Protect First - With Patented Virtualization.
Then Employ Detection, Verdicting, And Forensic Technologies To Harden Your Environment
ZeroDwell is a clearcut, proven solution that precedes detection-first security strategies to provide protection from ransomware and malware infections. Meanwhile, it simultaneously eliminates alert fatigue, slashes work loads for your IT and analyst teams, and abolishes big breach remediation budgets.
EXPLORE PLATFORM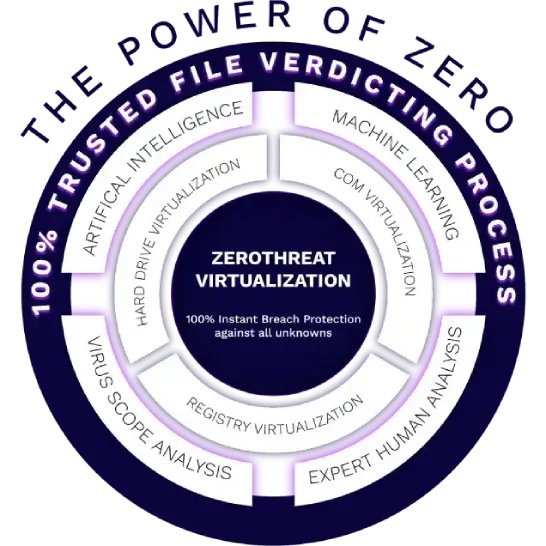
A major feature of ZeroThreat technology is ZERODWELL CONTAINMENT™ (ZDC). With ZDC, Xcitium reduces the amount of time a threat can maneuver or dwell in your environment, down to absolute zero. ZDC is the foundation of ZeroDwell's instantaneous kernel-level virtualization of unknown at runtime.
Attacks happen in minutes and seconds. But the impact from an attack does not always occur instantly. It can take some dwell time for an intruder to get a foothold and enumerate to execute search and destroy or exfiltration missions. Xcitium's ZDC intercepts and isolates the attack before any of its impact and intended damage can occur.
It's a race, and Xcitium leads with a disruptive, strategic offense. ZeroDwell provides an unfair advantage for defenders. When it comes to unknown entering your endpoints, we protect first, then ask questions and identify, detect and verdict second. That's Xcitium's unique advantage.

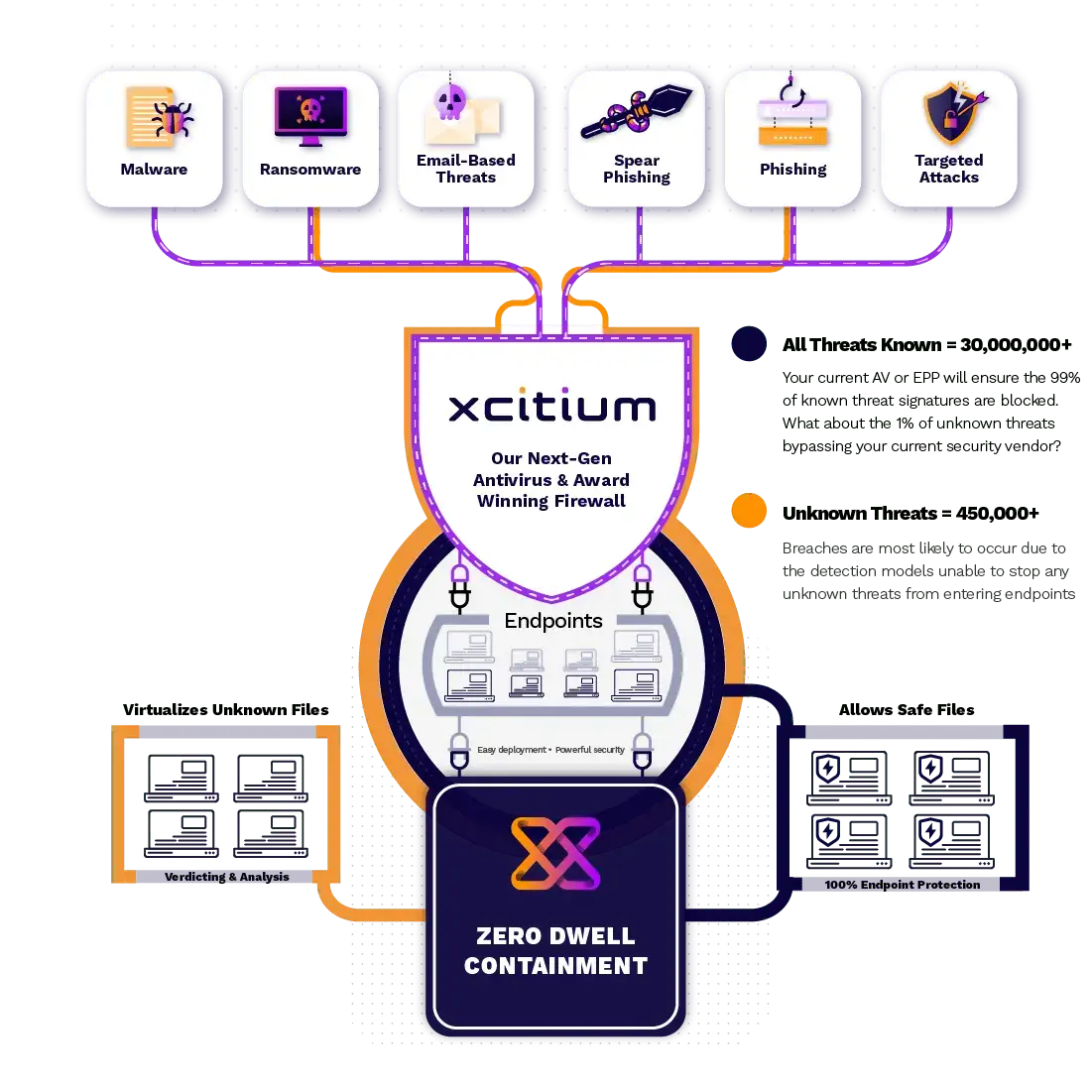
How We Help
Equip every endpoint, network, and workload with the latest threat intelligence against cyber threat signatures and payloads.
Defense against new or zero-day cyber threats using powerful static, dynamic, and patented behavioral AI.
Prevent unknown cyber attacks from causing damage to your endpoints with our lightweight Kernel-level API virtualization.
Gain full context of an attack to connect the dots on how hackers are attempting to breach your network.
Securing our customers are our #1 priority. Global industry leaders have validated our endpoint security solutions through rigorous testing. They rely on Xcitium to prevent breaches by using ZeroDwell that neutralizes ransomware, malware and cyber attacks. The Xcitium Enterprise Platform protects millions of endpoints daily from cyber threats.
EXPLORE CUSTOMER STORIES
Gain full context of an attack to connect the dots on how hackers are attempting to breach your network with ZeroDwell Containment, EPP, and Next-Gen EDR.
We continuously monitor endpoint device activities and policy violations, and provide threat hunting and SOC Services, with 24/7 eyes on glass threat management. Managed SOC services for MSPs and MSSPs.
Outsourced Zero Trust managed - security with options for protecting endpoints clouds and/or networks, as well as threat hunting, SOC Services, with 24/7 expert eyes on glass threat management.
Xcitium's Cloud Native Application Protection Platform (CNAPP) provides automated Zero Trust cloud security for cloud-based applications and cloud workloads, including infrastructure DevOps from code to runtime.
