What Is Port Mapping? A Complete Guide for Networking and Security
Updated on September 29, 2025, by Xcitium
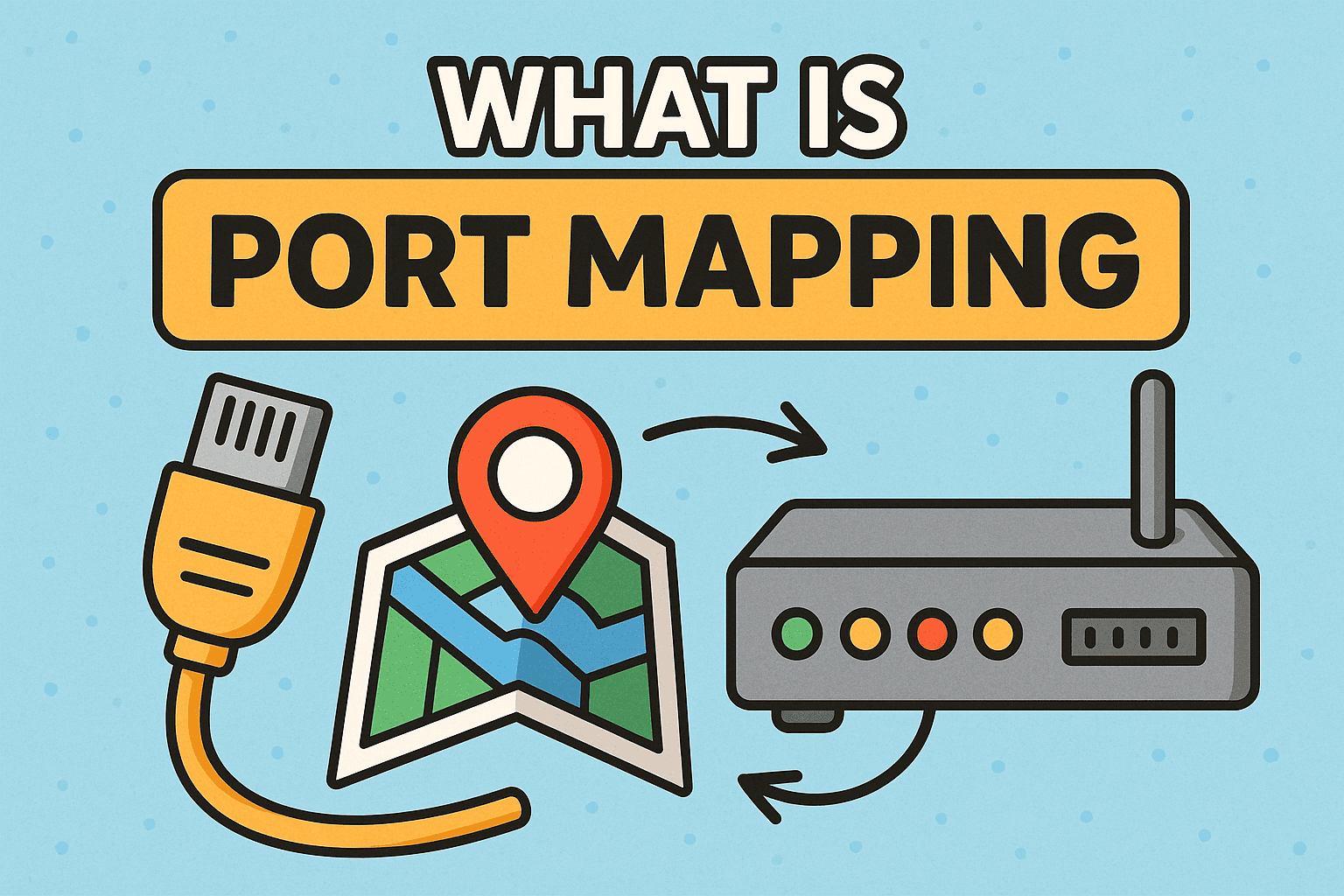
If you’ve ever set up a router, hosted a server, or managed corporate networks, you’ve likely encountered the term port mapping. But what is port mapping exactly, and why is it so important in modern networking?
Introduction: Why Ask “What Is Port Mapping?”
In simple terms, port mapping allows external devices to communicate with internal devices across a private network. While it enables services like gaming, file sharing, or remote access, it also introduces potential cybersecurity risks if not properly managed.
For IT managers, cybersecurity experts, and business leaders, understanding port mapping is essential to balance connectivity, performance, and security.
1. What Is Port Mapping?
Port mapping, also known as port forwarding, is a networking technique that directs communication requests from one address and port number to another.
In practice:
-
It lets devices outside your network (like the internet) reach devices inside your private LAN.
-
A router translates incoming requests on specific ports and sends them to designated devices.
Think of it as a digital receptionist: when data arrives at your network, port mapping decides which “room” (device or application) it should go to.
2. How Does Port Mapping Work?
Here’s a step-by-step breakdown:
-
A request comes from the internet to your public IP address on a specific port (e.g., port 80 for web traffic).
-
Your router checks its port mapping rules.
-
If a mapping exists, it forwards the traffic to the corresponding private IP address and port inside your network.
