What Is UDP Protocol? A Guide for IT & Cybersecurity Pros
Updated on July 21, 2025, by Xcitium
Have you ever streamed a video, played an online game, or made a VoIP call and wondered how it all stays so smooth? The secret often lies in the UDP protocol—a lightweight and fast method of sending data across networks. But what is UDP protocol, and why does it matter in cybersecurity and IT?
This guide breaks down UDP from basics to real-world applications, helping professionals across industries understand its role in networking.
What Is UDP Protocol?
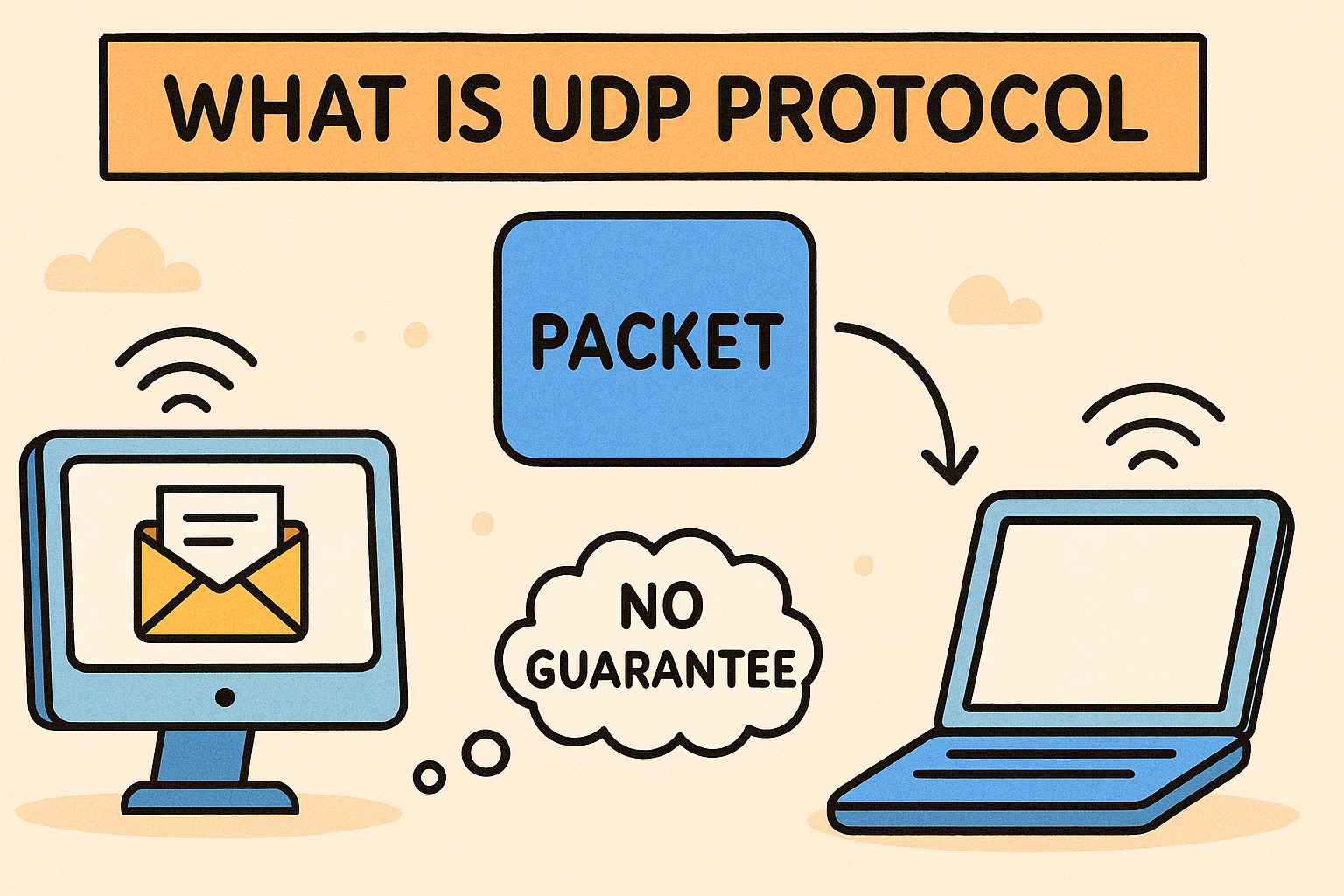
UDP stands for User Datagram Protocol. It is a connectionless communication protocol used in networks to send messages—called datagrams—without establishing a prior connection. Unlike TCP (Transmission Control Protocol), UDP doesn’t guarantee message delivery, ordering, or error checking.
