Why PII Is a Top Concern in Data Security
Updated on June 9, 2025, by Xcitium

What is PII and why is it the cornerstone of modern data protection strategies? In 2024 alone, over 422 million individuals were affected by data breaches exposing sensitive personal information. For cybersecurity professionals, IT managers, and executives, protecting Personally Identifiable Information (PII) isn’t just a best practice—it’s a regulatory mandate and reputational imperative.
What is PII? Definition and Context
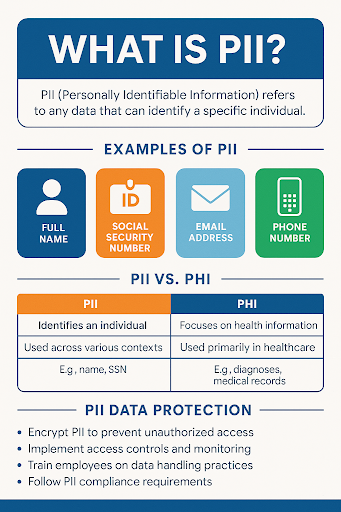
PII, or Personally Identifiable Information, refers to any data that can be used to identify, contact, or locate a single person, either directly or indirectly.
Common PII Examples
- Direct identifiers: Name, Social Security number, passport number
- Indirect identifiers: Date of birth, zip code, IP address, biometrics
- Contact details: Email, phone number, home address
- Financial information: Bank account numbers, credit card details
- Login credentials: Usernames, passwords
In the context of PII data protection, the more sensitive or unique the data, the greater the risk—and responsibility—attached to its handling.
PII vs PHI: What’s the Difference?
PII and PHI are both critical in compliance conversations, but they serve different regulatory and operational contexts.
| Feature | PII (Personally Identifiable Info) | PHI (Protected Health Info) |
| Definition | Any data identifying a person | Health data linked to identity |
| Governing Law | GDPR, CCPA, GLBA, etc. | HIPAA in the U.S. |
| Industry Focus | All sectors | Healthcare, insurance |
| Examples | SSN, IP address, name | Diagnoses, lab results, health records |
Understanding PII vs PHI is key for organizations operating in sectors like healthcare, finance, education, and e-commerce.
Why PII Matters to Cybersecurity and Business
Failing to secure PII can lead to:
- Legal penalties from GDPR, HIPAA, CCPA, and more
- Financial losses due to fraud or ransomware attacks
- Loss of consumer trust and reputational damage
- Operational disruption following breach investigations
From a cybersecurity perspective, PII is a prime target for hackers, often leveraged in identity theft, phishing, and social engineering attacks.
PII Compliance Requirements: What You Need to Know
Compliance is not optional. Here are the major PII compliance requirements based on global standards:
1. GDPR (EU)
- Consent must be clear and unambiguous
- Right to access, correct, and delete PII
- Data minimization and purpose limitation
2. CCPA (California)
- Right to know what PII is collected and shared
- Opt-out of data sales
- Strict notice and breach disclosure requirements
3. HIPAA (U.S. Healthcare)
- Only for PHI but overlaps when PII is present in health data
- Requires administrative, technical, and physical safeguards
4. GLBA (U.S. Financial Services)
- Financial institutions must explain data-sharing practices
- Requires secure handling of non-public personal information
Companies must regularly audit systems, update privacy policies, and train staff to ensure full compliance.
How to Protect PII Data: Best Practices
To meet compliance and defend against threats, follow these PII data protection strategies:
1. Data Encryption
- Use AES-256 encryption for both data at rest and in transit.
2. Access Controls
- Implement role-based access and multi-factor authentication.
3. Data Minimization
- Only collect what’s necessary; dispose of data that’s no longer needed.
4. Regular Risk Assessments
- Conduct vulnerability scans, penetration tests, and data mapping exercises.
5. Employee Training
- Educate staff on phishing, secure sharing, and safe storage of PII.
6. Incident Response Plan
- Have a clear process for detecting, reporting, and resolving data breaches.
Real-World PII Breach Examples
- Equifax (2017): 147 million PII records exposed due to unpatched software
- Facebook (2019): 530 million users’ data leaked, including phone numbers and emails
- T-Mobile (2021): Personal data of over 40 million customers stolen
These incidents show that even large enterprises can fail if security measures and compliance protocols are neglected.
Action Steps for Cybersecurity and IT Teams
- Conduct a PII audit across all platforms
- Use data classification to identify risk levels
- Deploy DLP (Data Loss Prevention) solutions
- Integrate SIEM systems to monitor for unusual data access patterns
- Establish zero-trust architecture to control access dynamically
Frequently Asked Questions (FAQ)
1. What does PII stand for?
PII stands for Personally Identifiable Information—any data that can be used to identify an individual.
2. What are examples of PII?
Names, SSNs, email addresses, IP addresses, biometric data, and financial records.
3. What is the difference between PII and PHI?
PII is general personal data, while PHI is health-related personal information covered by HIPAA.
4. What laws regulate PII?
Common regulations include GDPR (EU), CCPA (California), HIPAA (U.S.), and GLBA (U.S. financial services).
5. How can businesses protect PII?
By using encryption, access controls, staff training, data minimization, and incident response planning.
Final Thoughts: Why PII Protection is a Business Priority
Understanding what is PII is more than a compliance checkbox—it’s a critical part of safeguarding your brand, clients, and operational continuity. As threat actors become more sophisticated, your commitment to PII data protection must be proactive, continuous, and built into your digital DNA.
Don’t wait for a breach to take PII seriously.
👉 Request a Demo from Xcitium and Secure Your PII Infrastructure Today!