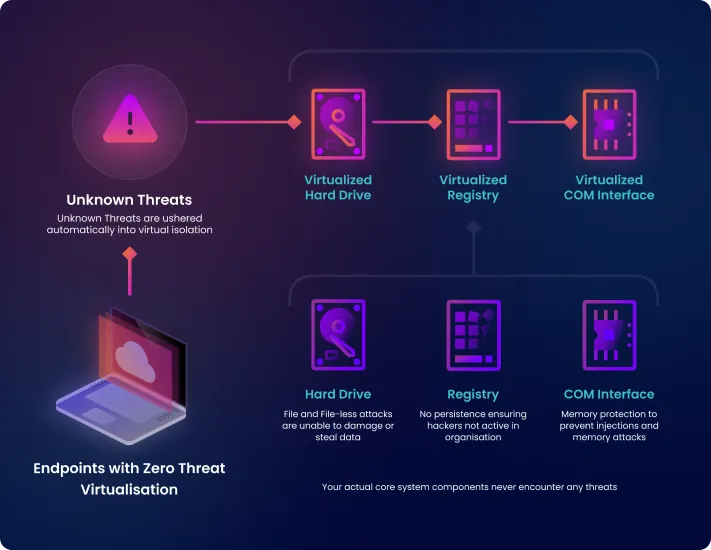
How Our Real-Time Virtualization Works
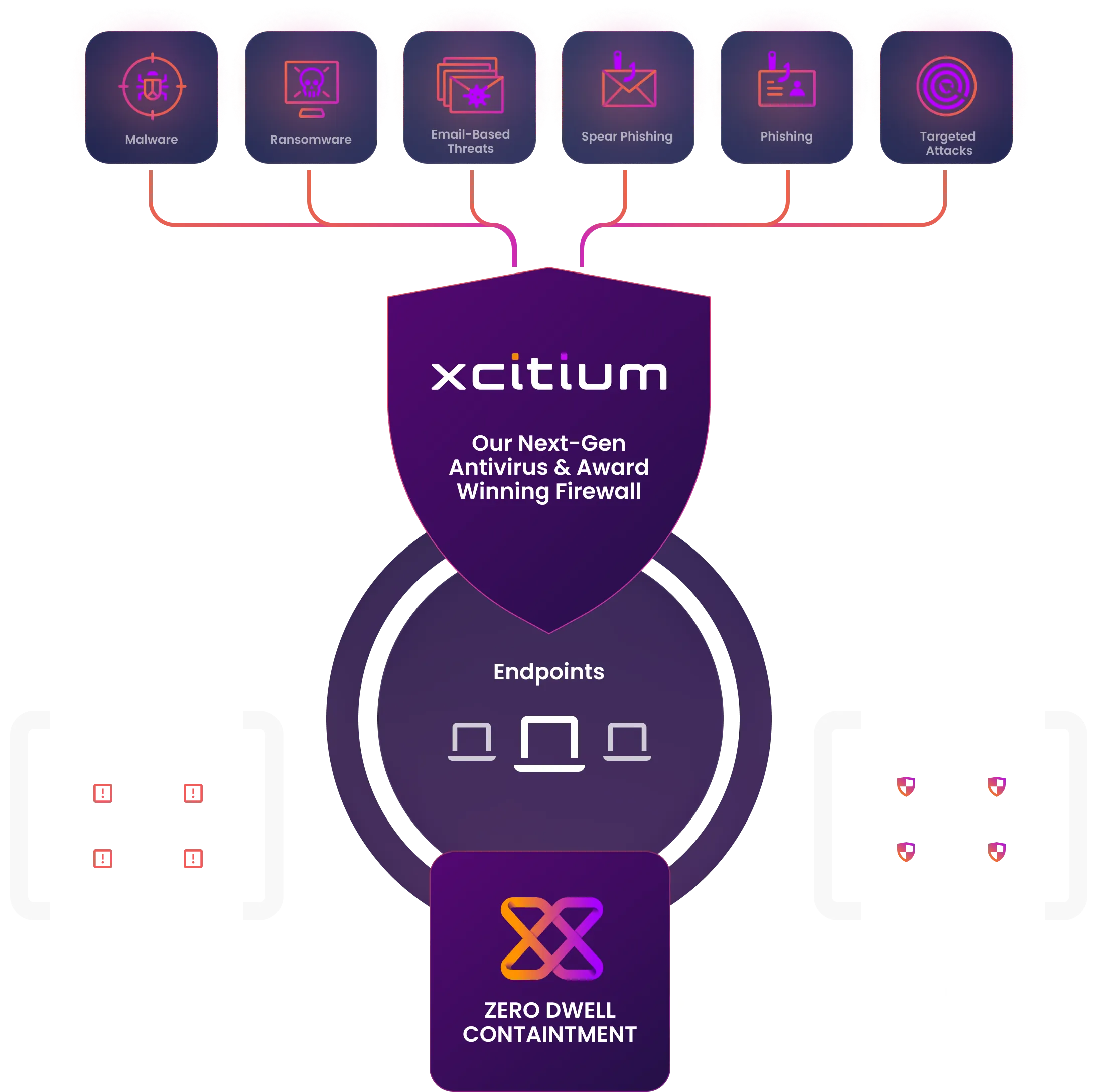
Xcitium’s patented ZeroDwell technology prevents unknown executables from damaging endpoints at runtime. Unknowns are allowed to run, avoiding any disruptions to your business, but in virtualized instances where they can be verdicted “good” or “bad”, thus preventing any damage to your endpoints.
