🚀 MDR for Microsoft: The Complete Conversational Guide to Modern Threat Protection (2026)
Updated on November 21, 2025, by Xcitium
Cyberattacks are getting smarter, faster, and more aggressive every year. Even companies using Microsoft’s security stack — including Microsoft Defender, Azure AD, and Microsoft 365 — still struggle to keep up with alert overload, cloud threats, identity attacks, and ransomware. That’s exactly why MDR for Microsoft has become one of the most important cybersecurity services in 2025.
If you’ve been wondering what MDR for Microsoft is, why businesses need it, or how it works, you’re in the perfect place. This friendly, conversational guide explains everything you need to know — without the jargon.
Let’s dive in.
What Is MDR for Microsoft? (Simple Explanation)
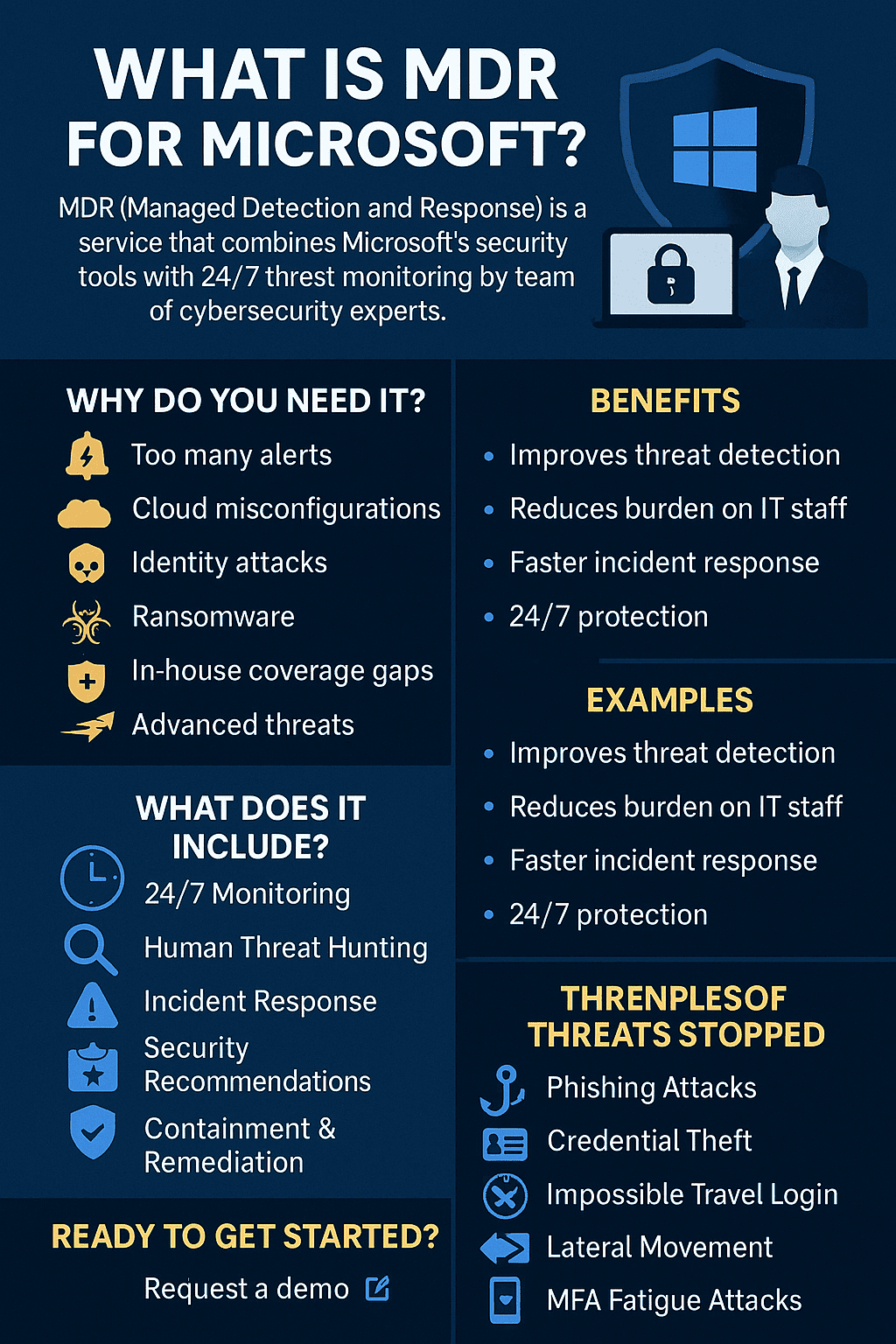
MDR for Microsoft is a managed security service that combines Microsoft’s powerful security tools with a 24/7 team of cybersecurity experts.
