History of EDR
EDR security was first coined by Anton Chuvakin, research director at Gartner, in July 2013. Endpoint threat Detection and Response is "the equipment that significantly focuses on identifying and exploring malicious activities and other issues on the endpoints."
This is a new category of solutions. However, the grouping of solutions is termed Endpoint Detection Response; this is sometimes compared to Advanced Threat Protection (ATP) in correspondence to overall security capabilities.
It is a rising innovation that requires constant checking and reaction to cutting-edge dangers. It is a type of advanced risk security.
EDR tools are used to test computers and networks for security issues. They provide an overview of the current state of a network, making it easy to detect vulnerabilities. They also allow you to view detailed information about the computer's security status, including system, network, and server information.
Attackers are always looking for new strategies to defraud and damage organizations. Your employees' off-site devices can be one of the entry points used to penetrate your network. With remote working now a common practice around the world, it's no surprise that endpoints are getting more and more vulnerable. An uneven endpoint security detection layer between your network and attackers can put your critical assets at risk.
For this reason, your response security teams need to put proper endpoints and cybersecurity protection measures in place. After all, malicious hackers are constantly lurking to take advantage of your existing detection vulnerabilities.

EDR Software allows you to visualize threats in a detailed timeline while instantaneous alerts keep you informed if an attack occurs. It helps you in preventing malicious threats before they can even harm your Windows endpoint device.
This tool is a powerful event analysis tool that monitors and detects malicious events on Windows endpoints.
How Does Endpoint Detection Response Work?
EDR works by observing endpoint and system occasions and recording the data in a focal database that facilitates examination, location, examination, detailing, and alarming.
Continuous observation and recognition are encouraged using examination instruments, which distinguish assignments that can enhance security by diverting regular attacks, encouraging early ID of progressing attacks - including insider dangers and outside attacks- and empowering quick reactions to identified attacks.
Not all security tools work in a similar way or offer an indistinguishable range of abilities from others in the space.
For example, some endpoint detection and response apparatuses perform more examination on the operator. In contrast, others conduct most information investigations on the backend using administration support.
Others fluctuate in gathering timing and scope or their capacity to coordinate with threat intelligence providers. However, all endpoint recognition and reaction instruments play out similar fundamental capabilities for a similar reason: to give way to consistent investigation to promptly recognize, identify, and avoid propelled malicious threats.
NOT JUST TOOLS, BUT CAPABILITIES
While Anton Chuvakin authored the term EDR, keeping in mind the end goal to describe a set of instruments, the time may likewise be utilized to depict the capacities of equipment with a substantially more extensive arrangement of security works as opposed to showing the device itself.
For example, a device may offer endpoint detection location and reaction notwithstanding application control, information encryption, device control, and encryption, user privileges, control of network access, and a range of different capacities in EDR products.
Equipment, both those delegated endpoint detection location and reaction devices and those offering cybersecurity as a component of a more extensive arrangement of capacities, are reasonable for many endpoint permeability utilization cases. Anton Chuvakin names a range of endpoint perceivability use cases falling inside three more extensive classes in Endpoint Detection Response:
- Information search and examination
- Suspicious action identification
- Exploration of data
Most endpoint protection and reaction devices address the reaction part of these capacities through advanced investigation that distinguishes designs and identifies irregularities, for example, uncommon procedures, odd or unrecognized organizations, or other unsafe exercises hailed given standard examinations in Endpoint Detection Response.
This procedure can be computerized, with abnormalities activating alarms to prompt activity or further examination instantly. However, numerous endpoint discovery and reaction devices also take into account manual or client-driven investigation of information in Endpoint Detection Response.
Endpoint detection & response is a developing field, yet endpoint IT capacities rapidly become essential to any venture security arrangement.
Endpoint detection and reaction is a sought-after capability for companies that demand Advanced threat protection. The advantages brought by consistent visibility into all activities of data make endpoint detection responses a good part of any security administration.