Detection-based security does not recognize (and thus protect against) unknowns, including new malware. Unknowns are only discovered and addressed by legacy detection-based endpoint security providers once it has done damage to their clients. Xcitium’s Zero Trust Architecture (ZTA) by contrast, automatically detects all unknown executables and allows them to launch only to a virtualized container where they can do no harm.
Zero Dwell containment is quickly deployed with cloud-native updates via the client so that it won’t heavily impact endpoint performance. End users enjoy seamless productivity, with the ability to run any unknown file virtually, even while the file is under analysis.
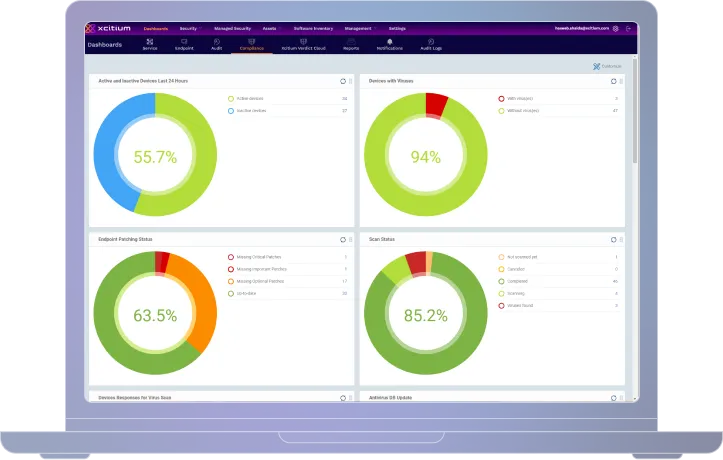
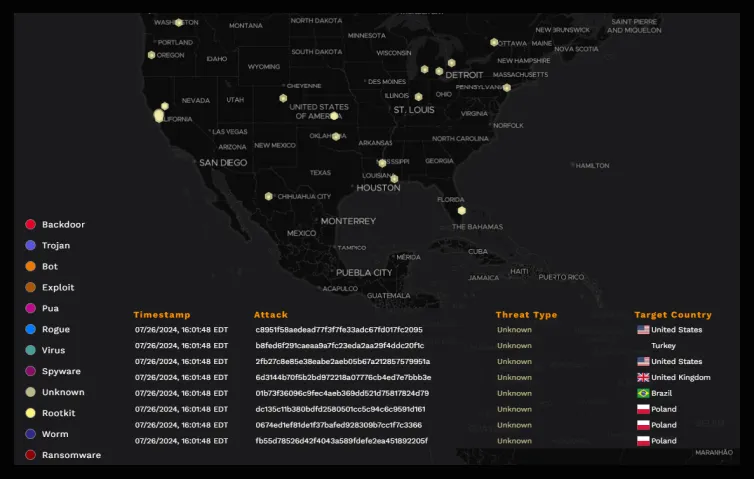
Through the Verdict Cloud engine, results are published globally in real-time for all Xcitium customers. Using a combination of multiple AI environments and human security specialists, you will never be exposed to the damage of cyber threats through true zero trust architecture.
Receive highly refined internal and external threat intelligence feeds to alert or block on indicators of compromise. Incorporate your companies own internal intelligence into Xcitium’s enterprise platform for added coverage. Complete Verdict Cloud integration for checks on process execution via MD5 hash submission.
Xcitium exists to ensure that people can embrace technology fully, without the shadow of insecurity hanging over them. We’re here to give users the freedom to explore, create, and connect without fear. Whether it’s preventing unknown files from compromising systems or offering innovative approaches to endpoint protection solution, Xcitium’s technology is designed to foster confidence. We believe that by keeping the digital ecosystem secure, we’re directly contributing to human evolution—by enabling people to take full advantage of the tools that define our era.

When you visit any website, it may store or retrieve information on your browser, mostly in the form of cookies. This information might be about you, your preferences or your device and is mostly used to make the site work as you expect it to. The information does not usually directly identify you, but it can give you a more personalized web experience. Because we respect your right to privacy, you can choose not to allow some types of cookies. Click on the different category headings to find out more and change our default settings. However, blocking some types of cookies may impact your experience of the site and the services we are able to offer.