What Is Internet Proxy? The Ultimate Guide to Proxy Servers
Updated on July 16, 2025, by Xcitium
Ever wondered what is internet proxy and how it affects your online security or browsing speed? Whether you’re a CEO managing corporate networks or an IT manager enhancing endpoint security, understanding internet proxies is essential.
This article explains internet proxy and how it works, its applications in WiFi setups, real-world internet proxy examples, and cybersecurity benefits. Learn how proxy servers function, when to use them, and what proxy server address configurations you need to know.
What Is Internet Proxy?
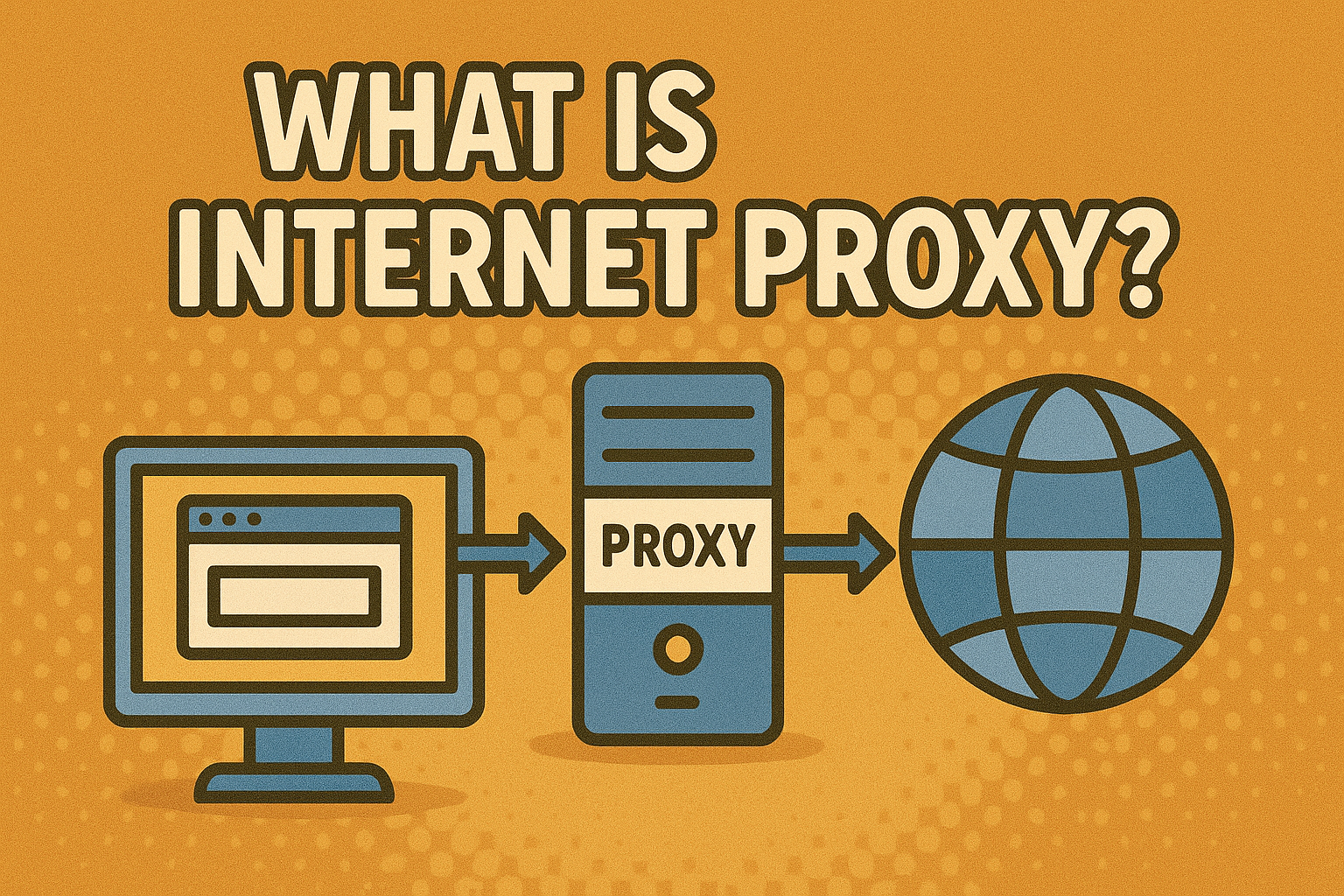
An internet proxy is an intermediary server that sits between your device and the internet. Instead of connecting directly to a website, your request goes through the proxy, which then forwards it to the destination.