5 Main Functions of an EDR
- Endpoint Detection: The programs are designed to detect malicious activity on endpoints, such as computers, laptops, and other devices connected to the network. This includes identifying malicious files, suspicious network traffic, and other indicators of compromise.
- Threat Hunting: The solutions are designed to help security teams hunt for threats and investigate suspicious activities. This includes identifying malicious files, suspicious network traffic, and other indicators of compromise.
- Incident Response: The solutions help security teams respond quickly and effectively to security incidents. This includes identifying the incident's source, determining the incident's scope, and taking steps to contain and remediate the incident in Endpoint Detection Response.
- Forensics: The solutions are designed to help security teams collect and analyze evidence from endpoints to identify the root cause of an incident. This includes collecting system logs, memory dumps, and other artifacts from the endpoint.
- Compliance: EDR solutions are designed to help organizations meet regulatory and industry compliance requirements. This includes identifying and remediating vulnerabilities, implementing security policies, and monitoring for suspicious activity.
3 Key components of EDR security
- This is the core component of a security system. It is a software solution that continuously monitors and detects malicious activity on endpoints like computers, laptops, and mobile devices. It can detect suspicious behavior, malicious files, and unauthorized access in Endpoint Detection Response.
- Network Monitoring: This component of a security system monitors the network for suspicious activity. It can detect malicious traffic, unauthorized access, and malicious files.
- Incident Response: This component of a security system is responsible for responding to security incidents. It can contain the spread of malicious activity, investigate the incident, and take corrective action in Endpoint Detection Response.
Endpoint data collection agents
Data collection agents are programs that collect and store data from various sources in a central repository. They can collect data from websites, databases, sensors, and other sources.
They can also be used to analyze the data and generate reports. Data collection agents can monitor performance, detect anomalies, and provide insights into customer behavior.
Why Automated response?
Automated responses are needed to give customers quick and accurate answers to their questions. Automatic responses can reduce customer service costs, improve customer satisfaction, and provide customers with a more personalized experience.
Automated responses can also streamline customer service processes, allowing customer service representatives to focus on more complex tasks in Endpoint Detection Response.
Analysis and forensics
Computer forensics is a branch of digital forensic science about legal evidence found in computers and digital storage media. Computer forensics examines digital media forensically to identify, preserve, recover, analyze, and present facts and opinions about digital information. It includes the collection of evidence, analysis of the evidence, and reporting of the findings, used to investigate a wide range of computer-related crimes, including fraud, identity theft, hacking, and copyright infringement.
Computer forensics experts use various tools and techniques to analyze digital evidence, including disk imaging, data recovery, and network analysis. They also use specialized software to analyze the evidence and uncover hidden data. By analyzing digital evidence, computer forensics experts can help to identify the perpetrators of cybercrimes and provide evidence to support criminal prosecutions. Computer forensics can also uncover evidence of corporate wrongdoing, such as embezzlement or insider trading.
EDR improves threat intelligence
Yes, the Enhanced Cybersecurity Services (ECS) program, which is part of the Department of Homeland Security's (DHS) Enhanced Cybersecurity Services (ECS) program, is designed to improve threat intelligence sharing.
The program provides a secure platform for sharing cyber threat indicators and other cyber security information between the public and private sectors.
It also provides a secure platform for sharing cyber threat intelligence among the public and private sectors. It provides a secure platform for sharing cyber threat indicators and other cyber security information among the public and private sectors.
This program is designed to improve the ability of the public and private sectors to detect, analyze, and respond to cyber threats.
What is Endpoint Detection Response?: What Should I Look for in an EDR Solution?
- Comprehensive threat detection: Look for a solution that offers extensive threat detection capabilities, including the ability to detect and respond to malicious activity, suspicious network traffic, and malicious files.
- Automated response: The solution should be able to respond automatically to detected threats, such as blocking malicious IP addresses, quarantining malicious files, and alerting security personnel.
- Endpoint visibility: It should provide visibility into the activities of endpoints, such as user logins, file access, and application usage.
