Xcitium Zerodwell Works - Block Zero-Day Malware Instantly
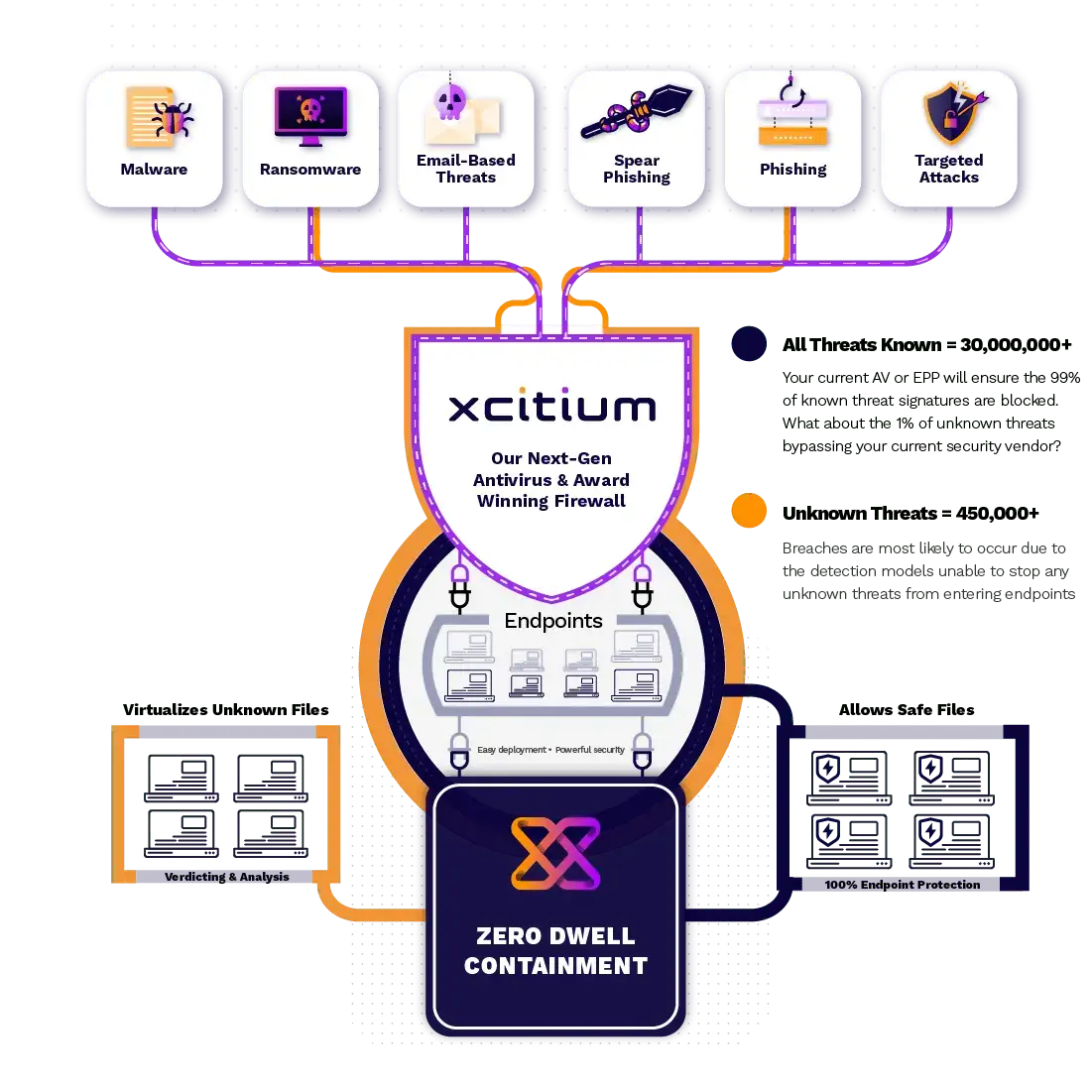
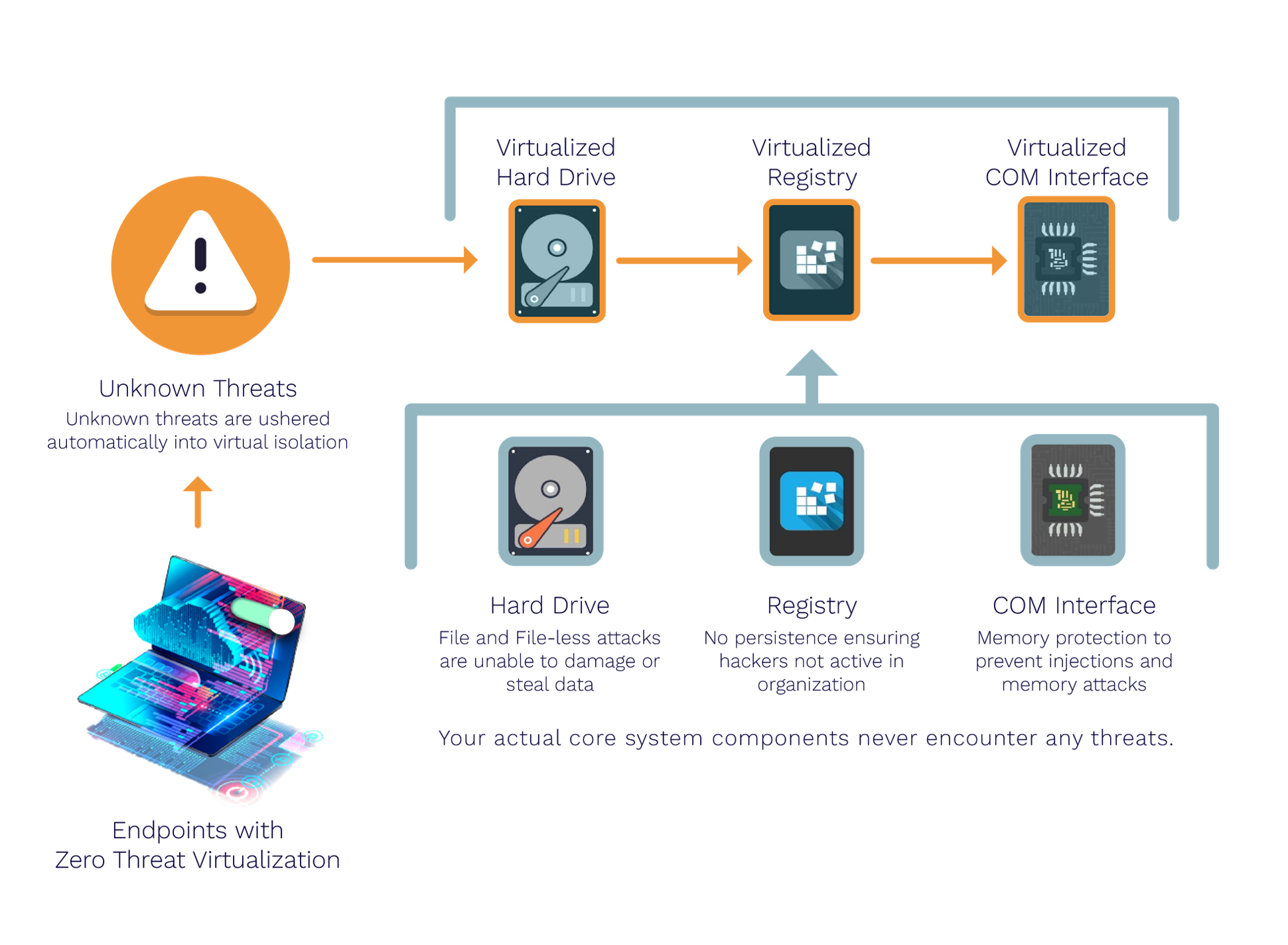
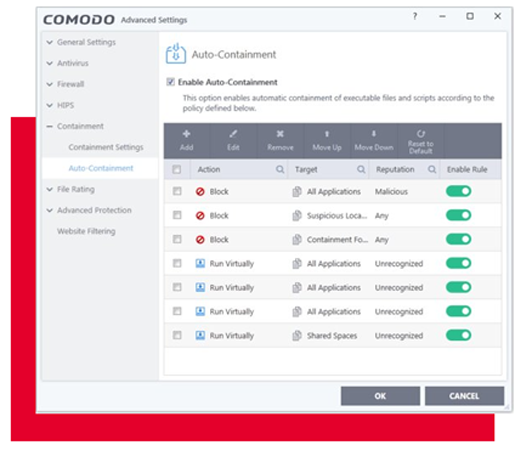
