Have you ever wondered, what does SQL stand for and why it matters so much in technology, business,...

Have you ever wondered, what does ERP stand for, and why it’s so frequently mentioned in...

What is smishing? If you’ve ever gotten a text message claiming to be from your bank or a...

What is a DDoS attack, and why should it be on every IT manager’s radar? If your website or...
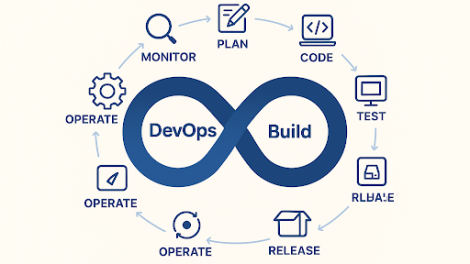
In a world where speed, security, and reliability define success, businesses can no longer afford...
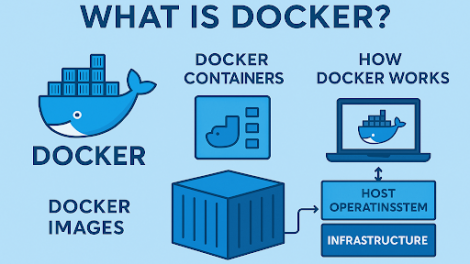
How do tech giants like Netflix, PayPal, and Spotify roll out updates with zero downtime and...

Can machines really learn like humans? If you’ve ever used a voice assistant, received a fraud...
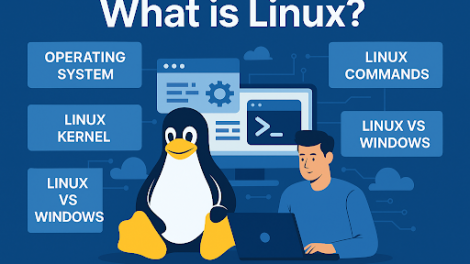
Have you ever wondered what powers your Android phone, the world’s fastest supercomputers, and...
Have you ever wondered how search engines rank results, how Netflix recommends your next binge, or...

What is PII and why is it the cornerstone of modern data protection strategies? In 2024 alone, over...