What Is A Vulnerability Assessment?
Vulnerability Assessment Definition: The name suggests is the process of recognizing, analyzing,...

Vulnerability Assessment Definition: The name suggests is the process of recognizing, analyzing,...

Zeus malware (a Trojan Horse malware) is also known as Zeus virus or Zbot. This malware runs on...

It is no doubt that ransomware and its many variants have become a nuisance to our digital online...

Firewall Definition: In the computing world, the terminology firewall security refers to a network...
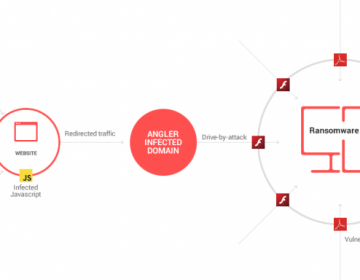
It is no longer news that ransomware is presently one of the most troublesome and challenging...

Most security groups work under the conviction that rapid remediation an episode levels with...

The WannaCry attack announced to the general audience a new threat—ransomware. With the damages...

The rise of online threats is getting advanced, and security experts are equally developing new...

Computer Trojan Virus: Meaning A computer Trojan refers to a program that appears to be harmless,...