What Is SOA? A Complete Guide to Service-Oriented Architecture
Updated on November 7, 2025, by Xcitium
In an age where digital transformation drives business success, the ability to connect multiple systems seamlessly is more critical than ever. But how can organizations make their applications communicate effectively without rewriting everything from scratch?
The answer lies in SOA — Service-Oriented Architecture.
SOA provides a modular and flexible way to design, develop, and integrate software systems. It allows different applications — even built with different technologies — to interact through well-defined services. In today’s interconnected IT and cybersecurity landscape, understanding what SOA is has become essential for ensuring data consistency, secure communication, and business agility.
What Is SOA (Service-Oriented Architecture)?
SOA, or Service-Oriented Architecture, is a software design approach where applications are built as a collection of loosely coupled, reusable, and interoperable services. Each service performs a specific function — such as authentication, data retrieval, or transaction processing — and communicates with others using standard protocols like HTTP, SOAP, or REST.
In simpler terms, SOA allows different parts of an organization’s IT environment to work together efficiently, regardless of platform or programming language.
For example:
-
A customer service app can call a payment processing service without knowing how it’s coded.
-
An inventory system can update order data automatically through shared APIs.
This decoupling not only boosts flexibility but also enhances security and scalability, which is why SOA remains foundational in enterprise architecture and cybersecurity frameworks.
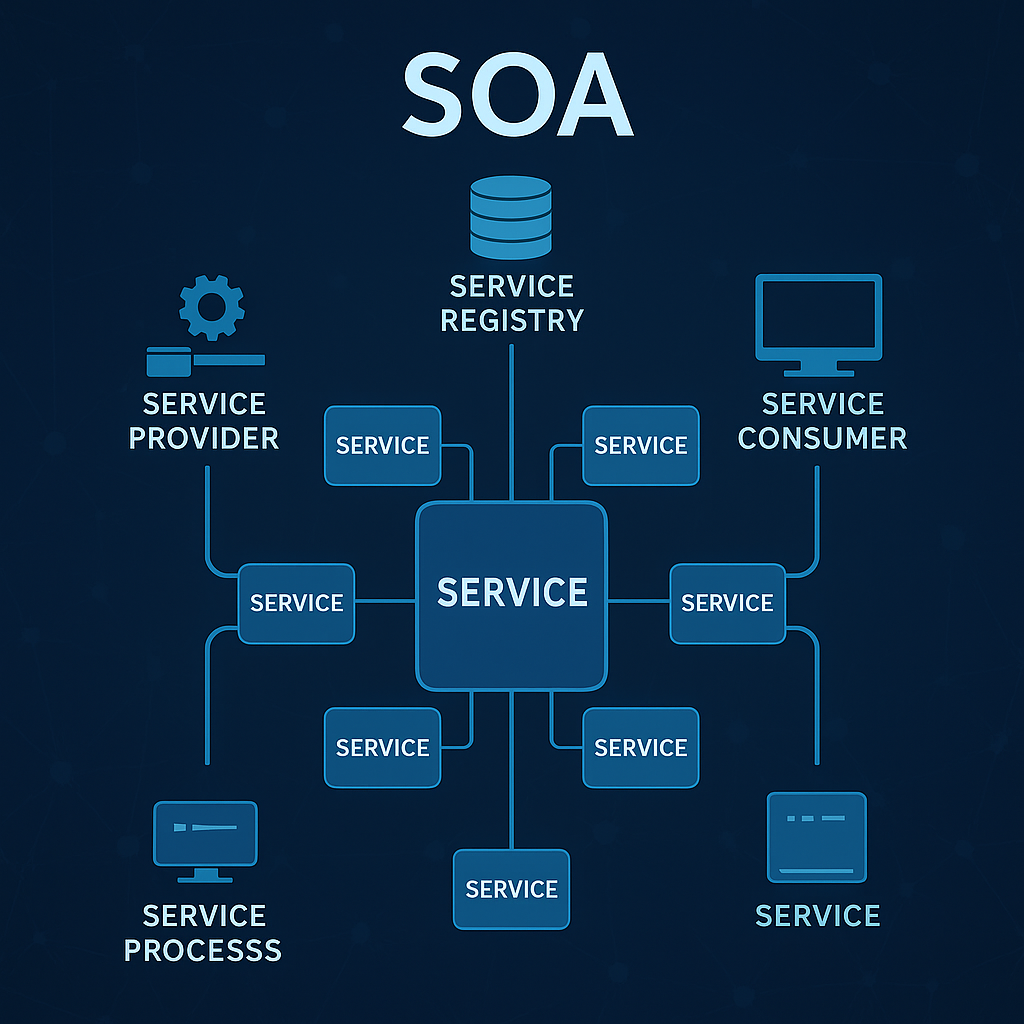
How Does SOA Work?
