Extended Detection & Response (XDR)
Experience unparalleled security with Xcitium’s Extended Detection and Response (XDR). Our cutting-edge platform unifies threat detection and response across your network, providing comprehensive visibility and advanced analytics to protect your organization. Leverage automated incident response, AI-driven insights, and continuous support from our cybersecurity experts.
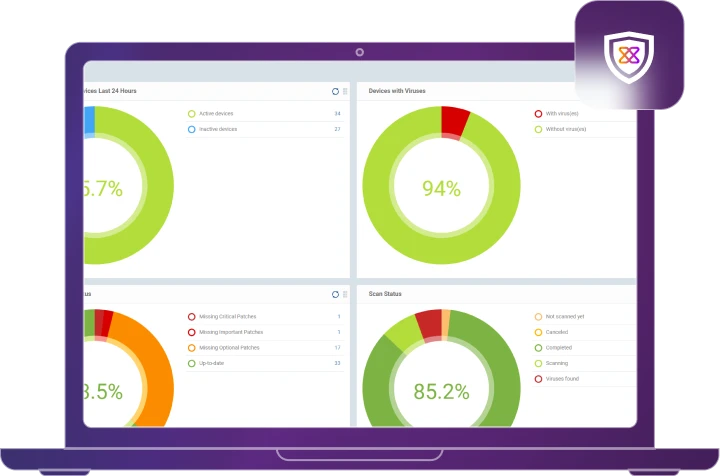
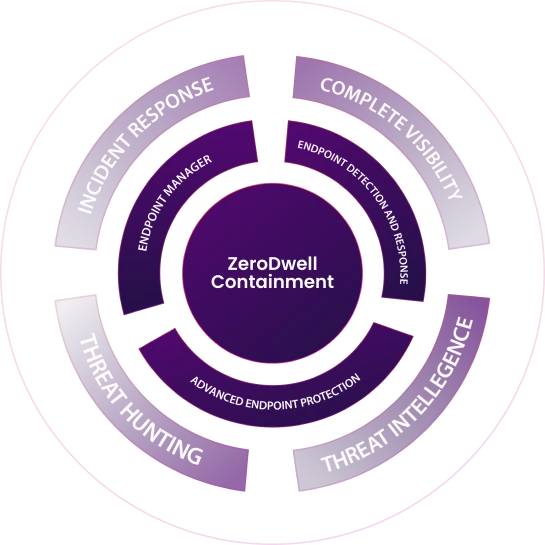
How It Works
Leverage a 24x7x365 team of highly skilled SOC Xcitium Complete XDR analysts to conduct in-depth investigations. Receive Xcitium Complete XDR high-fidelity threat notifications for attacker activity, malicious programs, & suspicious behavior.
Key Features
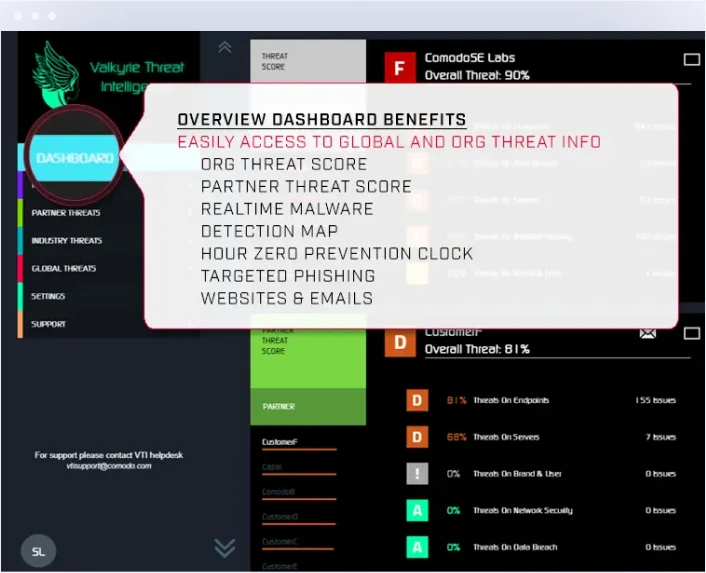
Threat Intelligence Integrations
Receive highly refined internal & external threat intelligence feeds to XDR alert or block Indicators of Compromise. Incorporate Complete XDR your internal intelligence into Xcitium’s Enterprise Platform for added coverage. Our Verdict Cloud integration checks on process execution via hash submission and delivers Xcitium Complete static analysis, kill-chain reporting, & human reverse engineering.
