What Are JSON Files? A Complete Guide for Tech, Cybersecurity & IT Leaders
Updated on November 14, 2025, by Xcitium
If you’ve worked in IT, cybersecurity, software development, or cloud operations, you’ve likely encountered JSON files countless times. But what are JSON files, and why are they essential for modern systems?
JSON files sit at the core of digital communication today. From APIs and web apps to configuration files and automation tools, JSON quietly powers billions of transactions each day. They’re lightweight, readable, flexible—and increasingly targeted by attackers seeking data exposure or misconfigured systems.
In this guide, you’ll learn what JSON files are, how they work, why organizations use them, and how to protect them from security risks. We’ll break everything down with simple examples, practical tips, and insights tailored for IT managers, cybersecurity teams, and business leaders.
What Are JSON Files? (Primary Keyword)
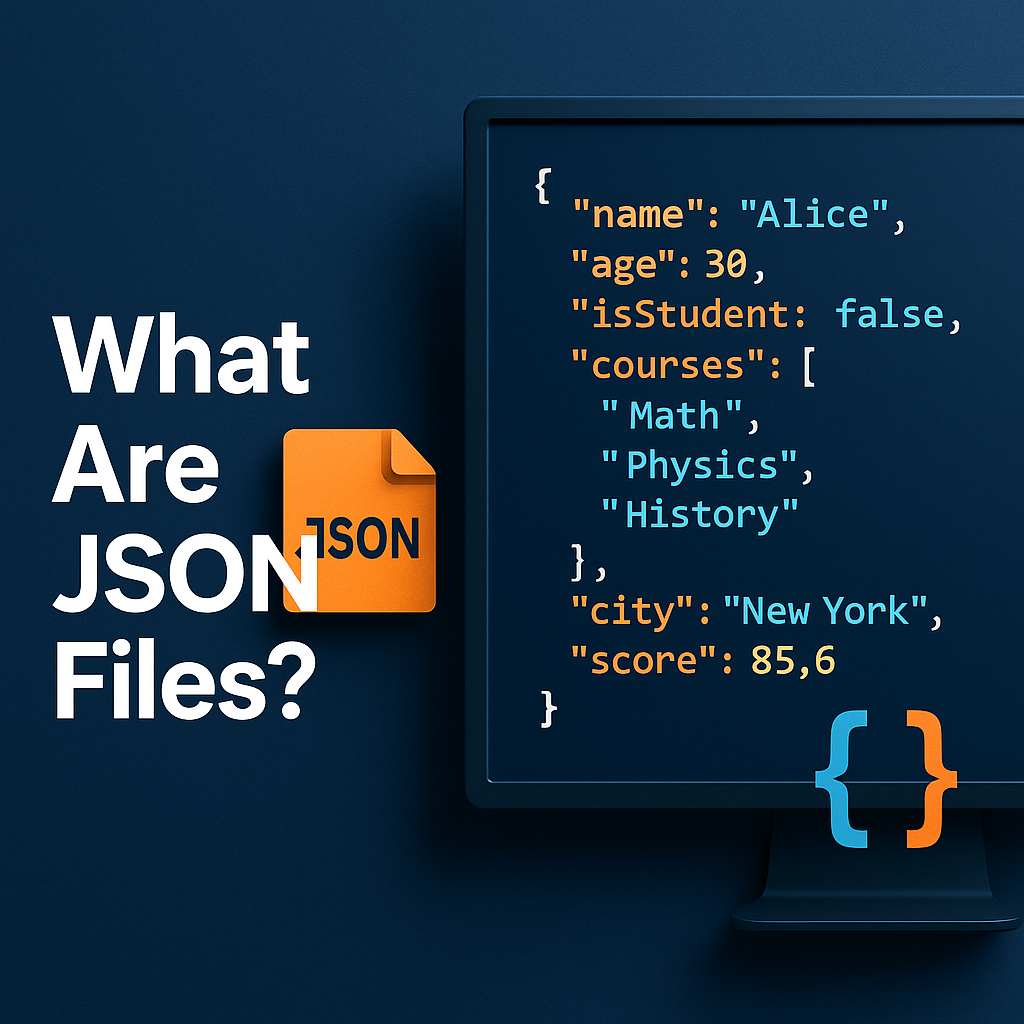
A JSON file is a text-based data format used to store and transmit structured information. JSON stands for JavaScript Object Notation, and although it originated with JavaScript, it is now supported across nearly every programming language.
