What Is a Proxy? The Smart Guide for Cybersecurity and IT Leaders
Updated on July 30, 2025, by Xcitium
With cyberattacks on the rise and data breaches making headlines weekly, it’s natural to wonder: how exposed are we online? Whether you’re an IT manager, a CEO, or a cybersecurity professional, understanding what a proxy is can significantly improve your organization’s digital privacy and control.
From enhancing security to bypassing geo-restrictions, proxies are powerful tools with a wide range of uses. In this guide, we’ll demystify proxies—how they work, types, benefits, and how to use them securely in modern enterprise environments.
What Is a Proxy?
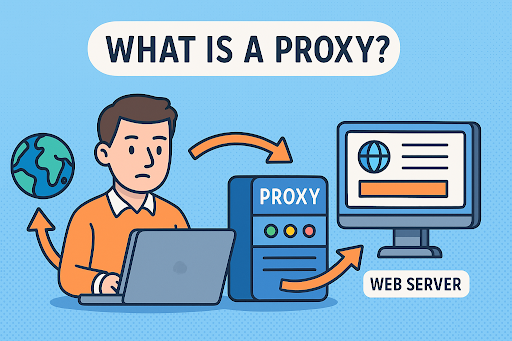
A proxy—or proxy server—is an intermediary between a user’s device and the internet. When you use a proxy, your internet traffic is routed through the proxy server before reaching its final destination. This hides your actual IP address and can enhance privacy, control, and performance.
In simple terms, it’s like asking someone else to speak on your behalf. The website sees the proxy, not you.
How Does a Proxy Work?
Here’s how a proxy functions step-by-step:
- You send a request (e.g., to access a website).
- The proxy server receives the request and changes your IP.
- It forwards the request to the target server using the proxy’s IP.
- The response is received by the proxy and sent back to you.
This creates a protective buffer between your device and the internet, offering anonymity and control.
Types of Proxy Servers
Not all proxies are the same. Here’s a breakdown of the most commonly used types:
1. Forward Proxy
Routes traffic on behalf of users inside a network. Commonly used to monitor employee browsing or block access to specific sites.
2. Reverse Proxy
Sits in front of web servers and routes incoming traffic to backend systems—helpful for load balancing and DDoS protection.
3. Transparent Proxy
Used mostly for content filtering; users are unaware their traffic is being filtered or logged.
4. Anonymous Proxy
Hides your IP address but reveals you are using a proxy—ideal for privacy-conscious browsing.
5. High Anonymity Proxy (Elite Proxy)
Doesn’t identify itself as a proxy and completely hides your identity.
Proxy vs VPN: What’s the Difference?
| Feature | Proxy | VPN (Virtual Private Network) |
| Encryption | Usually none | End-to-end encryption |
| Speed | Faster (less overhead) | Slower (due to encryption) |
| IP Masking | Yes | Yes |
| Cost | Often free or low-cost | Usually paid |
| Ideal Use | Content access, basic anonymity | Secure data transmission, remote work |
Conclusion: Use proxies for lightweight tasks like geo-unblocking, and VPNs for sensitive, encrypted activities.
Why Businesses Use Proxies
Proxies aren’t just for hiding your IP—they’re essential for enterprise-grade cybersecurity and performance optimization.
🔐 Enhance Privacy
Proxies mask employee IPs, protecting internal infrastructure from malicious actors.
🧠 Control Internet Usage
IT managers can monitor and restrict access to non-business websites during work hours.
🌍 Bypass Geo-Restrictions
Proxies help access region-locked content or services during global operations.
🛡️ Improve Security
Reverse proxies can detect and mitigate DDoS attacks, while forward proxies shield internal systems from exposure.
Benefits of Using Proxies in Cybersecurity
- ✅ Improved Network Performance
- ✅ Load Balancing & Caching
- ✅ Content Filtering & Monitoring
- ✅ Anonymity for Threat Analysis
- ✅ Risk Mitigation for Web Crawlers & Bots
Proxies are especially useful for red team exercises, threat intelligence gathering, and compliance auditing.
Real-World Example: Proxy in Action
A cybersecurity firm needed to collect threat intelligence without exposing its analysts. By deploying a high-anonymity proxy, they were able to monitor hacker forums and dark web listings without revealing their location—keeping operations secure while staying invisible.
Common Proxy Risks and How to Avoid Them
While proxies are powerful, they’re not foolproof. Misconfigured proxies or untrusted public proxies can open the door to:
- Data leaks
- Man-in-the-middle (MITM) attacks
- Unauthorized access to network resources
👉 Best Practices:
- Always use reputable proxy providers
- Implement firewall and DLP integration
- Enforce access control policies
- Regularly audit proxy server logs
How to Choose the Right Proxy
When selecting a proxy solution, consider:
- ⚙️ Purpose: Browsing, scraping, security, or load balancing?
- 🌍 Geolocation Needs: Do you need to mask location?
- 🛡️ Security Level: Will it handle sensitive data?
- 📈 Scalability: Can it support your user load?
Need to enhance privacy, filter content, or secure your endpoints?
Discover how enterprise-grade proxies can power up your cybersecurity framework.
👉 Request a free Xcitium demo today
Frequently Asked Questions (FAQs)
1. What is a proxy and why is it used?
A proxy is a server that acts as a middleman between a user and the internet. It’s used for privacy, content control, and security.
2. Is using a proxy safe?
Yes, when using trusted proxies with proper configuration. Avoid free, public proxies for sensitive data.
3. Can a proxy hide my IP address?
Absolutely. Proxies mask your real IP address and replace it with their own, providing anonymity.
4. What is the difference between proxy and firewall?
A proxy manages outbound/inbound web traffic, while a firewall blocks unauthorized access to or from private networks.
5. Should I use a proxy for cybersecurity tasks?
Yes. Proxies are excellent tools for safely gathering threat intel, running red team simulations, and managing secure traffic.
Conclusion
Now that you understand what a proxy is, it’s clear they serve far more than basic anonymity. From protecting user data to managing network performance and enhancing threat detection, proxies are a vital asset in any IT or cybersecurity strategy.
👉 Don’t leave your digital perimeter exposed.
Book your Xcitium proxy demo today and gain control, security, and peace of mind.










![what is wireless lan]](https://www.xcitium.com/blog/wp-content/uploads/2025/07/what-is-wireless-lan.png)