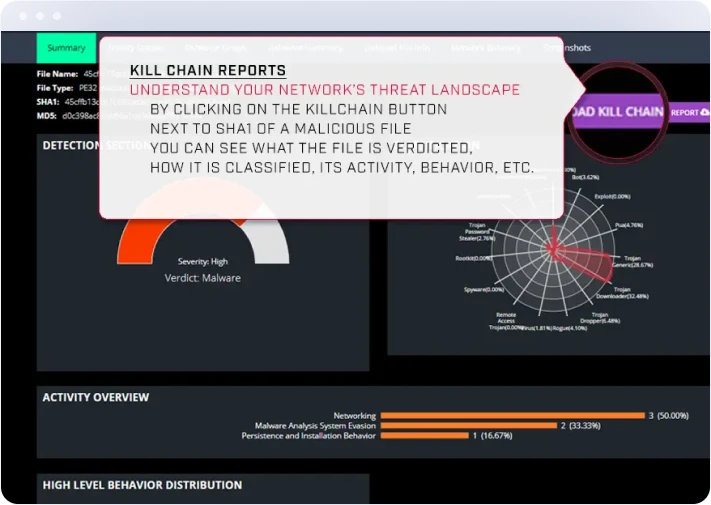
Real-Time Response & Reporting
Xcitium’s XDR platform enables our respondents to automate the forensic collection process, block activity in real-time, isolate endpoints from the network, execute custom commands, and provide live responses to your remote systems for remediation.
Proactive Threat Hunting
Our team of highly trained cybersecurity experts will continuously hunt through generated logs looking for anomalous and suspicious activity across your organization. Your environment will be baselined for known good behavior and you will be alerted on deviations outside those recorded patterns.

Automated Incident Response
Our incident response team is readily available to conduct in-depth forensic investigations. Receive a detailed timeline of attack activity derived from digital forensics. In Xcitium Complete XDR addition to Xcitium Complete Technology telemetry, this includes analysis of artifacts such as $MFT, Windows Event Logs, Registry, Web History, etc. After a breach or incident, our team guides you through the next best steps to protect your XDR endpoints, XDR network, and assets. This Xcitium Complete XDR includes threat neutralization and remediation support.
Eliminate Alert Fatigue
Get high fidelity notifications on file-less attacks, advanced persistent threats and privilege escalation attempts.
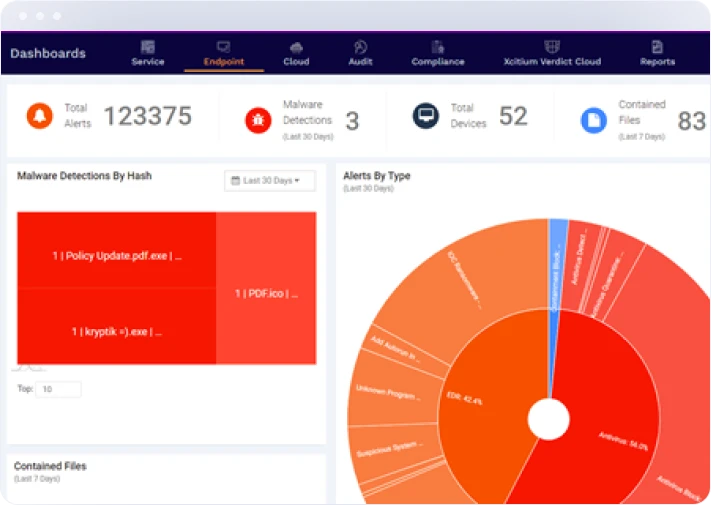
Detailed Reporting
Received detailed reports on threat activity affecting your environment, vulnerability management & insight into compliance reporting.
Benefits
Solution
Why Choose Xcitium?
Xcitium is a leader in cybersecurity, offering innovative solutions to protect against the most advanced threats. Our endpoint security platform combines cutting-edge technology with expert support, ensuring your business stays secure in a constantly evolving threat landscape. Trust Xcitium to safeguard your endpoints and protect your business.





