+ | + | + |
| Cloud Security Posture Management (CSPM) Ensure continuous compliance and security across your cloud infrastructure with Xcitium’s Cloud Security Posture Management (CSPM). |
+ | + | + |
| Cloud Workload Protection Platform (CWPP) Secure your cloud workloads with Xcitium’s Cloud Workload Protection Platform (CWPP). |
+ | + | + |
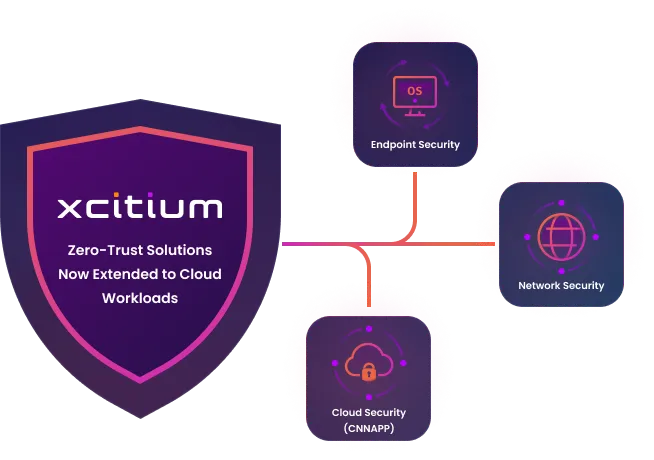
Zero-Trust from Endpoints to Cloud Workloads
We implement a robust zero trust model that spans from endpoints to cloud workloads, ensuring comprehensive security across your entire digital infrastructure. Our patented auto containment technology plays a crucial role in this strategy. By isolating and examining any suspicious activity in real-time, ZeroDwell Containment prevents potential threats from causing harm, regardless of their origin or destination within your network.
System
Management
Management
The Xcitium Difference:
Handling Unknowns
- The EPP/EDR industry is detection-based, ignoring unknowns (zero-day threats)
- Xcitium is the only vendor capable of detecting both knowns and unknowns
- Patented virtualization containment technology eliminates damage from zero-day threats
Benefits
Solution
Why Choose Xcitium?
Xcitium exists to ensure that people can embrace technology fully, without the shadow of insecurity hanging over them. We’re here to give users the freedom to explore, create, and connect without fear. Whether it’s preventing unknown files from compromising systems or offering innovative approaches to endpoint protection solution, Xcitium’s technology is designed to foster confidence. We believe that by keeping the digital ecosystem secure, we’re directly contributing to human evolution—by enabling people to take full advantage of the tools that define our era.