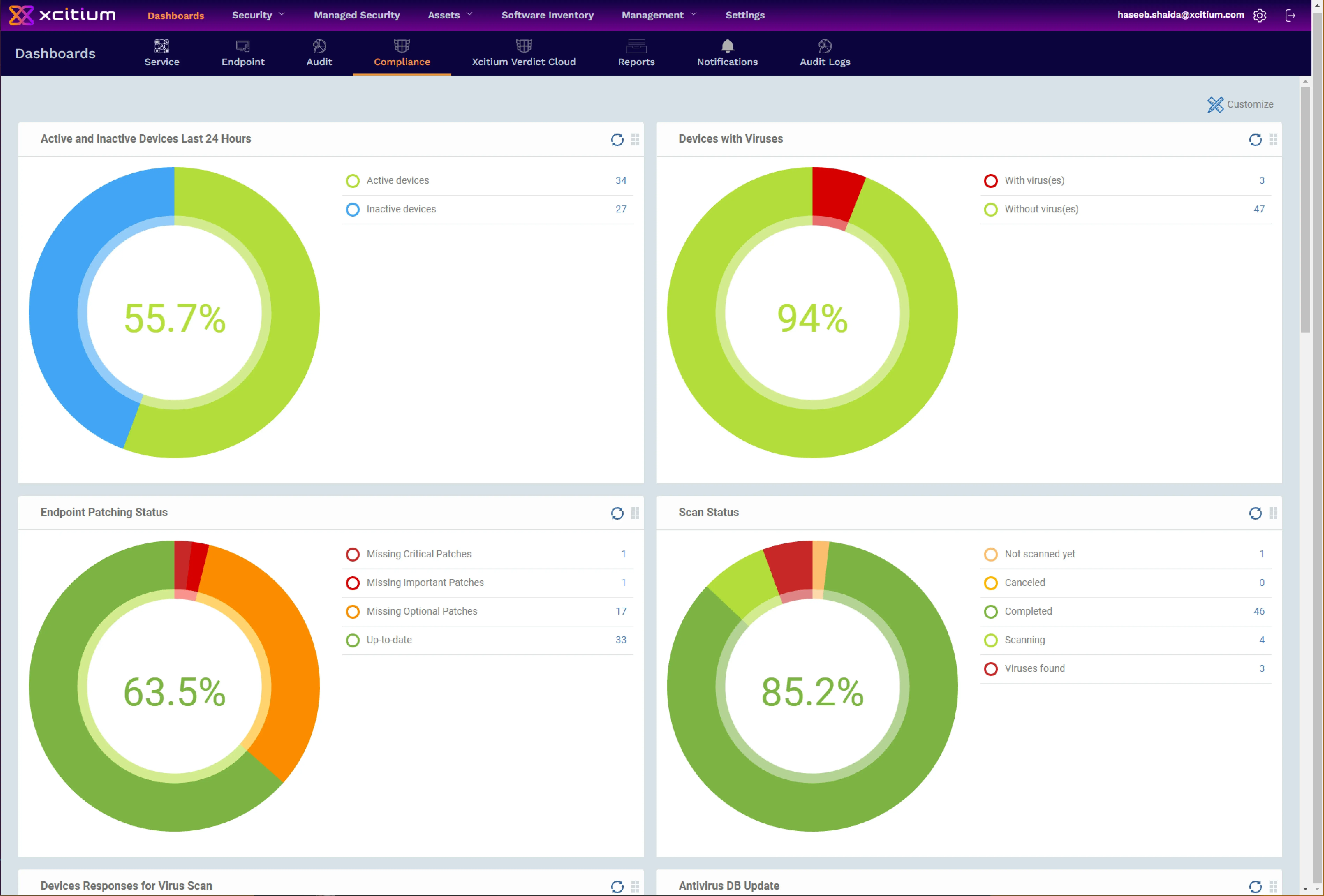
Xcitium ZeroDwell works Containment technology isolates Unknowns to prevent them from damaging endpoints at runtime. This Xcitium ZeroDwell ground-breaking default-deny solution protects first, instantly, and automatically, thereby preventing breaches while allowing users to continue their work without disruption during an Xcitium ZeroDwell endpoint's virtualization.