Best Security For Computer Endpoint Devices – Top 12 Tips
Computer security issues are not only a hassle for students or professional corporates, as...

Computer security issues are not only a hassle for students or professional corporates, as...
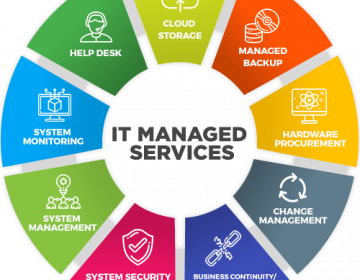
Small business startups often face the situations of not having expert guidance and lack of...

Cybersecurity ventures are the building blocks behind the powerful encryption of data of companies....

Why is a business-boosting element essential for companies’ digital presence getting exploited...

IT consulting is the element of success for many business companies. Evolving technologies have...

As cybercrimes are surging and damaging global businesses’ reputations by stealing data, every...

The utilization of mobile endpoint devices is not just for personal use anymore. Global...

Entrepreneurship is at its peak in today’s marketplace of digital businesses. Hence, there is...

Many have their own perceptions, theories, and references about the criminal cyber acts of...