What Is a Hash Function? A Complete Guide for Cybersecurity
Updated on November 7, 2025, by Xcitium
In cybersecurity and data management, the term hash function often appears in discussions about encryption, digital signatures, and data integrity. But what does a hash function really do, and why is it so crucial for modern information systems?
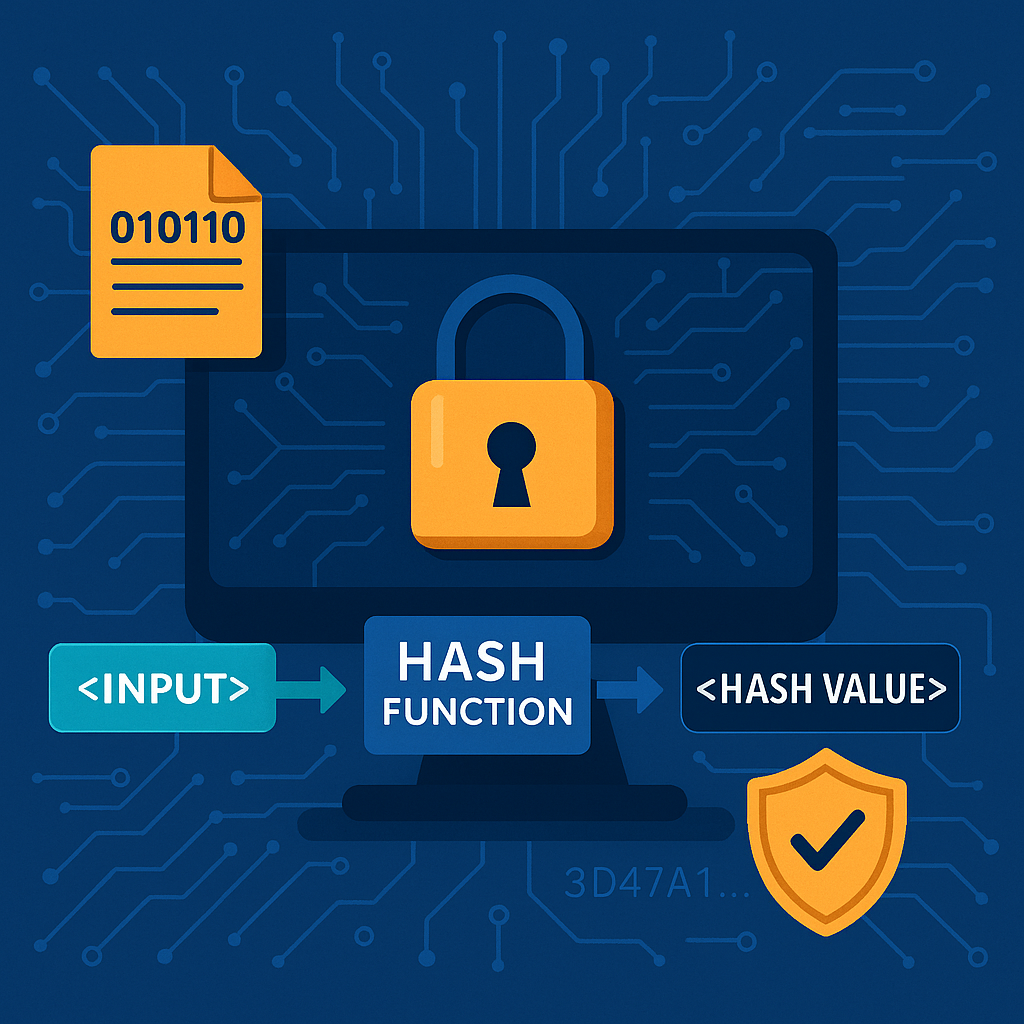
A hash function is a mathematical algorithm that converts data of any size into a fixed-size string of characters, often represented as a series of numbers and letters. This process is vital for securing information in everything from passwords and file verification to blockchain technology and digital certificates.
Understanding how hash functions work—and how they protect data—is essential for IT professionals, cybersecurity experts, and business leaders alike. Let’s explore how these cryptographic tools keep our digital world safe.
What Is a Hash Function?
A hash function takes an input (often called a “message”) and returns a unique, fixed-length string known as a hash value or digest. Regardless of the input size, the output remains the same length.
For instance:
Even a tiny change in the input—say, typing “xcitium” in lowercase—will produce a completely different hash. This sensitivity to input changes is known as the avalanche effect, and it’s what makes hash functions so powerful for security applications.
How Hash Functions Work
Hash functions are designed to follow key mathematical principles that ensure speed, consistency, and irreversibility. They use complex algorithms that perform multiple rounds of bitwise operations, shifts, and modular additions to generate the hash output.
The Core Properties of Hash Functions
A good cryptographic hash function must meet these essential criteria:
-
Deterministic Output – The same input always produces the same hash output.
-
Irreversibility – It should be nearly impossible to reverse-engineer the original input from the hash.
-
Collision Resistance – Two different inputs should never produce the same hash value.
-
Avalanche Effect – A small change in input drastically changes the output hash.
-
Efficiency – The function must compute quickly, even for large datasets.
These properties make hash functions invaluable for cybersecurity operations, especially where data validation and authentication are critical.
Common Types of Hash Functions
Several cryptographic hash functions are used in cybersecurity today. Each offers different levels of complexity and security strength.
1. MD5 (Message Digest 5)
Once widely used, MD5 produces a 128-bit hash value. However, due to discovered vulnerabilities and hash collisions, MD5 is now considered insecure for modern encryption needs.