-
The designated device or application receives the traffic and responds.
This translation process is what enables external users to access internal services securely (if configured correctly).
3. Common Use Cases for Port Mapping
Port mapping is widely used in both home and enterprise networks.
-
Remote Desktop Access: Connect to office PCs or servers from outside the network.
-
Hosting Web Servers: Allow external users to reach internal websites.
-
Online Gaming: Enable multiplayer game servers to communicate across NAT (Network Address Translation).
-
VoIP Services: Support internet-based phone calls by routing traffic properly.
-
IoT Devices: Manage cameras, smart devices, and sensors remotely.
For IT managers, proper port mapping ensures seamless access without compromising security.
4. Static vs Dynamic Port Mapping
Not all port mappings are the same.
-
Static Port Mapping: Manually assigns external ports to internal devices. Best for servers and applications that require predictable access.
-
Dynamic Port Mapping: Assigned automatically by Universal Plug and Play (UPnP). Convenient but risky if misused.
👉 Businesses typically prefer static mapping for control and accountability, while consumers often rely on dynamic mapping for convenience.
5. Security Risks of Port Mapping
While port mapping improves connectivity, it also expands the attack surface for cybercriminals.
Common Risks Include:
-
Unauthorized Access: Open ports can expose sensitive devices.
-
Port Scanning Attacks: Hackers scan for open ports to exploit vulnerabilities.
-
Malware Infiltration: Exposed devices may serve as entry points.
-
Compliance Violations: Improper configurations may breach GDPR, HIPAA, or PCI DSS rules.
For cybersecurity teams, improperly managed port mapping is a red flag.
6. How to Secure Port Mapping
Organizations must balance accessibility with protection.
Best Practices:
-
✅ Only open ports that are absolutely necessary.
-
✅ Use firewall rules to limit access by IP address.
-
✅ Deploy VPNs for secure remote access instead of direct port exposure.
-
✅ Regularly scan for open ports with tools like Nmap.
-
✅ Disable UPnP in enterprise environments to prevent automatic risky mappings.
-
✅ Monitor logs for unusual traffic.
These steps help IT managers minimize risks while maintaining connectivity.
7. Port Mapping vs NAT vs Port Triggering
It’s easy to confuse related networking terms, but here’s the difference:
-
NAT (Network Address Translation): Converts private IP addresses to public ones. Port mapping is a subset of NAT.
-
Port Mapping/Forwarding: Directs specific external traffic to internal devices.
-
Port Triggering: Temporarily opens ports when an outbound request is made, closing them when not in use.
👉 For businesses, port mapping offers stability, while port triggering offers flexibility but less predictability.
8. Port Mapping in Business Environments
Enterprise use of port mapping is different from home setups. IT teams use it for:
-
Secure Remote Access: Connecting branch offices and remote workers.
-
Application Hosting: Ensuring customers can access internal web apps.
-
Testing Environments: Allowing external developers temporary access.
-
IoT Integration: Managing sensors, industrial machines, or medical devices.
Here, documentation and policy enforcement are key to preventing misconfigurations.
9. Real-World Example of Port Mapping
Imagine a company hosting a customer portal on an internal server:
-
Public IP receives a request on port 443 (HTTPS).
-
Router forwards it to the internal server’s IP (192.168.1.100).
-
Employees and customers access the service securely from anywhere.
Without port mapping, the server would be invisible to the outside world.
10. Future of Port Mapping and Networking Security
As networking evolves, port mapping may look different:
-
Cloud Services: Cloud-native applications reduce the need for manual port forwarding.
-
Zero Trust Architectures: Minimize exposed ports with identity-based access.
-
AI-driven Monitoring: Automated detection of suspicious port activity.
-
IPv6 Adoption: May simplify or eliminate some port forwarding needs due to direct addressing.
Still, port mapping remains a critical concept in 2025 for legacy and hybrid networks.
Quick Port Mapping Checklist
✅ Understand what services need external access
✅ Use static port mapping for critical applications
✅ Disable UPnP in business environments
✅ Restrict port access with firewalls and VPNs
✅ Regularly monitor and audit open ports
FAQs on Port Mapping
1. What is port mapping in simple terms?
It’s a process that lets outside devices connect to specific devices or services inside your private network.
2. Is port mapping the same as port forwarding?
Yes. The terms are often used interchangeably in networking.
3. Is port mapping safe?
It can be safe if properly configured with firewalls, VPNs, and strong access controls. Otherwise, it poses risks.
4. Do businesses still use port mapping with cloud services?
Yes, though many cloud-native services reduce reliance on manual mappings. Hybrid setups still need them.
5. Can hackers exploit open ports?
Yes. Hackers often scan for open ports to launch attacks. That’s why limiting exposure is critical.
Final Thoughts + Call to Action
Asking “what is port mapping?” is more than a networking curiosity—it’s about understanding a process that powers connectivity while introducing security challenges.
For IT managers, cybersecurity leaders, and executives, port mapping is both a tool and a risk. When properly configured, it enables smooth operations and secure access. When ignored, it opens doors for attackers.
🚀 Ready to strengthen your organization’s network security?
Request a demo of Xcitium’s advanced cybersecurity solutions today and gain control, visibility, and peace of mind.