MDR for Defender: The Complete Conversational Guide to Strengthening Your Security in 2026
Updated on November 21, 2025, by Xcitium
Have you ever wondered why cyberattacks keep getting more advanced even though businesses invest in antivirus and endpoint security? If you’ve used Microsoft Defender before, you probably know it offers strong protection — but even Defender has its limits. That’s where MDR for Defender comes in.
MDR stands for Managed Detection and Response, and when you combine MDR with Microsoft Defender, you get a powerful security system that gives you real-time monitoring, threat hunting, faster response times, and expert guidance 24/7.
In this friendly, conversational guide, you’ll learn exactly what MDR for Defender is, why businesses rely on it, how it works, and how you can use it to prevent breaches, reduce risk, and stay ahead of cyber threats.
Let’s dive in.
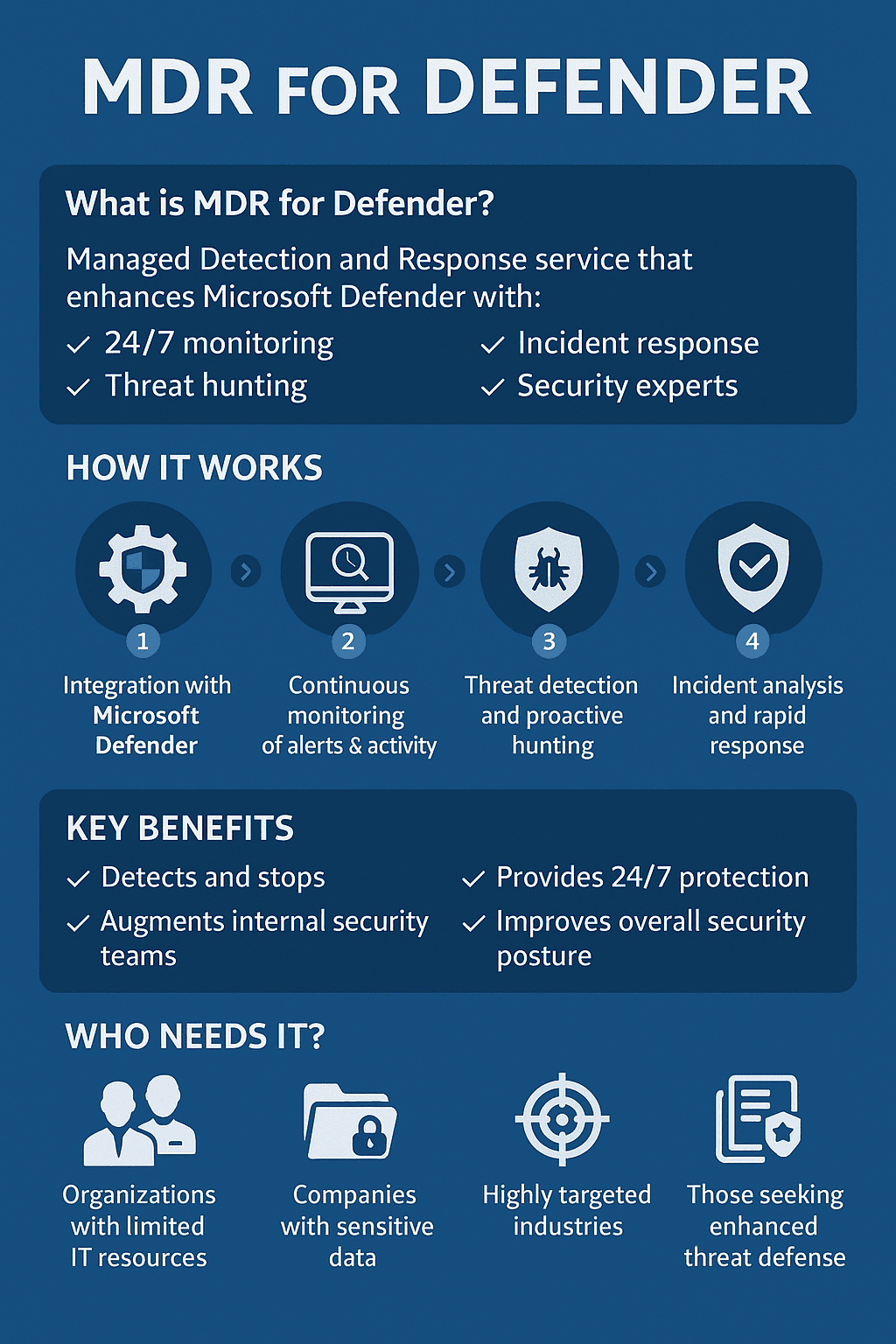
⭐ What Is MDR for Defender? (Simple Definition)
MDR for Defender is a managed security service that enhances Microsoft Defender by adding:
-
24/7 monitoring
-
Expert threat hunting
-
Incident response support
-
Faster detection of attacks
-
Real-time threat investigation
-
Human-led analysis and intelligence
While Microsoft Defender provides strong automated endpoint protection, MDR adds human expertise, advanced analytics, and continuous monitoring to ensure nothing slips through the cracks.
