How to Prevent SQL Injection: A Complete Security Guide
Updated on October 16, 2025, by Xcitium
Did you know that SQL injection (SQLi) remains one of the top web application vulnerabilities, according to OWASP? Despite being well-known, thousands of organizations still fall victim each year. SQL injection attacks allow hackers to manipulate databases, steal sensitive data, or even take full control of an application.
Introduction: Why SQL Injection Is Still a Threat
For IT managers, cybersecurity experts, and business leaders, understanding how to prevent SQL injection is crucial. In this guide, we’ll explore what SQL injection is, why it happens, and actionable steps to secure your systems.
1. What Is SQL Injection?
SQL injection is a type of injection attack where malicious SQL statements are inserted into input fields of an application. If the application doesn’t properly validate or sanitize user input, the attacker can gain unauthorized access to databases.
Common Targets of SQL Injection:
-
Login forms
-
Search boxes
-
URL parameters
-
API endpoints
👉 Example of a vulnerable query:
If input isn’t validated, an attacker could enter:
This would bypass authentication and grant unauthorized access.
2. Why SQL Injection Is Dangerous
SQL injection isn’t just about database access—it can have devastating consequences.
Risks of SQL Injection:
-
Data Theft: Exposes usernames, passwords, credit card numbers.
-
Data Manipulation: Hackers can delete or alter data.
-
Privilege Escalation: Gain administrator-level access.
-
Reputation Damage: Loss of customer trust and compliance fines.
👉 According to IBM’s 2023 X-Force report, SQL injection was among the top three initial attack vectors exploited by cybercriminals.
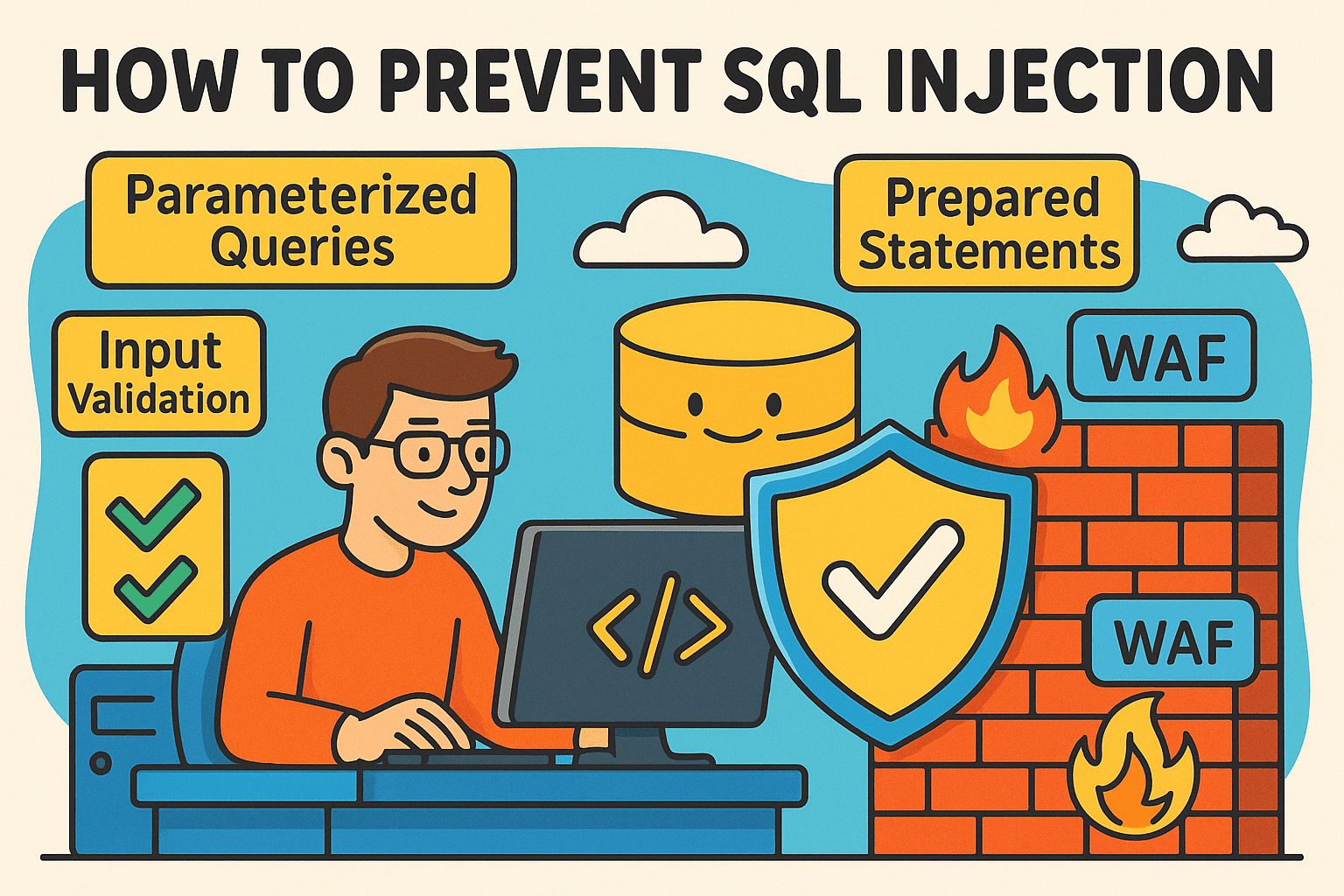
3. How to Prevent SQL Injection
Preventing SQL injection requires a multi-layered defense strategy.