The SOA model revolves around services — modular building blocks that can be developed, deployed, and reused independently.
Here’s how it typically works:
-
Service Provider – Creates and hosts the service, making it available to consumers.
-
Service Registry – Acts as a directory or catalog where available services are published and described.
-
Service Consumer – The application or system that uses a service to perform a specific task.
Each service communicates using a service contract — a standard interface that defines inputs, outputs, and security policies.
Example:
Imagine a banking system using SOA:
-
The authentication service verifies users.
-
The transaction service processes payments.
-
The notification service sends alerts.
These independent modules can evolve separately — improving maintainability and reducing downtime during updates.
Core Principles of Service-Oriented Architecture
A successful SOA implementation follows several architectural principles that ensure modularity, reliability, and security.
1. Loose Coupling
Services are designed to minimize dependency on other services, making systems more flexible and fault-tolerant.
2. Reusability
Each service is built to serve multiple applications, reducing duplication of effort.
3. Discoverability
Services are published in a registry where consumers can find and connect to them easily.
4. Composability
Multiple services can be combined to form larger business processes or workflows.
5. Interoperability
SOA uses open standards (like XML, SOAP, and REST) to allow diverse systems to interact seamlessly.
6. Security
Each service can enforce its own authentication, authorization, and encryption policies, providing granular control over access.
Components of SOA Architecture
SOA includes several key components that ensure efficient communication and security among services:
| Component | Description |
|---|---|
| Service Interface | Defines how services interact (methods, parameters, protocols). |
| Service Contract | Specifies rules and security policies for data exchange. |
| Service Implementation | The backend logic that performs the defined function. |
| Service Repository/Registry | Stores metadata and makes services discoverable. |
| Message Bus (ESB) | The Enterprise Service Bus (ESB) acts as the communication backbone. |
| Policy Management Layer | Ensures compliance with governance and security standards. |
These components work together to form a secure and efficient service ecosystem.
Benefits of Using SOA
Implementing a Service-Oriented Architecture offers major business and technical advantages:
1. Enhanced Flexibility
Organizations can modify or replace individual services without disrupting the entire system.
2. Improved Scalability
As demand grows, specific services can be scaled independently to handle more load.
3. Cost Efficiency
Reusing existing services minimizes redundant development and lowers maintenance costs.
4. Better Integration
SOA enables legacy systems to connect with modern applications through APIs, promoting interoperability.
5. Stronger Security
By isolating and controlling access at the service level, SOA limits attack surfaces and improves compliance with data protection standards.
6. Business Agility
Businesses can respond faster to changes in market conditions or technology by quickly assembling or modifying services.
SOA vs. Microservices: What’s the Difference?
Many confuse SOA with microservices architecture, but while both share modular principles, they differ in scope and granularity.
| Feature | SOA | Microservices |
|---|---|---|
| Scope | Enterprise-wide integration | Application-level services |
| Communication | Typically uses ESB (SOAP, XML) | Lightweight protocols (REST, JSON) |
| Deployment | Centralized governance | Independent deployment |
| Security | Managed through central policies | Implemented per service |
| Use Case | Large enterprises, multi-system integration | Cloud-native, agile development |
SOA is ideal for enterprises needing to connect diverse systems, while microservices suit modern, agile applications.
Security in Service-Oriented Architecture
Since SOA involves multiple interacting services, securing communication and access is crucial. Common security layers include:
1. Authentication and Authorization
Each service verifies the identity of users or systems before granting access. OAuth 2.0 and SAML are common standards.