In simple terms:
A JSON file contains data organized in name–value pairs, arrays, or nested structures, using a lightweight syntax that both humans and machines can read.
JSON is the standard format for modern web APIs, configuration files, system logs, cloud services, and more.
Why JSON Files Are Popular in Modern Computing
JSON files have become the default data format across the internet because they offer:
✔ Human readability
Readable like plain text, making debugging easy.
✔ Lightweight structure
Minimal syntax reduces file size and speeds up processing.
✔ Language independence
Works with Python, JavaScript, Go, Java, C#, PHP, Rust—virtually every language.
✔ Easy integration into APIs
Almost every cloud platform and app uses JSON for requests and responses.
✔ Ideal for configurations
Used in Docker, Kubernetes, CI/CD pipelines, VSCode settings, and many enterprise tools.
These benefits make JSON key to everything from microservices to AI pipelines.
JSON File Structure: How It Works
JSON consists of simple building blocks:
1. Key–Value Pairs
2. Arrays
3. Nested Objects
4. Data Types JSON Supports
-
Strings
-
Numbers
-
Booleans
-
Arrays
-
Objects
-
Null
JSON’s simplicity is what makes it so powerful.
Common Uses of JSON Files in IT and Cybersecurity
JSON is everywhere. Here are the most common use cases:
1. Web APIs (Most Common Use)
APIs like OpenAI, Google Cloud, AWS, GitHub, and internal enterprise APIs all send and receive JSON.
Example API response:
2. Configuration Files
Many platforms store app or system configuration in JSON:
-
Docker Compose
-
Kubernetes manifests
-
VSCode settings
-
NPM package files (
package.json) -
Application settings
3. Logging and Monitoring
Security tools generate logs in JSON because it’s machine-friendly:
-
SIEM systems
-
SOAR tools
-
SOC dashboards
-
Endpoint logs
-
Cloud audit logs
4. Data Storage and Transfer
JSON is widely used in:
-
NoSQL databases (MongoDB, CouchDB)
-
Data streams (Kafka, Firehose)
-
Machine learning pipelines
-
Cloud storage objects
5. Automation and Scripting
DevOps and cybersecurity automation depend on JSON to:
-
Replace environment variables
-
Send configuration updates
-
Build API-driven workflows
-
Trigger automated alerts
Advantages of JSON Files for Modern Organizations
1. Easy to Read and Modify
Great for teams managing rapid application changes.
2. Small File Size
Faster transmission and lower bandwidth cost.
3. Universally Supported
Every major IT and security system uses JSON.
4. Flexible Structure
Works for simple and complex data models.
5. Perfect for Hybrid and Cloud Environments
JSON is cloud-native by design.
Security Risks Associated With JSON Files
While JSON is incredibly useful, it also introduces security risks if not properly protected.
1. Sensitive Data Exposure
JSON often stores credentials, API keys, tokens, or user information.
2. Misconfigured Permissions
Cloud storage buckets and server locations can expose JSON files publicly.
3. API Vulnerabilities
If JSON requests aren’t validated, attackers can inject malicious data.
4. JSON Injection Attacks
Attackers manipulate JSON content to exploit backend systems.