In simple terms:
👉 Microsoft Defender protects your devices. MDR for Defender protects your entire business — with real humans watching for threats 24/7.
⭐ Why MDR Is Needed (Even If You Already Use Microsoft Defender)
Microsoft Defender is excellent, but businesses still struggle to keep up with:
-
Alert fatigue
-
False positives
-
Threat complexity
-
Limited internal staff
-
Ransomware
-
Zero-day attacks
-
Multi-stage intrusions
-
Cloud threats
-
Identity-based attacks
Most companies don’t have a full security team working around the clock. Attackers do.
That’s why MDR for Defender is essential — it bridges the gap between technology and human expertise.
🔍 What MDR for Defender Actually Does
Here’s what MDR providers do behind the scenes:
1. 24/7 Monitoring and Response
Security analysts watch your endpoints, cloud apps, and Defender alerts continuously — even when your internal team is offline.
2. Threat Hunting
Humans actively look for suspicious behavior:
-
Lateral movement
-
Privilege escalation
-
Unusual login patterns
-
Beaconing
-
Ransomware activity
AI alerts + human validation = fewer missed threats.
3. Faster Incident Response
When something happens, MDR analysts jump into action:
-
Investigating the threat
-
Stopping the attack
-
Isolating compromised endpoints
-
Guiding your IT team
-
Containing the breach
4. Advanced Analytics
MDR platforms integrate:
-
Behavioral analysis
-
Endpoint telemetry
-
Attack chain mapping
-
MITRE ATT&CK coverage
Providing a deeper look than Defender alone.
5. Proactive Recommendations
You also receive:
-
Security hardening guidance
-
Compliance recommendations
-
Patch priorities
-
Risk scoring
This helps your business stay ahead of attackers.
Benefits of MDR for Defender
If you’re wondering what makes MDR worth it, here are the biggest advantages:
✔ Stops advanced threats early
Human analysts catch attacks that automated systems miss.
✔ Reduces breach costs
Faster response = less damage.
✔ Saves IT teams from alert overload
Instead of thousands of Defender alerts, you get actionable summaries.
✔ Enhances your entire security stack
Defender becomes stronger with human intelligence layered on top.
✔ Boosts compliance
Supports SOC 2, HIPAA, GDPR, PCI-DSS, and ISO.
✔ 24/7 protection
Cyberattacks happen at night and during holidays. MDR covers you.
✔ Reduces risk for CEOs and CISOs
Executives gain confidence that threats are being handled proactively.
How MDR for Defender Works (Step-by-Step)
Let’s break down the entire lifecycle.
Step 1: Integration with Microsoft Defender
MDR connects to:
-
Microsoft Defender for Endpoint
-
Microsoft Defender for Identity
-
Defender for Cloud Apps
-
Defender for Office 365
Step 2: Continuous Monitoring
All activity, alerts, and telemetry flow into one dashboard.
Security analysts monitor:
-
Endpoint behavior
-
Cloud activity
-
Network anomalies
-
Identity threats
-
Login attempts
-
Email attacks
Step 3: Threat Detection
Using:
-
AI
-
Machine learning
-
Behavior analysis
-
MITRE ATT&CK mapping
Suspicious behaviors trigger deep investigation.