2. Encryption
Data is encrypted in transit using TLS/SSL, ensuring sensitive information remains secure between services.
3. Message Integrity
Digital signatures verify that messages are not tampered with during transmission.
4. Security Policies
SOA enforces centralized governance, allowing administrators to define and enforce consistent security policies across all services.
5. Logging and Monitoring
Continuous monitoring and logging of service interactions help detect unauthorized access or anomalies early.
Use Cases of SOA in Cybersecurity and Business
1. Banking and Financial Services
Banks use SOA to integrate payment gateways, KYC verification, and fraud detection systems across different platforms securely.
2. Healthcare
SOA connects patient record systems, appointment scheduling, and insurance verification, maintaining compliance with HIPAA regulations.
3. E-Commerce
Retailers use SOA to link order management, inventory, and shipping systems, ensuring real-time updates and security in transactions.
4. Government and Defense
Public sector systems rely on SOA to share information across agencies while maintaining strict security controls.
5. Cloud Computing and SaaS
Many cloud-based applications are built on SOA principles, providing secure access to distributed resources and APIs.
Challenges in Implementing SOA
Despite its advantages, SOA implementation can be complex if not managed properly.
-
Governance Overhead: Requires strict monitoring and version control.
-
Security Complexity: Multiple endpoints mean more potential vulnerabilities.
-
Performance Bottlenecks: Overuse of the ESB can introduce latency.
-
Integration Costs: Legacy systems may need significant refactoring to adopt SOA standards.
To overcome these challenges, organizations often use automation tools, API gateways, and modern endpoint protection platforms like Xcitium, which monitor and secure service interactions in real time.
Best Practices for Adopting SOA
-
Start with Clear Business Goals – Define the problems SOA will solve before implementation.
-
Establish Governance Policies – Standardize service definitions and security protocols.
-
Implement Strong Access Controls – Enforce role-based access and encryption at every level.
-
Use an API Gateway – Centralize monitoring and secure all service requests.
-
Ensure Scalability – Design for future growth and cloud integration.
-
Automate Testing and Monitoring – Use continuous testing to detect failures and vulnerabilities early.
The Future of SOA in Cybersecurity and Cloud Systems
SOA continues to evolve alongside cloud and hybrid IT infrastructures. In fact, modern architectures like API-first design, zero-trust networks, and service meshes are built on SOA foundations.
With the rise of AI-driven cybersecurity, future SOA systems will automatically detect anomalies, optimize performance, and self-heal against threats.
As organizations shift toward hybrid and multi-cloud environments, SOA’s modular design will remain critical in ensuring secure, efficient interoperability between on-premise and cloud-based systems.
Conclusion
So, what is SOA?
It’s more than just an architecture — it’s a strategy that enables businesses to stay agile, secure, and future-ready.
By breaking complex systems into independent, secure services, Service-Oriented Architecture allows organizations to scale faster, integrate smarter, and protect better.
In today’s digital-first economy, SOA isn’t just about technology — it’s about building a foundation of trust and adaptability.
Ready to Secure Your IT Ecosystem?
Empower your organization with next-gen security and architecture solutions.
👉 Request a Demo at Xcitium and discover how to safeguard every service and endpoint across your enterprise.
FAQs: What Is SOA?
1. What does SOA stand for?
SOA stands for Service-Oriented Architecture, a design model that allows different software systems to communicate and reuse services efficiently.
2. What is the main goal of SOA?
The main goal of SOA is to promote interoperability, reusability, and flexibility across distributed systems while maintaining security and performance.
3. How is SOA used in cybersecurity?
SOA enhances cybersecurity by enabling centralized policy enforcement, secure data exchange, and granular access controls across all connected services.
4. Is SOA still relevant today?
Yes. While microservices are popular, SOA remains the foundation for enterprise-level integration, especially in finance, healthcare, and government sectors.
5. What technologies are used in SOA?
Common SOA technologies include SOAP, REST APIs, XML, JSON, WSDL, and Enterprise Service Bus (ESB) frameworks.