Why Hashing Matters More Than You Think
Updated on June 5, 2025, by Xcitium
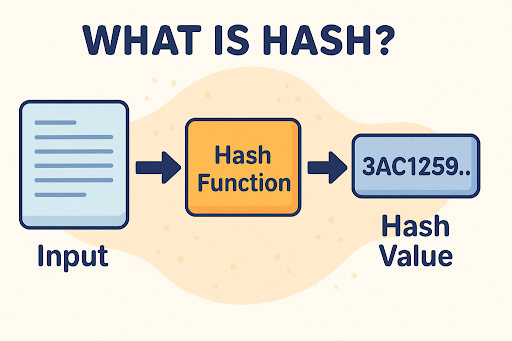
In today’s data-driven world, verifying authenticity and protecting integrity is paramount. But how do systems detect if your password or critical files have been tampered with? The answer lies in a powerful mathematical concept: the hash.
Understanding what is hash is essential for anyone in cybersecurity, IT management, or software architecture. From securing passwords to verifying blockchain transactions, hashes ensure digital trust. In this article, we’ll explore the fundamentals of hashing, how it works, how it differs from encryption, and the types of hashing algorithms used across industries.
What Is Hash? (Definition & Cybersecurity Relevance)
A hash is a fixed-length string of characters (also called a digest) generated by a mathematical algorithm from input data of any size. It’s a one-way process, meaning you cannot reverse the hash to retrieve the original data.
Core Characteristics:
- Deterministic: Same input = same output.
- One-way: Impossible to reconstruct original input.
- Fast computation: Quick to generate.
- Collision-resistant: Unlikely two inputs produce same output.
- Fixed length: Output size is constant regardless of input.
In cybersecurity, hashing is widely used for:
- Storing and verifying passwords
- File integrity checks
- Digital signatures
- Blockchain validation
- Message authentication
How Hashing Works (Step-by-Step Breakdown)
Understanding how hashing works starts with the transformation of data through a hash function. Let’s explore the process:
Example:
Input: “Cybersecurity is vital.”
Hash (SHA-256):
3cc67f3fdf62e44a2b1f1b93a19388e1f0c08a207d707a47f803c823462dcabd
Steps:
- Input Data: Can be text, file, or code.
- Hash Function: Applies complex mathematical operations.
- Fixed-Length Output: Typically 128-bit, 256-bit, or more.
Hashing is used in password storage, where systems store the hash of your password. When you log in, the entered password is hashed and compared to the stored value. If they match, access is granted.
Types of Hashing Algorithms
There are several hashing algorithms, each with its own use cases and levels of security. Let’s explore the most prominent types of hashing algorithms:
1. MD5 (Message Digest 5)
- 128-bit output
- Fast but vulnerable to collision attacks
- Now considered outdated for secure systems
2. SHA-1 (Secure Hash Algorithm 1)
- 160-bit output
- Better than MD5 but also deprecated for cryptographic use
3. SHA-256 / SHA-3
- Stronger and widely used
- 256-bit output in SHA-256
- Used in Bitcoin and modern encryption systems
4. Bcrypt
- Designed for password hashing
- Incorporates a salt and is slow to compute—ideal for security
5. Argon2
- Winner of the Password Hashing Competition
- Provides memory-hard and side-channel attack resistance
| Algorithm | Output Size | Best For | Security Status |
| MD5 | 128-bit | Checksums | Insecure |
| SHA-1 | 160-bit | Legacy | Broken |
| SHA-256 | 256-bit | Signatures, Blockchain | Secure |
| Bcrypt | Variable | Passwords | Strong |
| Argon2 | Variable | Passwords | Cutting-edge |
Hash vs Encryption: What’s the Difference?
A common misconception is that hashing and encryption are the same. While both are fundamental to cybersecurity, they serve different purposes.
Key Differences Between Hash and Encryption:
| Feature | Hashing | Encryption |
| Direction | One-way | Two-way (encrypt/decrypt) |
| Use Case | Verify data integrity | Protect data confidentiality |
| Output | Fixed-length digest | Variable-length cipher text |
| Reversible | No | Yes (with decryption key) |
| Example Use | Password storage, integrity | Secure messaging, file access |
Hashing is about validation. Encryption is about secrecy.
Real-World Use Cases of Hashing
Hashing isn’t just a theoretical concept. It’s widely used in industries like finance, government, and healthcare. Here are a few examples:
1. Digital Signatures
Ensures document integrity. The original document is hashed; if the hash changes, the document is compromised.
2. Password Management
Most secure systems never store your password—only its hash (ideally with salt and Bcrypt or Argon2).
3. File Integrity Verification
Used in malware detection and secure file downloads. If the file’s hash changes, it may be infected.
4. Blockchain
Each block’s hash depends on the previous, creating an immutable chain.
5. SSL Certificates
Hash functions help generate digital certificates to establish trust in browsers.
Common Attacks on Hashing (and How to Prevent Them)
1. Collision Attacks
Two inputs yield the same hash. Modern algorithms like SHA-256 mitigate this.
2. Rainbow Table Attacks
Uses precomputed hash tables to reverse-engineer passwords. Prevention: use salting.
3. Brute Force Attacks
Tries every combination. Use slow algorithms like Bcrypt or Argon2 to make brute force unfeasible.
4. Length Extension Attacks
Certain algorithms like MD5 and SHA-1 are vulnerable. Avoid legacy hashing algorithms.
Best Practices for Hashing in Cybersecurity
- Use modern algorithms like SHA-3, Bcrypt, or Argon2.
- Always apply salting to passwords.
- Prefer key-stretching techniques for password hashes.
- Never rely on MD5 or SHA-1 for secure applications.
- Audit and test the hashing logic in your security architecture.
Conclusion: Why Hashing Is Foundational for Cybersecurity
Understanding what hash is is crucial for building secure applications, verifying integrity, and protecting sensitive data. From password protection to blockchain and secure messaging, hashing plays a silent yet essential role in cybersecurity infrastructure.
Don’t leave your data to chance—Request a Demo with Xcitium to explore advanced cybersecurity solutions that incorporate best-in-class hashing and encryption technologies.
FAQ: What You Should Know About Hashing
1. What is a hash in simple terms?
A hash is a unique fingerprint of data, generated by a formula that can’t be reversed. It’s used to verify data without exposing it.
2. Why is hashing important in cybersecurity?
It protects data integrity, authenticates users, and supports encryption systems without storing sensitive information directly.
3. Is hashing better than encryption?
Not better—just different. Hashing is for verification, and encryption is for confidentiality.
4. Can a hash be decrypted?
No. Hashing is a one-way function. You cannot retrieve the original data from a hash.
5. Which hashing algorithm is most secure?
SHA-3 and Argon2 are among the most secure today, depending on the use case.