Step 4: Threat Hunting
Experts proactively search for:
-
Dormant malware
-
Hidden persistence mechanisms
-
Lateral movement
-
Credential theft
-
Unusual patterns
Step 5: Response Guidance (or Full Containment)
Depending on your MDR provider:
They may:
✔ Notify you instantly
✔ Isolate infected devices
✔ Kill malicious processes
✔ Block attacker IPs
✔ Remove malware
✔ Remediate misconfigurations
Step 6: Post-Incident Reporting
You receive:
-
Incident report
-
Root cause analysis
-
Timeline of attack
-
Recommendations
-
Prevention steps
⭐ MDR for Defender vs Microsoft Defender: What’s the Difference?
Here’s a quick breakdown:
| Feature | Microsoft Defender | MDR for Defender |
|---|---|---|
| Threat detection | Automated | Automated + human-led |
| Monitoring | Business hours | 24/7/365 |
| Response | Manual | Guided or fully managed |
| Threat hunting | Limited | Proactive & continuous |
| Expertise | In-house | Global SOC teams |
| Alert fatigue | High | Low |
| Cost | Free/Included | Subscription |
MDR transforms Defender from a powerful tool into a fully managed security operation.
⭐ Who Needs MDR for Defender?
You should consider MDR if:
-
Your IT team is small
-
You don’t have a 24/7 SOC
-
You deal with sensitive data
-
Ransomware is a concern
-
You have remote workers
-
You use Microsoft 365 heavily
-
You must meet compliance standards
-
You can’t afford downtime
Industries that benefit most:
-
Healthcare
-
Finance
-
SaaS companies
-
Legal
-
Government
-
Manufacturing
-
Managed service providers
🔐 Why MDR for Defender Is Critical for Zero-Trust Security
Zero-trust requires:
-
Continuous monitoring
-
Behavioral analysis
-
Identity protection
-
Endpoint control
-
Least-privilege enforcement
-
Real-time actions
Defender alone can’t maintain zero-trust — MDR makes it possible.
🧩 How MDR Helps Against Ransomware
MDR teams:
✔ Detect early signs like:
-
Shadow copy deletion
-
Encryption patterns
-
Suspicious PowerShell commands
-
Privilege escalation
✔ Stop attacks before encryption
✔ Isolate infected endpoints
✔ Block attacker connections
✔ Guide teams through recovery
This prevents multi-million-dollar damages.
⭐ Choosing the Best MDR for Defender Provider
Look for:
-
24/7 SOC support
-
Real human analysts
-
Quick response times
-
Defender expertise
-
MITRE ATT&CK coverage
-
Cloud + endpoint integration
-
Affordable pricing
-
Automated containment
-
Clear reporting
Platforms like Xcitium MDR combine powerful containment with Defender’s detection signals for maximum protection.
🎯 Conclusion: MDR for Defender Is Essential in 2026
If you’ve been wondering why so many organizations are upgrading from Microsoft Defender alone to MDR for Defender, here’s the bottom line:
👉 Defender protects devices. MDR protects your business.
With threat hunting, human analysts, rapid response, and 24/7 visibility, MDR dramatically reduces your risk of breaches.
In a world where cyberattacks are constant, MDR isn’t a luxury — it’s a necessity.
🔐 Enhance Microsoft Defender with Xcitium MDR
Boost your endpoint and identity protection with proactive threat hunting and real-time containment.
👉 Request a demo: https://www.xcitium.com/request-demo/
❓ FAQs About MDR for Defender
1. Is MDR for Defender the same as Microsoft Defender?
No. MDR adds human-led monitoring and response on top of Defender.
2. Does MDR work with Microsoft 365?
Absolutely — it integrates seamlessly with M365 and Azure AD.
3. Is MDR only for large enterprises?
No. Small and midsize businesses benefit the most.
4. Can MDR stop ransomware?
Yes — MDR responds early, isolates endpoints, and prevents encryption.
5. How fast does MDR respond to threats?
Most MDR providers respond within minutes, not hours.


 (151 votes, average: 4.67 out of 5, rated)
(151 votes, average: 4.67 out of 5, rated)