5. Logging Data Leaks
Improperly redacted JSON logs can contain:
-
Passwords
-
Tokens
-
PII
-
Internal IP addresses
How to Secure JSON Files: Best Practices for Cybersecurity Teams
To prevent data breaches and API attacks, follow these steps:
1. Encrypt JSON Files at Rest and in Transit
Use:
-
TLS 1.2+
-
AES-256
-
HTTPS-only endpoints
Never store JSON files in plain text on public servers.
2. Mask Sensitive Data
Before generating logs or exporting files:
-
Hash passwords
-
Remove API keys
-
Redact tokens
-
Truncate PII
3. Implement Access Controls
Use:
-
IAM roles
-
RBAC
-
Zero Trust security
-
Principle of least privilege
4. Validate All JSON Input
Prevent JSON injection using:
-
Strict schema validation
-
Whitelisting allowed keys
-
Rejecting unexpected data types
Tools such as OpenAPI, JSON Schema, and OWASP validation controls help significantly.
5. Monitor Access With SIEM Tools
Track:
-
Unauthorized API calls
-
Anomalous JSON payloads
-
Suspicious data exports
-
Privilege escalations
6. Use API Gateways and WAF Rules
Block malicious JSON traffic before it hits your backend.
JSON Files vs XML vs YAML: What’s the Difference?
| Feature | JSON | XML | YAML |
|---|---|---|---|
| Readability | High | Low | High |
| File Size | Small | Large | Small |
| Complexity | Simple | Complex | Medium |
| Best Use | APIs & configs | Documents | DevOps configs |
| Security Risk | Medium | High | Medium |
JSON strikes the best balance for modern application ecosystems.
Real-World Examples of JSON in Enterprise Environments
✔ Cloud Services
AWS IAM policies, Lambda functions, and S3 permissions all use JSON.
✔ Security Tools
EDR, SIEM, SOAR, vulnerability scanners, and firewalls export logs in JSON.
✔ DevOps Pipelines
GitHub Actions, GitLab CI, Azure DevOps rely heavily on JSON configuration.
✔ Web Applications
Frontend and backend communication flows entirely through JSON APIs.
JSON is the backbone of modern automation, security frameworks, and data exchange.
How to Open and Edit JSON Files
1. Any Text Editor
-
Notepad
-
Notepad++
-
Sublime
-
VSCode (recommended)
2. Development Tools
-
IntelliJ
-
PyCharm
-
Visual Studio
-
JetBrains Fleet
3. Online JSON Viewers/Formatters
Helps validate syntax and beautify output.
Best Practices for IT Teams Working With JSON Files
-
Always validate JSON before deployment
-
Use version control (like Git)
-
Enable change tracking and audit logs
-
Follow naming conventions
-
Use consistent indentation
-
Remove unused keys
Conclusion: JSON Files Are the Foundation of Modern Digital Systems
Understanding what JSON files are is essential for anyone working in IT, cybersecurity, DevOps, cloud engineering, or enterprise technology. JSON is simple yet powerful, making it the default structure for transmitting data across apps, APIs, and cloud systems.
But with its widespread use comes increased security risk. Protecting JSON files—through encryption, validation, monitoring, and Zero Trust principles—is critical for safeguarding your organization’s data.
Want stronger protection across your endpoints, APIs, and cloud workloads?
👉 Secure your environment with Xcitium’s ZeroDwell Containment Platform.
Request a free demo today:
🔗 https://openedr.platform.xcitium.com/register/
FAQ: What Are JSON Files?
1. Are JSON files safe?
Yes, but only if encrypted, validated, and stored securely. JSON can expose sensitive data if misconfigured.
2. What are JSON files used for?
APIs, logs, configurations, cloud services, automation scripts, and database storage.
3. Can a JSON file contain malware?
Not directly, but JSON injection or malicious payloads can compromise backend systems.
4. How do I open a JSON file?
Use VSCode, Notepad, any IDE, or online JSON viewers.
5. Is JSON better than XML?
For most modern applications, yes. JSON is smaller, faster, and easier to read.