TToday, cyber security is saturated with different solutions. And when it comes to enterprise endpoint security, you find plenty of options. You can only decide what option is suitable for your organization if you opt for EDR Demo.
According to AlliedMarket Research, the Endpoint detection, and response market size will reach $18.3 billion by 2031.
Some top EDR vendors include SentinelOne, Microsoft Defender, Xcitium EDR, and many others. Every vendor brings some unique features that set them apart from others. Many new companies are emerging in the market.
You'll find similarities and differences when you check the individual datasheet of the Endpoint detection solution. It becomes a challenge to pick one among all. You can opt for an EDR demo to make the right choice.
What Happens During EDR Demo?
The good news is that you can get a cost-free demo of the Endpoint detection and response tool. You can contact a company by sharing your company name, employee number, and overall business scale. Once you request a demo, the company will send an alert, and he will offer you a demo, so you can better understand how this tool helps you protect your endpoints.
Here is what they do in the demo:
Contextualize and Identify Threats in Real-Time
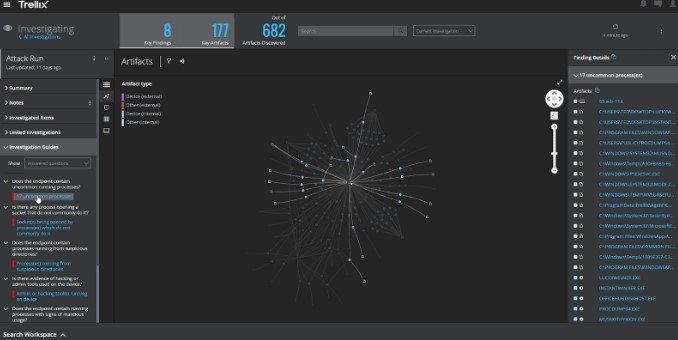
The purpose of an EDR agent is to help your team identify threats. Before you start using a system, you must know how it works. Thereby, a system engineer comes to offer a complete demonstration. This expert will show you how multiple Artificial intelligence agents work together to spot threats lingering on your endpoints.
You can see and visualize threats in real time. And there are other things you would get in an EDR demonstration. Another thing this professional will explain is threat context. For example, when you opt for the Xcitium EDR demo, a professional will share a tree structure with you.
You can visualize how an attack started, where it spread, and how it stopped and contained. In other words, you can visualize every phase of an attack and potential threat.
Threat Response & Rollback
If you watch the SentinelOne ActiveEDR Demo video, it provides a complete explanation of how this software will respond to a threat.
Let's suppose a ransomware attack happens on your business.
Ransomware infects essential files and data. Once this attack is over, rollback features rescue your team. The data of infected files will be restored, and you won't lose it.
Regarding response factors, every EDR tool has an automatic response system. It contains threats while isolating a compromised Endpoint temporarily. Your team gets time to investigate an incident and respond to it.
Some EDRs bring an incident response playbook so that your team gets guidance and suggestion on what kind of response they should take based on a threat vector.
Compatibility and Customization
Although there is a magnitude of Endpoint detection and response solutions available in the market, only some solutions are designed to meet your organization's specific needs. During an EDR demo, your team should find a solution compatible with existing security tools.
Some vendors offer customized solutions, and they are indeed the right choice. Xcitium allows its users to customize the policy per company size and requirements. It will enable your team to respond to threats as they want and define everything per enterprise specifications.
Malicious Behavior Prediction
No matter what Endpoint security solution you get, it works proactively. And your company needs to understand that. Some enterprises stick with legacy software and antivirus. They believe that it's good enough security they have in the network.
They need to know that endpoints are the most vulnerable; they are the most favorite entry points for cybercriminals.
A system engineer offers a detailed demonstration of how an endpoint detection tool keeps track of all behavior and user activities on endpoints. The expert further explains how your team can predict malicious behavior across all threat vectors.
Once you predict an attack, you prep with risk management and remediation. This proactive approach is far better than a reactive solution like an antivirus. You hunt for threats actively, and it's how you can improve your security posture by identifying potential threats.
Seamlessly Adapt Defenses
When getting an EDR Demo, investing money in a solution that adapts your endpoint and server defense is better. It should create a strong security shield against the latest malware, ransomware, APTs, and other attacks. It must offer protection against a broad spectrum of threats on your organization's endpoint.
Wrap up
Booking an EDR demo aims to understand how this software detects, responds, and prevents existing, latest, and advanced threats. You can either get a live demo or watch a video. It will help you better understand features and functionality.
Get a demonstration of multiple EDR solutions, compare them, and pick one that fits your organization's security needs and budget.