- Cloud-Based: It should be cloud-based to give users endpoint solutions offering constantly updated threat prevention and visibility.
- User behavior analytics: The solution should be able to detect suspicious user behavior, such as unusual login attempts or data exfiltration attempts.
- Incident response capabilities: It should provide incident response capabilities, such as investigating and remediating threats.
- Integration with other security solutions: This solution should be able to integrate with other security solutions, such as firewalls, antivirus, and SIEMs.
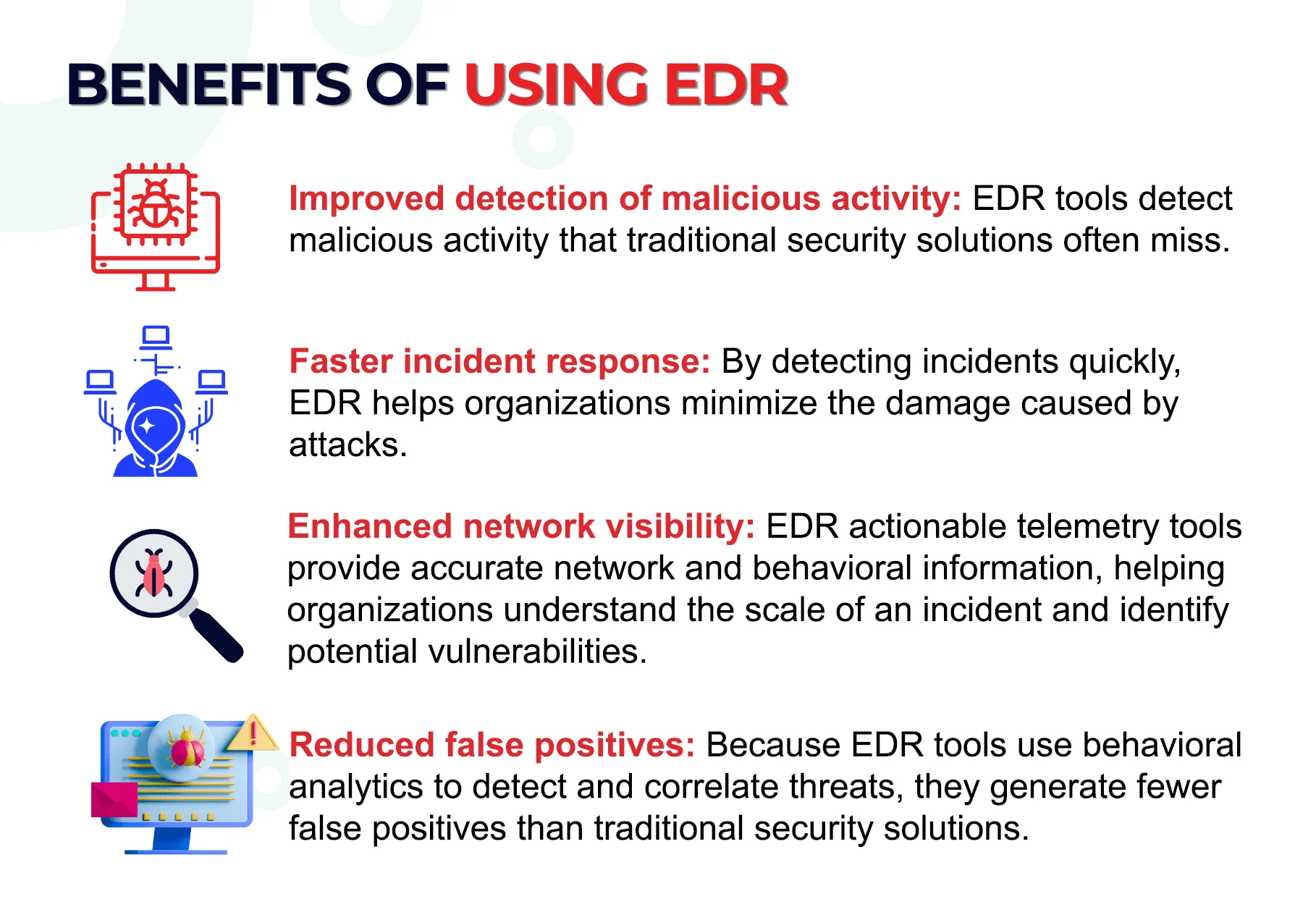
What is the difference between an EPP and EDR?
