What Is API? The Smart Guide for Cybersecurity and IT Leaders
Updated on July 30, 2025, by Xcitium
Have you ever wondered how your favorite apps—like Google Maps, payment gateways, or Slack—communicate with each other so seamlessly? The secret is in the API. Whether you’re a tech leader, cybersecurity manager, or a CEO navigating digital transformation, understanding what is API is key to unlocking modern digital efficiency and security.
APIs drive everything from login pages to cloud services and mobile apps. And as integrations rise, so does the importance of understanding, managing, and securing them.
What Is API?
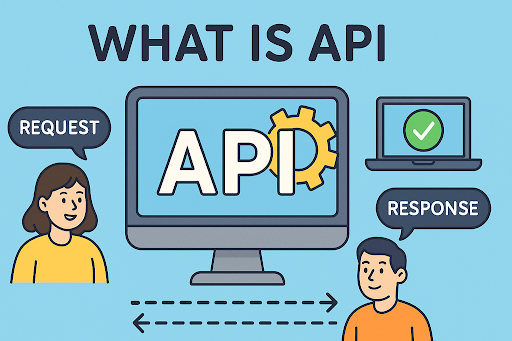
An API (Application Programming Interface) is a set of rules and protocols that allows different software systems to communicate and exchange data.
Think of an API like a restaurant menu. You (the user) request a dish (data/function), the waiter (API) takes your order to the kitchen (server), and then brings your meal back (response).
How Does an API Work?
Let’s break it down step-by-step:
- Request Sent: The client (browser, app, etc.) sends a request to the API.
- Processing: The API processes the request according to pre-defined rules.
- Response Returned: The requested data or function is returned to the client.
Example: A payment app uses an API to verify your bank credentials, retrieve your account info, and complete a transaction—all in seconds.
Common Types of APIs
1. REST (Representational State Transfer)
Most widely used due to simplicity. Operates over HTTP and returns data in JSON format.
2. SOAP (Simple Object Access Protocol)
More rigid and secure, often used in enterprise-level or legacy systems.
3. GraphQL
An API query language developed by Facebook. Offers more flexibility in data requests than REST.
4. Open vs Private APIs
- Open APIs are public and encourage integration (e.g., Twitter API).
- Private APIs are internal and enhance in-house connectivity between systems.
Why APIs Matter in Cybersecurity
With growing cloud adoption, IoT ecosystems, and third-party tools, APIs have become both an opportunity and a risk. Here’s why cybersecurity pros need to pay attention:
🔐 Data Exposure
APIs handle sensitive data—from personal info to payment credentials. Misconfigured APIs can leak this data.
🧰 Attack Surface Expansion
Every new API endpoint adds a potential entry point for hackers.
🧪 Testing Complexity
APIs often change during software updates. If not tested properly, they become vulnerabilities.
🚫 Rate Limiting & Abuse
Without proper controls, APIs can be spammed or exploited by DDoS-style attacks.
Real-World API Use Cases
🏦 Banking & FinTech
- Mobile banking apps use APIs to fetch real-time account data.
- Payment processors (like Stripe or PayPal) use secure APIs for transactions.
🚑 Healthcare
- Hospitals use APIs to share patient data across platforms securely (under HIPAA compliance).
🧑💻 IT & Cybersecurity
- Threat detection platforms use APIs to ingest data from multiple security tools and automate incident response.
Benefits of Using APIs in Business and IT
- ✅ Speed Up Development
- ✅ Enable System Integration
- ✅ Reduce Costs
- ✅ Enhance User Experience
- ✅ Improve Security with Automation
Modern businesses can’t scale without APIs. They enable interoperability across services and automation of complex tasks.
API Security Best Practices
To protect your APIs from common vulnerabilities like Broken Object Level Authorization (BOLA) or injection attacks, follow these security tips:
✔️ Use Authentication & Authorization
Implement OAuth 2.0, API keys, or JWT tokens to control access.
✔️ Validate All Inputs
Prevent injection attacks with strong input validation.
✔️ Rate Limiting
Throttle requests to stop abuse or brute-force attacks.
✔️ Encryption
Use HTTPS/TLS to protect data in transit.
✔️ Monitor & Audit
Log API usage and set up alerts for unusual activity.
Common API Vulnerabilities
| Vulnerability | Description |
| BOLA | Unauthorized access due to improper ID validation |
| Insecure Endpoints | Lack of authentication on some API routes |
| Data Overexposure | Returning too much information in API responses |
| Lack of Rate Limiting | Can lead to brute-force or spam attacks |
🔍 Pro Tip: Use automated API testing and security scanning tools to detect these flaws early.
How to Build an API Strategy
- Map All APIs in Use
Start by identifying internal, public, and third-party APIs. - Align APIs with Business Goals
Don’t build an API just to build one—ensure it serves your process. - Secure by Design
Build in security from day one—not as an afterthought. - Documentation Matters
Ensure your API is well-documented for developers and security teams alike.
Want to safeguard your APIs and integrate smarter?
Xcitium offers secure API management and monitoring solutions that scale with your business.
👉 Request your free Xcitium demo now
Frequently Asked Questions (FAQs)
1. What is an API in simple terms?
An API is a tool that allows software applications to talk to each other and share data or functionality.
2. Are APIs secure?
They can be, but only if designed and managed with strong security measures like authentication, encryption, and rate limiting.
3. What is the difference between REST and SOAP?
REST is simpler and more flexible, while SOAP is more secure and better suited for enterprise environments.
4. Why do businesses use APIs?
APIs speed up development, reduce costs, and allow different systems to work together efficiently.
5. How do I protect APIs from threats?
Use access controls, encrypt data, validate input, and monitor traffic regularly.
Conclusion
Now that you know what an API is, you’re equipped to lead smarter digital strategies. APIs are the glue of the modern web—but with that power comes responsibility. For every integration or efficiency gain, there’s a need for security, governance, and oversight.
APIs aren’t just technical tools—they’re business enablers.
👉 Secure your APIs and explore scalable solutions with Xcitium