In Simple Terms:
A proxy masks your identity by changing your IP address and acting as a gateway between your device and the web.
What Is a Proxy Server Address?
It’s the specific IP address and port number your system uses to connect to the proxy. It tells your browser or device where to send the request before it reaches the internet.
Think of a proxy as your online middleman—it fetches, filters, and sometimes encrypts your traffic.
Internet Proxy and How It Works
A proxy server works by intercepting and relaying your internet traffic. Here’s how it typically functions:
- You type a URL into your browser.
- The request is sent to the proxy server instead of directly to the website.
- The proxy evaluates the request, applies filtering rules, and forwards it.
- The response comes back through the proxy and is delivered to your device.
Proxy Protocols:
- HTTP/HTTPS Proxy: Used for web browsing
- SOCKS Proxy: Supports all traffic types, including FTP and P2P
- Transparent Proxy: No configuration needed; user may be unaware
Proxies can be used for speed, filtering, logging, or anonymity—depending on the setup.
Internet Proxy Used For: Real-World Applications
Proxies serve various purposes in cybersecurity, business, and even casual browsing.
Common Use Cases:
- Security & Anonymity: Mask IPs to protect identities
- Content Filtering: Block access to specific websites or services
- Load Balancing: Distribute network traffic efficiently
- Bypassing Geo-Restrictions: Access region-locked content
- Bandwidth Management: Limit or optimize data consumption
Proxy in WiFi Networks:
Proxies are commonly implemented in enterprise or public WiFi to:
- Enforce content policies
- Control bandwidth
- Monitor network usage
Internet proxy used for more than just privacy—it’s also about control and optimization.
Internet Proxy Example: How It Looks in Action
Let’s say you’re using a proxy to access a U.S.-only streaming service from Europe.
What Happens:
- Your device connects to a U.S.-based proxy server
- The proxy sends the request to the streaming site
- The service sees a U.S. IP and grants access
- The content is routed back through the proxy to your device
This allows you to bypass geo-restrictions while maintaining privacy.
Business Example:
- A company sets up proxies to prevent employees from accessing social media at work and to monitor web traffic for security purposes.
Every internet proxy example has a specific goal—privacy, access control, or content optimization.
Types of Proxy Servers
Different proxies serve different needs. Choosing the right type depends on your use case.
1. Forward Proxy
- Positioned between client and internet
- Used to monitor or control user behavior
2. Reverse Proxy
- Sits in front of servers, managing inbound traffic
- Useful for load balancing and caching
3. Transparent Proxy
- Operates without user awareness
- Common in public WiFi or ISP-level filtering
4. Anonymous Proxy
- Hides IP address but not proxy usage
- Good for basic privacy
5. Elite Proxy
- Hides both IP and proxy usage
- Ideal for high-security operations
Knowing these types helps you choose the right solution for cybersecurity, compliance, or user management.
Advantages and Limitations of Internet Proxies
Pros:
- Improved privacy and anonymity
- Better control over internet usage
- Ability to bypass geo-blocks
- Enhanced performance via caching
Cons:
- May reduce speed
- Can be detected and blocked by websites
- Not always encrypted (depends on protocol)
Choose secure proxies that support HTTPS and regularly update configuration policies.
Proxy Server Security Best Practices
To maximize the benefits and minimize risks:
Tips:
- Use proxies that support HTTPS and encryption
- Regularly update proxy software and firmware
- Monitor logs for suspicious activity
- Avoid free proxies from unknown sources
- Implement authentication for access control
Secure proxies are essential for any cybersecurity framework, especially in regulated industries.
FAQs
1. What is internet proxy?
An internet proxy is a server that routes your traffic through itself to mask your IP, manage content, or increase privacy.
2. What is a proxy server address?
It’s the IP and port of the proxy you configure your device to use for internet access.
3. What is an internet proxy used for?
Used for anonymity, filtering content, security, and accessing restricted resources.
4. What are examples of proxy servers?
Examples include Squid (forward proxy), NGINX (reverse proxy), and public proxy IPs used for bypassing geo-blocks.
5. What’s the difference between proxy and VPN?
A proxy masks web traffic only, while a VPN encrypts all device traffic. VPNs are generally more secure.
Final Thoughts & CTA
Now that you know what is internet proxy, it’s time to consider how proxy servers can fit into your network and security strategy. From performance enhancements to access controls, proxies offer flexibility and protection when used correctly.
👉 Request a Demo with Xcitium Today
Learn how Xcitium can help implement secure, scalable proxy systems tailored to your business needs.