EPP (Endpoint Protection Platform) is a type of security software that protects an endpoint or device. It typically includes antivirus, firewall, and other security features.
EDR is a type of security software that provides additional detection and response capabilities beyond what EPP offers. It typically includes advanced analytics and threat intelligence capabilities to detect and respond to threats in real-time.

5 Reasons Your Business Needs Endpoint Detection Response?
While most organizations invest in Security Information and Event Management (SIEM) for their corporate networks' overall security visibility, EDR is just as important for their endpoint monitoring and protection. It provides the organization with a strong endpoint security solution that requires minimal effort and investment, strengthening its network security.
- Increased Visibility: It provides businesses greater visibility into their IT environment, allowing them to detect and respond to threats quickly and effectively.
- Improved Threat Detection: They are designed to detect malicious activity on endpoints, such as malicious files, suspicious network connections, and unauthorized user activities.
- Faster Response Times: It can help businesses respond to threats quickly and accurately, allowing them to reduce the amount of time it takes to detect and mitigate threats.
- Enhanced Security: The solution can help businesses strengthen their security posture by allowing them to detect and respond to threats quickly and accurately.
- Cost Savings: It can help businesses save money by reducing the time and resources needed to detect and respond to threats.
Key Endpoint Detection and Response Capabilities
Key EDR capabilities refer to the ability of an organization to detect, investigate, and respond to security incidents. This includes the ability to detect malicious activity, investigate the source of the activity, and respond appropriately.
This may include using automated tools to detect and respond to threats and manual processes for investigation and response. Additionally, organizations can monitor user activity and detect anomalous behavior, as well as respond to incidents quickly and effectively in Endpoint Detection Response.
What Are The Top EDR Security Solutions?
