Supply Chain Attack: Why Xcitium Is the Best Choice Over CrowdStrike for IT Security
Updated on September 17, 2025, by Xcitium
In today’s hyper-connected world, businesses depend on an increasingly complex ecosystem of third-party tools, open-source libraries, and cloud services. While this interconnectedness fuels innovation and agility, it also opens the door to one of the most dangerous modern cyber threats: the supply chain attack.
Recent headlines have highlighted the devastating effects of these attacks, including the compromise of CrowdStrike’s npm packages. This incident exposed how even major security vendors can fall victim to malicious code injected into trusted software dependencies. The lesson is clear: no organization is immune.
This article explores what supply chain attacks are, why they’re so dangerous, and how Xcitium outperforms CrowdStrike in protecting organizations from these threats.
What Is a Supply Chain Attack?
A supply chain attack is when attackers compromise the software, services, or hardware that organizations rely on — usually through trusted third parties. Instead of targeting an organization directly, hackers manipulate upstream vendors or open-source projects to insert malicious code. Once that code reaches downstream users, it can steal data, exfiltrate credentials, or even spread like a worm.
Key features of supply chain attacks:
- Trusted path exploitation: Users assume updates are safe.
- Widespread reach: A single compromised package can affect thousands of companies.
- Stealth: Malicious code often hides in plain sight, avoiding detection until it’s too late.
- Business impact: Breaches can result in downtime, regulatory fines, and reputational damage.
The CrowdStrike npm breach serves as a prime example of how devastating such an attack can be.
The CrowdStrike npm Attack
malicious actors compromised several npm packages published under CrowdStrike’s account. The attack injected code designed to:
- Steal API keys, tokens, and credentials from development environments.
- Exfiltrate sensitive environment variables to attacker-controlled servers.
- Spread automatically to other dependent projects, acting like a self-replicating worm.
While CrowdStrike responded quickly and confirmed that its Falcon sensor was not impacted, the incident highlighted a critical weakness: reliance on detection-based defenses leaves a dangerous gap.
CrowdStrike: Strengths and Limitations
CrowdStrike is a recognized leader in endpoint detection and response (EDR). Its Falcon platform is widely adopted and trusted by enterprises worldwide.
Strengths of CrowdStrike:
- Cloud-native EDR platform with excellent threat intelligence.
- Strong detection and behavioral analysis capabilities.
- Wide integration ecosystem and global brand reputation.
Limitations in the context of supply chain attacks:
- Detection-first model: Relies on identifying malicious behavior, which can take time.
- Exposure window: During this lag, compromised packages may already exfiltrate data.
- High cost: Falcon’s enterprise pricing can be prohibitive for SMBs or budget-conscious organizations.
- Complexity: Requires skilled SOC teams to maximize value.
In supply chain attack scenarios, these gaps can be exploited.
Xcitium: A Prevention-First Approach
Xcitium (formerly Comodo) takes a different philosophy: it doesn’t just detect threats — it prevents them from executing harm. This prevention-first model is especially powerful against supply chain attacks.
Core strengths of Xcitium:
- Default Deny & Auto-Containment
- Unknown files are automatically isolated in a virtualized environment until verified safe.
- Prevents malicious npm packages or zero-day payloads from accessing sensitive data.
- Zero-Dwell Protection
- Reduces attacker dwell time to near zero.
- Stops threats instantly instead of waiting for detection or human analysis.
- Virtualization Technology
- OS-level and CPU-level containment ensures minimal system impact.
- Users can continue working without disruption, even when files are under analysis.
- Comprehensive Security Suite