A. Use Parameterized Queries (Prepared Statements)
Instead of directly concatenating user input, use parameterized queries.
Example in Python (with SQLite):
Benefits:
-
Prevents attackers from injecting malicious SQL.
-
Forces input to be treated as data, not executable code.
B. Input Validation and Sanitization
-
Only accept expected data types (e.g., numeric values where numbers are required).
-
Reject dangerous characters like quotes (
'), semicolons (;), and comments (--). -
Use whitelisting instead of blacklisting.
👉 Example: If a user ID must be numeric, ensure only numbers are accepted.
C. Use Stored Procedures Safely
Stored procedures can reduce risk, but only if they’re properly implemented.
Bad example (still vulnerable):
Safe example:
D. Apply Least Privilege Principles
-
Database accounts used by applications should have minimum required privileges.
-
Avoid using
rootor admin accounts for database connections. -
Segregate read-only and write access accounts.
👉 This limits damage even if SQL injection occurs.
E. Use ORM (Object Relational Mapping) Tools
Frameworks like Hibernate, Django ORM, or Entity Framework handle SQL generation safely, reducing direct exposure to raw queries.
F. Employ Web Application Firewalls (WAFs)
-
A WAF can detect and block malicious SQL injection patterns.
-
Acts as a secondary defense when developers miss vulnerabilities.
-
Works well in hybrid and cloud environments.
G. Regular Security Testing
-
Perform penetration testing to simulate SQL injection attacks.
-
Use automated tools like SQLMap for vulnerability scanning.
-
Follow the OWASP Testing Guide for best practices.
4. Real-World Examples of SQL Injection
-
Sony Pictures Hack (2011): Attackers used SQLi to expose millions of user records.
-
TalkTalk Breach (2015): A teenager exploited SQL injection to access personal customer data, costing the company £77 million.
-
British Airways Fine (2018): SQLi vulnerabilities contributed to breaches affecting 380,000 transactions.
👉 Lesson: Even big enterprises can fall if SQLi defenses are overlooked.
5. SQL Injection Prevention Checklist for IT Leaders
Here’s a quick action plan for your organization:
-
✅ Always use parameterized queries
-
✅ Validate and sanitize all user inputs
-
✅ Avoid dynamic SQL at all costs
-
✅ Apply least privilege access controls
-
✅ Regularly patch and update databases
-
✅ Deploy WAFs for additional protection
-
✅ Conduct regular code reviews and penetration tests
6. The Future: Modern Approaches to SQLi Prevention
-
Zero Trust Security: Assume every input is malicious until validated.
-
AI-powered Security Tools: Detect abnormal database queries.
-
DevSecOps Integration: Embed security testing into CI/CD pipelines.
-
Cloud-native Protections: Cloud WAFs and managed database services help reduce exposure.
Quick Recap: How to Prevent SQL Injection
-
Use prepared statements to avoid unsafe query concatenation.
-
Sanitize and validate all inputs.
-
Apply least privilege to database accounts.
-
Deploy WAFs and perform regular testing.
-
Learn from real-world breaches to stay ahead of attackers.
FAQs on Preventing SQL Injection
1. What is the easiest way to prevent SQL injection?
The most effective method is using parameterized queries or prepared statements.
2. Are stored procedures always safe?
No. Poorly written stored procedures can still be vulnerable.
3. Can a WAF completely stop SQL injection?
A WAF is an important layer of defense, but it should be combined with secure coding practices.
4. How do I know if my site is vulnerable?
Run penetration tests using tools like SQLMap or hire a professional security team.
5. Is SQL injection still common in 2025?
Yes. Despite awareness, many legacy systems and poorly coded apps remain vulnerable.
Final Thoughts
Learning how to prevent SQL injection is not just a developer’s responsibility—it’s a business-critical priority. By combining secure coding, access control, and ongoing testing, organizations can reduce the risk of one of the most damaging cyberattacks.
🚀 Want to ensure your organization is fully protected against SQL injection and other threats?
Request a demo from Xcitium and explore advanced endpoint and application security solutions.