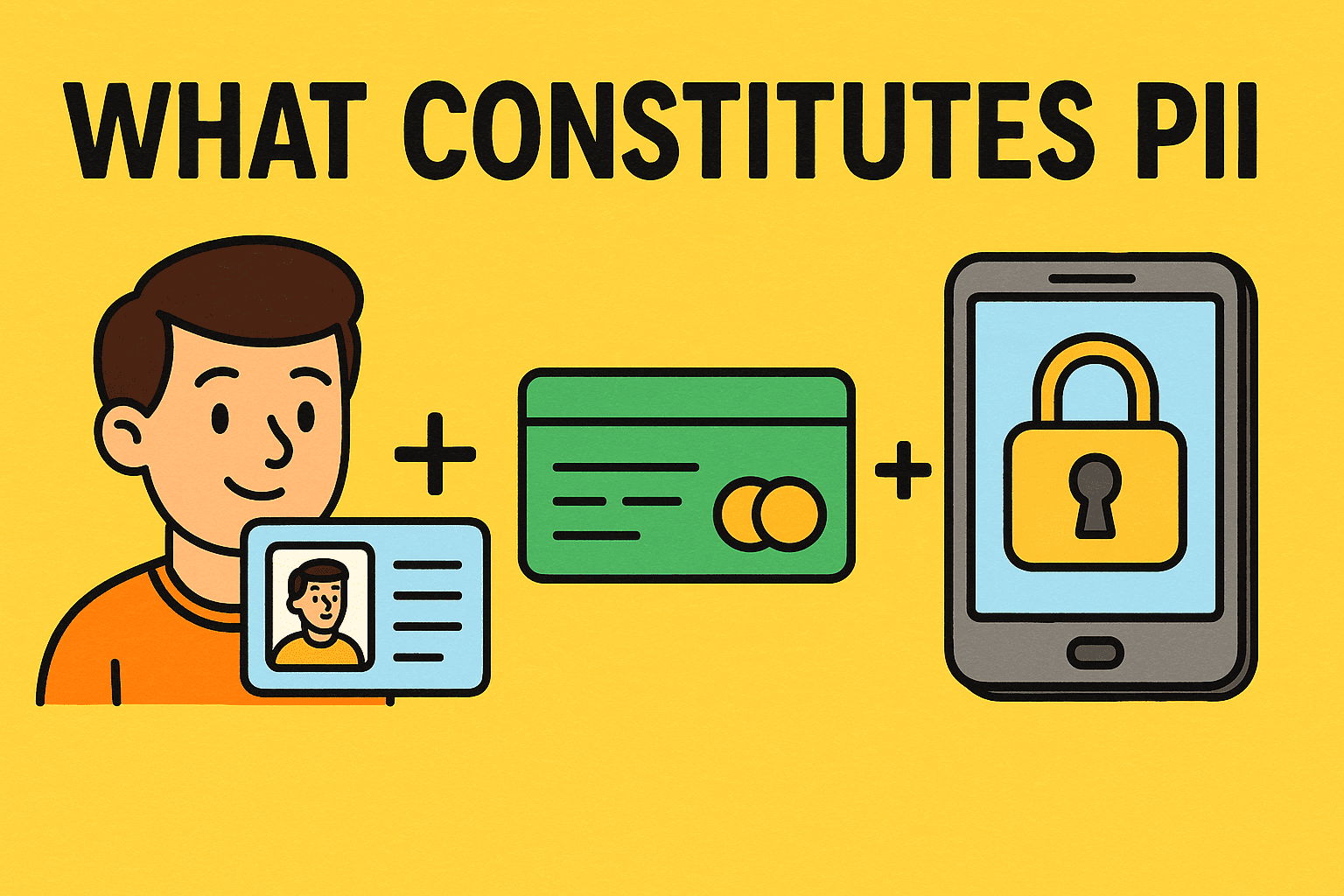
What Constitutes PII? A Complete Guide to Personal Identifiable Information
Updated on September 29, 2025, by Xcitium
Did you know that over 83% of organizations experienced a data breach involving PII (Personally Identifiable Information) in 2023? With cybercrime costs rising each year, understanding what constitutes PII is no longer just an IT concern—it’s a critical business requirement.
Introduction: Why Asking “What Constitutes PII?” Matters
PII, or Personally Identifiable Information, includes any data that can be used to identify an individual. From Social Security numbers to email addresses, protecting PII is essential for compliance, customer trust, and cybersecurity resilience.
In this guide, we’ll explore what constitutes PII, its categories, real-world examples, compliance obligations, and best practices to keep sensitive data safe.
1. What Constitutes PII?
PII (Personally Identifiable Information) refers to data that can directly or indirectly identify an individual.
Direct Identifiers (Always PII)
-
Full name
-
Social Security number
-
Driver’s license or passport number
-
Biometric identifiers (fingerprints, facial scans)
Indirect Identifiers (Potential PII)
-
Email address
-
Phone number
-
Date of birth
-
IP address or geolocation data
When combined, indirect identifiers can reveal a person’s identity—making them just as important to protect.
2. Categories of PII
PII is often divided into sensitive and non-sensitive categories:
-
Sensitive PII: Information that, if disclosed, could cause harm (e.g., financial accounts, health records, government-issued IDs).