2. SHA Family (Secure Hash Algorithm)
Developed by the NSA, SHA algorithms are among the most trusted and widely used.
-
SHA-1: 160-bit output; now deprecated for most uses.
-
SHA-2: Available in SHA-224, SHA-256, SHA-384, and SHA-512; currently the standard for most security systems.
-
SHA-3: The newest iteration, built for post-quantum safety and enhanced resistance to cryptanalysis.
3. BLAKE2 and BLAKE3
These are modern hash algorithms optimized for both speed and security, often outperforming SHA in performance benchmarks.
4. Whirlpool
A robust 512-bit hash function, often used in encryption systems and file integrity verification.
Applications of Hash Functions in Cybersecurity
Hash functions play a vital role across multiple cybersecurity processes and tools. Here’s how they protect systems and users daily.
1. Password Storage and Authentication
When you create a password, it’s not stored as plain text. Instead, it’s hashed using a cryptographic function like SHA-256.
When you log in, the system hashes your entered password and compares it to the stored hash—if they match, you’re authenticated.
Many systems also use salting (adding random data to the password before hashing) to prevent attackers from using precomputed lookup tables (rainbow tables) to guess passwords.
2. Digital Signatures and Certificates
Hash functions enable digital signatures, which verify that data or documents haven’t been altered in transit.
When you visit a secure website (HTTPS), your browser checks the hash of its SSL certificate to ensure its authenticity.
3. Data Integrity Verification
Organizations use hashes to confirm that data hasn’t been tampered with during transmission or storage.
For example, software downloads often include a checksum—a hash value that users can verify to ensure the file is legitimate.
4. Blockchain and Cryptocurrency
Every block in a blockchain includes the hash of the previous block, creating an immutable chain.
This makes blockchain technology tamper-proof, as altering any single block changes all subsequent hashes.
5. Malware Detection and Threat Analysis
Cybersecurity tools use hash-based techniques to detect malicious files.
By comparing file hashes against known malware databases, systems can quickly identify and block threats.
How Hash Functions Differ from Encryption
While both hash functions and encryption are key parts of cybersecurity, they serve very different purposes:
| Feature | Hash Function | Encryption |
|---|---|---|
| Purpose | Data integrity & verification | Data confidentiality |
| Reversibility | One-way (irreversible) | Two-way (can be decrypted) |
| Output Size | Fixed length | Variable length |
| Common Algorithms | SHA-256, MD5, BLAKE2 | AES, RSA, DES |
Hashing ensures data integrity, while encryption ensures data privacy—both are vital to a strong security framework.
Why Hash Functions Are Critical for Business Security
For IT leaders and CISOs, implementing hash functions correctly is essential to safeguarding digital assets and maintaining trust.
They underpin secure login systems, protect intellectual property, and enable compliance with data protection laws like GDPR and HIPAA.
Key benefits include:
-
✅ Protecting sensitive credentials from exposure.
-
✅ Ensuring software authenticity during updates or distribution.
-
✅ Verifying system integrity after incidents or backups.
-
✅ Supporting secure communication via SSL/TLS protocols.
Neglecting proper hashing standards can leave organizations open to data breaches, credential theft, and system manipulation.
Best Practices for Using Hash Functions in Security
To make the most of hash functions in cybersecurity, professionals should follow these guidelines:
-
Avoid deprecated algorithms like MD5 and SHA-1.
-
Use salted hashes to secure stored passwords.
-
Combine hashing with encryption for layered security.
-
Regularly update algorithms as standards evolve.
-
Validate hash functions through FIPS-certified libraries or trusted providers.
Implementing these practices ensures stronger protection against evolving threats.
Real-World Example: Hashing in Action
Consider a company distributing security software updates.
To prevent tampering, they publish the hash of the update file (for example, SHA-256 checksum).
When users download the file, they can verify it by generating their own hash—if it matches, the file is authentic.
This simple yet effective method prevents man-in-the-middle attacks and malware injection, ensuring that users receive safe, verified software.
Future of Hash Functions: Post-Quantum Security
As quantum computing evolves, traditional cryptographic systems face potential vulnerabilities.
Quantum algorithms like Shor’s could break existing encryption and hashing methods.
To counter this, researchers are developing post-quantum cryptographic hash functions that can resist quantum attacks.
Future systems will likely rely on algorithms that combine speed, scalability, and quantum resistance—ensuring long-term digital security.
Conclusion
A hash function is one of the cornerstones of cybersecurity—quietly protecting billions of transactions, communications, and logins every day.
From password management to blockchain verification, hashing ensures that data remains authentic, untampered, and trustworthy.
Organizations that understand and implement robust hash algorithms not only enhance their security posture but also build digital resilience in an increasingly interconnected world.
Ready to Strengthen Your Data Security?
Protect your systems with enterprise-grade cybersecurity solutions.
👉 Get Started with Xcitium Today
Frequently Asked Questions (FAQ)
1. What is a hash function used for?
Hash functions are used for data verification, password storage, and ensuring data integrity. They play a critical role in digital signatures, encryption protocols, and blockchain systems.
2. Can a hash function be reversed?
No. Hash functions are designed to be one-way—you can’t retrieve the original input from the hash value.
3. Is SHA-256 still secure?
Yes. SHA-256 is currently considered secure and widely used for password hashing, SSL certificates, and blockchain encryption.
4. What’s the difference between MD5 and SHA-256?
MD5 generates a 128-bit hash and is outdated due to collision risks.
SHA-256, on the other hand, creates a 256-bit hash and offers much stronger security.
5. How does hashing protect passwords?
Instead of storing plain text passwords, systems store their hash values. Even if attackers access the database, they can’t easily recover the original passwords.