To assist your IT endpoint security teams in proactively mitigating cyber threats with an intelligent security response, EDR solutions provide the following features:
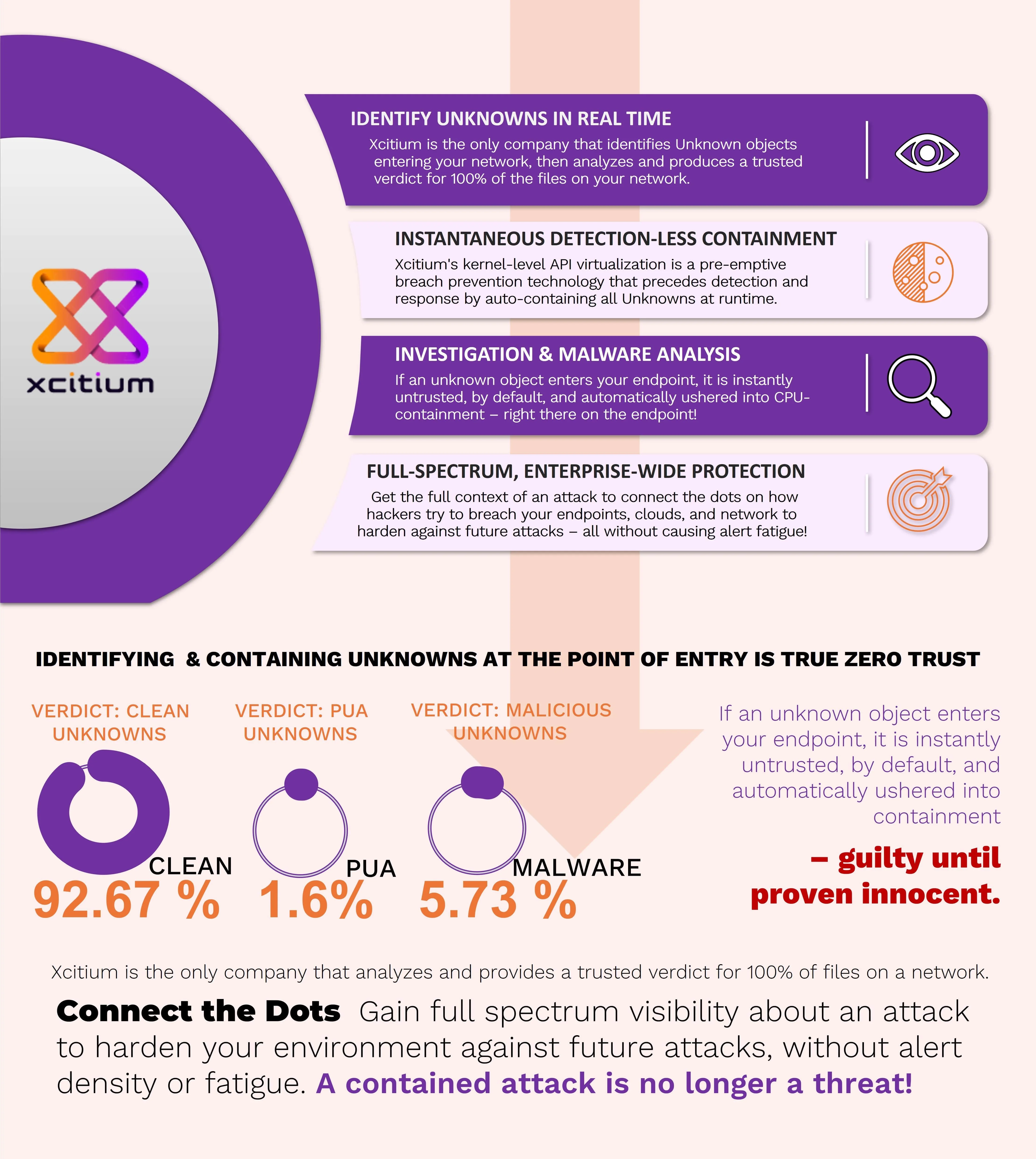
- Detection: The core capability of an Endpoint EDR detects advanced threats that bypass front-line defenses by analyzing files in real-time. Cyber threat intelligence using big data, machine learning, and advanced file analysis is crucial for effective detection.
- Containment: After giving an EDR solution, an Endpoint can contain malicious files to avoid infecting legitimate processes, applications, and users. Segmentation can help prevent lateral movement of threats in your network. Combined with EDR protection, this can contain malicious files before causing damage. For example, ransomware must be fully contained once it encrypts information.
- Investigation: When a malicious file is detected and contained, it's essential to investigate further to identify vulnerabilities and prevent future hazards. This involves sandboxing to observe the file's behavior without risking the network. The EDR endpoint security tool can assess the file and communicate findings with the cyber threat coping strategies for future preparedness. Neglecting investigation may result in the same hazards occurring again due to unknown vulnerabilities or outdated software.
- Elimination: The EDR detection solution can also eliminate threats by providing good visibility to determine files' origin and interaction with data and applications. It's not as simple as just deleting the file, as remediation of various network parts may be necessary. EDR solutions with retrospective abilities can provide actionable data to revert systems to their pre-infection state. Immediate action is crucial to respond to real-time incidents and effectively eliminate vulnerabilities.
Conclusion - Xcitium's EDR Security Solution
As cyberattacks continue to increase and become sophisticated, more and more people see the significance of adopting good endpoint detection response solutions. Afterall, EDR provides visibility into your endpoints so you can respond quickly to malicious actions.
For comprehensive endpoint protection solutions, choose Xcitium EDR. We can help you stay on top of your IT environment so your endpoint security teams can fend off threats that compromise your system. Contact us now!
How Xcitium Stops CyberThreats Hiding in Unknowns.