UDP is part of the transport layer in the OSI and TCP/IP models, making it crucial for applications that prioritize speed over reliability.
What Is UDP Protocol Used For?
UDP is ideal in scenarios where speed is critical, and occasional data loss is acceptable:
- Streaming media (YouTube, Netflix)
- Online gaming (low latency communication)
- Voice over IP (VoIP) (Skype, Zoom)
- DNS lookups
- Broadcast and multicast transmissions
Because UDP doesn’t waste time ensuring all data is received, it’s perfect for real-time communication.
UDP Protocol in Networking: How It Works
Here’s how UDP operates in a network:
- No Handshake – No setup process before sending data.
- Datagram-Based – Sends independent packets without tracking.
- No Delivery Assurance – Does not confirm receipt or order of data.
- Lightweight Header – Only 8 bytes vs TCP’s 20 bytes.
Its simplicity makes UDP fast but less reliable than TCP.
UDP vs TCP: Key Differences
| Feature | UDP Protocol | TCP Protocol |
| Connection | Connectionless | Connection-oriented |
| Reliability | No guarantee | Ensures delivery and order |
| Speed | Faster | Slower due to handshakes and checks |
| Use Cases | Streaming, DNS, VoIP | File transfer, emails, web browsing |
| Header Size | 8 bytes | 20 bytes |
| Overhead | Low | Higher |
So when comparing UDP vs TCP, choose UDP for speed and TCP for reliability.
UDP Protocol Example: Real-World Use
Let’s take online gaming as an example. A delay in game communication—even milliseconds—can impact gameplay. UDP sends rapid updates without waiting for acknowledgments, ensuring real-time responsiveness. This is more important than perfect data accuracy in such cases.
Understanding UDP Port Number and Protocol Number
- UDP Port Number: Identifies specific processes or services. Common ports include:
- 53 – DNS
- 67/68 – DHCP
- 123 – NTP (Network Time Protocol)
- UDP Protocol Number: In IP headers, UDP is assigned protocol number 17.
This enables routers and firewalls to recognize and handle UDP traffic appropriately.
Where Does UDP Fit in the OSI and TCP Models?
UDP resides in the transport layer (Layer 4) and relies on the Internet Protocol (IP) for addressing and routing. Applications using UDP must handle any required data checking or sequencing themselves.
Benefits of UDP Protocol
- 🌐 Speed and Low Latency – Ideal for real-time apps.
- 🔄 Efficient Bandwidth Usage – Minimal overhead.
- 🚀 Fast Transmission – Skips handshake and verification.
- 💡 Multicast Support – Perfect for broadcasting data to many users.
Drawbacks of UDP Protocol
- ❌ No delivery assurance
- ❌ No retransmission of lost packets
- ❌ Susceptible to spoofing or flooding in cyberattacks
That’s why security-conscious networks often combine UDP with encryption, firewalls, and anomaly detection systems.
UDP in Cybersecurity
Cyber attackers often exploit UDP’s connectionless nature for:
- UDP flood DDoS attacks
- Spoofed DNS requests
- Port scanning
To mitigate these risks:
- Implement deep packet inspection (DPI)
- Use rate limiting and UDP filtering rules
- Monitor unusual traffic spikes from UDP-heavy services
Final Thoughts
So, what is UDP protocol? It’s a fast, lightweight method of data transmission, ideal for real-time applications. While it trades reliability for speed, it remains a vital tool in every IT and cybersecurity professional’s arsenal.
To fully leverage or secure UDP in your enterprise environment, understanding its role, limitations, and protections is essential.
✅ Ready to secure your network?
Partner with Xcitium for real-time visibility, threat protection, and expert support.
🔎 Frequently Asked Questions (FAQ)
Q1: What is UDP protocol used for?
A: UDP is used for real-time communication like video streaming, VoIP, DNS, and online gaming where speed matters more than accuracy.
Q2: How does UDP differ from TCP?
A: Unlike TCP, UDP doesn’t guarantee delivery, order, or data integrity. It’s faster and better for time-sensitive applications.
Q3: What is an example of UDP protocol?
A: Streaming services like Netflix and video calls via Zoom often use UDP to reduce latency and buffering.
Q4: What is the UDP protocol number?
A: UDP is assigned protocol number 17 in the IP header.
Q5: Is UDP secure?
A: UDP lacks built-in security, but it can be secured with encryption (like DTLS), firewalls, and traffic monitoring tools.