- Endpoint protection, patch management, mobile device security, and remote monitoring.
- Tools for both SMBs and enterprises with flexible deployment options.
- Cost-Effective SOC & MDR
- 24/7 managed detection and response without enterprise-level price tags.
- Makes advanced protection accessible to smaller organizations.
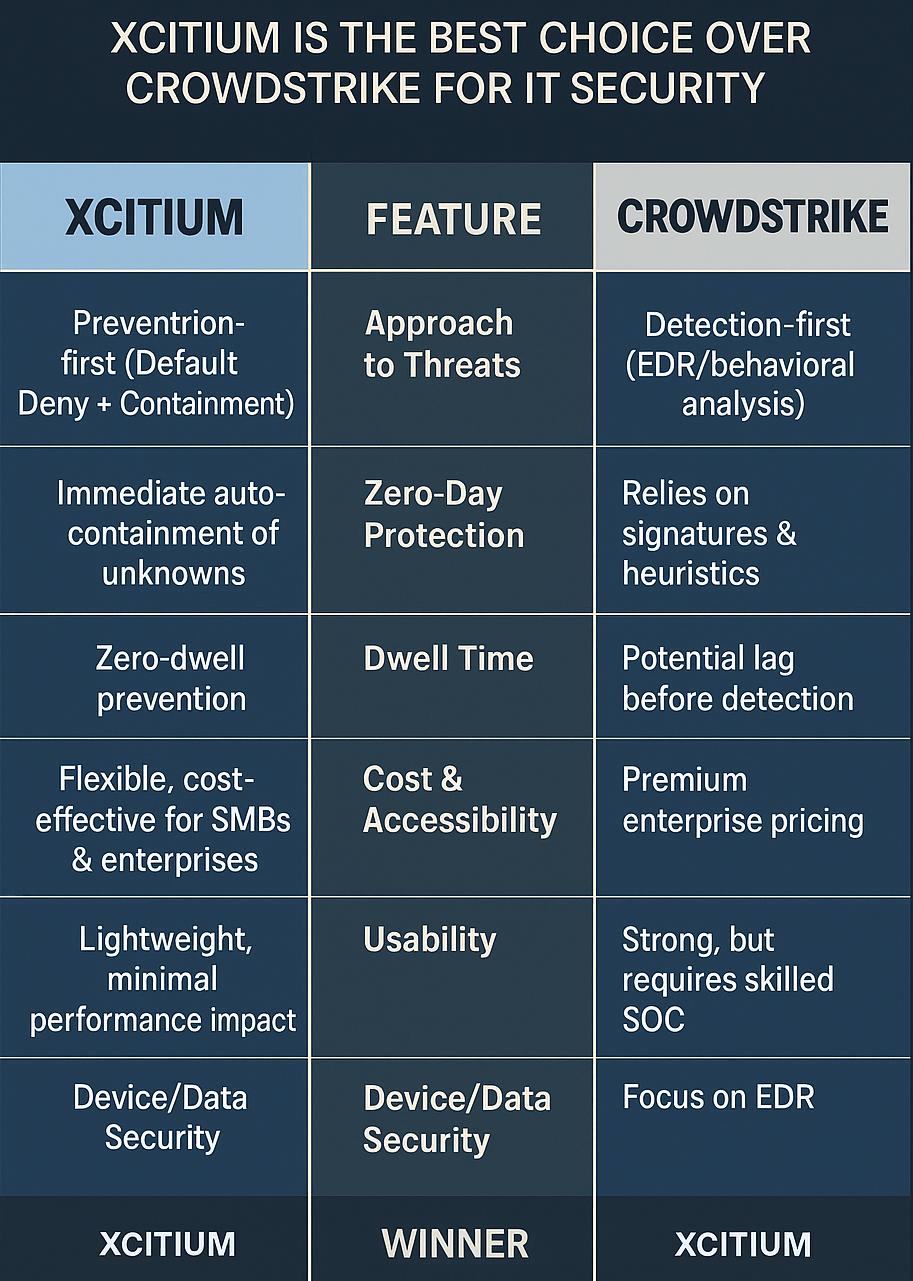
Xcitium vs CrowdStrike: Head-to-Head Comparison
| Feature | CrowdStrike | Xcitium | Winner |
| Approach to Threats | Detection-first (EDR/behavioral analysis) | Prevention-first (Default Deny + Containment) | Xcitium |
| Zero-Day Protection | Relies on signatures & heuristics | Immediate auto-containment of unknowns | Xcitium |
| Dwell Time | Potential lag before detection | Zero-dwell prevention | Xcitium |
| Cost & Accessibility | Premium enterprise pricing | Flexible, cost-effective for SMBs & enterprises | Xcitium |
| Usability | Strong, but requires skilled SOC | Lightweight, minimal performance impact | Xcitium |
| Device/Data Security | Focus on EDR | Adds remote wipe, data isolation, BYOD protection | Xcitium |
Why Xcitium Is Better for Supply Chain Attack Protection
- Stops Unknown Threats Immediately: Malicious npm or open-source packages are isolated instantly.
- Reduces Risk of Credential Theft: Containment prevents malware from accessing tokens or environment variables.
- Minimizes Business Impact: Zero-dwell technology stops attacks before they cause downtime.
- Affordable for All Sizes: Enterprises and SMBs alike benefit without breaking budgets.
- Built for Resilience: Additional device and data protection features make Xcitium a full-spectrum solution.
In short, Xcitium doesn’t just compete with CrowdStrike — it fills the gaps that detection-based platforms can’t address.
Practical Steps for Organizations
In light of recent supply chain breaches, here’s how businesses can protect themselves — and how Xcitium helps:
- Audit Dependencies: Identify third-party libraries in use.
- Enforce Least Privilege: Limit developer and admin access.
- Automate Patching: Use Xcitium’s centralized patch management.
- Deploy Auto-Containment: Neutralize zero-day or malicious files instantly.
- Implement Continuous Monitoring: RMM and MDR services provide proactive oversight.
Conclusion
The supply chain attack has become one of the most dangerous threats to modern IT environments. The CrowdStrike npm compromise demonstrates that even top-tier security vendors can fall victim.
While CrowdStrike is strong in detection and response, Xcitium delivers superior protection by focusing on prevention, containment, and zero-dwell security. With its lightweight virtualization, cost-effective MDR, and prevention-first approach, Xcitium offers organizations the confidence that even unknown or zero-day supply chain threats cannot cause harm.
For businesses serious about IT security, the choice is clear: Xcitium is the smarter defense against supply chain attacks.
👉 Learn more at Xcitium.com
Frequently Asked Questions (FAQs)
1. What is a supply chain attack in cybersecurity?
A supply chain attack targets the vendors, tools, or libraries an organization depends on, inserting malicious code upstream so it spreads downstream into trusted environments.
2. How was CrowdStrike affected by a supply chain attack?
Several npm packages published under CrowdStrike’s account were compromised with malicious code. Although Falcon itself wasn’t impacted, the incident revealed vulnerabilities in open-source ecosystems.
3. How does Xcitium protect against supply chain attacks?
Xcitium uses auto-containment and default deny policies to isolate unknown files immediately. This ensures malicious code from compromised packages cannot access or steal sensitive data.
4. Is Xcitium better than CrowdStrike for zero-day threats?
Yes. While CrowdStrike focuses on detection, Xcitium prevents zero-day threats from causing harm by isolating them instantly, reducing dwell time to zero.
5. Is Xcitium suitable for small and medium-sized businesses?
Absolutely. Xcitium offers cost-effective SOC and MDR services, making enterprise-grade protection accessible to SMBs as well as large enterprises.