-
Non-Sensitive PII: Publicly available information (e.g., ZIP codes, gender, or job titles). While less risky, it can still be dangerous when combined with other data.
👉 Example: A birthdate alone might not be risky, but when paired with a name and address, it becomes a powerful identifier for identity theft.
3. Examples of PII in Everyday Life
To better understand what constitutes PII, here are examples across industries:
-
Finance: Credit card numbers, bank account credentials, loan applications.
-
Healthcare: Patient records, insurance details, genetic data.
-
Education: Student ID numbers, grades, transcripts.
-
Business: Employee files, payroll data, email directories.
-
Technology: IP addresses, login credentials, biometric authentication data.
Every industry handles PII in some form, making protection a universal responsibility.
4. Why Protecting PII Matters
Failing to protect PII has severe consequences:
-
Data Breaches: Compromised PII fuels identity theft and fraud.
-
Financial Losses: Average cost of a PII-related breach is over $4.45 million.
-
Legal Penalties: Non-compliance with GDPR, HIPAA, or CCPA can result in heavy fines.
-
Reputation Damage: Customers lose trust when their personal data is mishandled.
For IT managers and executives, protecting PII is not just compliance—it’s business survival.
5. Laws and Regulations Around PII
Governments worldwide define and regulate what constitutes PII differently.
-
GDPR (EU): Defines PII broadly, including online identifiers like IP addresses.
-
HIPAA (US): Protects health-related PII such as medical records.
-
CCPA (California, US): Extends protections to consumer data, including browsing history.
-
PCI DSS: Protects payment card information.
👉 Organizations must understand which laws apply to their industry and geography.
6. Cybersecurity Risks to PII
Hackers constantly target PII for financial gain.
Common Threats:
-
Phishing Attacks: Trick employees into giving up credentials.
-
Ransomware: Encrypts sensitive PII until a ransom is paid.
-
Insider Threats: Employees misusing access to confidential data.
-
Data Leaks: Misconfigured cloud storage exposing PII.
-
Social Engineering: Exploiting publicly available information.
Cybersecurity leaders must anticipate these risks and enforce protective measures.
7. How Businesses Can Protect PII
Strong protection strategies go beyond encryption.
Best Practices:
-
✅ Data Minimization: Collect only the PII you need.
-
✅ Encryption: Secure data at rest and in transit.
-
✅ Access Control: Apply least-privilege principles.
-
✅ Multi-Factor Authentication (MFA): Add extra login protection.
-
✅ Employee Training: Teach staff to recognize phishing and handle data securely.
-
✅ Regular Audits: Identify vulnerabilities before attackers do.
For executives, investing in data protection strengthens both compliance and customer trust.
8. PII in the Cloud
With businesses shifting to cloud platforms, understanding what constitutes PII becomes more complex.
-
Cloud misconfigurations are a leading cause of PII leaks.
-
Shared responsibility models mean businesses—not just providers—are accountable.
-
Encryption and identity access management (IAM) are critical safeguards.
👉 CEOs should ensure their cloud partners align with compliance and security standards.
9. Real-World Data Breach Examples Involving PII
Learning from past incidents clarifies the risks:
-
Equifax (2017): 147 million people’s PII exposed due to unpatched systems.
-
Target (2013): Customer names, emails, and payment data stolen in a vendor-related breach.
-
Facebook (2019): Hundreds of millions of records, including phone numbers, exposed.
Each case underscores why organizations must prioritize PII security.
10. Future of PII Protection
Looking ahead, PII protection will evolve with technology:
-
Zero Trust Security: Ensuring no user or device is automatically trusted.
-
AI-Powered Threat Detection: Identifying unusual data access patterns.
-
Biometric Data Challenges: As biometrics become common, securing them is critical.
-
Stricter Regulations: More regions will adopt GDPR-like laws.
For business leaders, staying ahead means adopting proactive strategies now.
Quick PII Protection Checklist
✅ Identify what constitutes PII in your organization
✅ Encrypt sensitive and confidential data
✅ Enforce least privilege access controls
✅ Train employees on safe data handling
✅ Regularly audit and patch IT systems
✅ Stay compliant with GDPR, HIPAA, and other frameworks
FAQs on PII
1. What constitutes PII in simple terms?
PII is any data that can directly or indirectly identify a person, such as names, Social Security numbers, or email addresses.
2. Is an IP address considered PII?
Yes, under GDPR and certain laws, IP addresses and online identifiers qualify as PII.
3. What’s the difference between PII and sensitive PII?
Sensitive PII includes high-risk data like medical or financial records, while non-sensitive PII includes basic identifiers like ZIP codes.
4. How can companies reduce PII risks?
By minimizing data collection, encrypting information, enforcing access controls, and conducting regular audits.
5. Can PII be shared legally?
Yes, but only with proper consent, legal basis, or within compliance frameworks.
Final Thoughts
Asking “what constitutes PII?” is more than a compliance question—it’s about protecting people, businesses, and reputations in a digital-first world.
By clearly identifying what counts as PII, enforcing strict data security policies, and staying ahead of evolving threats, organizations can significantly reduce their risks.
🚀 Ready to safeguard your business’s sensitive data?
Request a demo of Xcitium’s advanced cybersecurity solutions today and gain visibility, compliance, and peace of mind.