In simple terms:
👉 Microsoft provides the security tools. MDR provides the humans who monitor them.
MDR for Microsoft includes:
-
24/7 threat monitoring
-
Human threat hunting
-
Rapid incident response
-
Deep investigation of alerts
-
Containment & remediation support
-
Security recommendations
-
Expert oversight
You can think of MDR as a full Security Operations Center (SOC), but outsourced, affordable, and always awake.
Why Microsoft Security Alone Isn’t Enough
Microsoft Defender, Sentinel, and M365 security tools are excellent — but they’re not “set and forget.”
Businesses still face challenges like:
✔ Too many alerts
IT teams get overloaded.
✔ Complex identity attacks
Attackers target Azure AD & Microsoft 365 users.
✔ Cloud misconfigurations
One wrong setting can expose sensitive data.
✔ Ransomware targeting Windows endpoints
Microsoft’s tools detect threats — but someone needs to analyze them.
✔ No 24/7 in-house team
Most companies don’t have round-the-clock coverage.
✔ Advanced threats bypassing automation
Human adversaries require human defenders.
This is why MDR for Microsoft exists — to bridge the gap.
What MDR for Microsoft Actually Includes
Let’s break down what MDR providers do behind the scenes.
1. 24/7 Monitoring & Response
Security analysts actively monitor:
-
Microsoft Defender for Endpoint
-
Microsoft Defender for Identity
-
Microsoft Defender for Cloud Apps
-
Azure AD login events
-
Microsoft 365 anomalies
-
Endpoint behaviors
-
Email threats
If something looks suspicious, they investigate immediately.
2. Human-Led Threat Hunting
Humans go beyond automated alerts. They look for:
-
Lateral movement
-
Hidden persistence
-
Credential theft
-
Phishing attempts
-
Ransomware staging
-
Privilege escalation
-
Abnormal user behavior
Threat hunting finds attacks that AI alone cannot.
3. Incident Response & Containment
When a threat is discovered, MDR teams can:
-
Isolate devices
-
Kill malicious processes
-
Block attacker IPs
-
Disable compromised accounts
-
Remove malware
-
Guide internal teams step-by-step
This dramatically reduces breach impact.
4. Real-Time Notification
Businesses receive clear, actionable alerts like:
“Suspicious PowerShell activity blocked. Threat contained. No further action required.”
Not confusing logs. Not thousands of alerts.
Just clear answers.
5. Proactive Security Recommendations
MDR teams help you harden your Microsoft environment by advising on:
-
Conditional access
-
MFA
-
Identity settings
-
Endpoint policies
-
Data leak prevention
-
Cloud configurations
This prevents future attacks.
How MDR for Microsoft Works (Step-by-Step)
Here’s the lifecycle of a typical attack detection.
Step 1: Data Collection
Telemetry flows from Microsoft:
-
Defender
-
Azure AD
-
Office 365
-
Cloud Apps
-
Endpoints
Step 2: Automated Analysis
Microsoft’s AI flags suspicious patterns.
Step 3: Human Investigation
MDR analysts review:
-
Activity logs
-
Device alerts
-
User behavior
-
Threat intelligence
Step 4: Threat Hunting
Analysts search for related activity or hidden evidence.
Step 5: Containment & Remediation
Analysts isolate devices or disable accounts.
Step 6: Reporting & Prevention
Businesses receive:
-
Root-cause analysis
-
Attack timeline
-
Remediation guidance
-
Hardening recommendations
Benefits of MDR for Microsoft
✔ 24/7 security — even when your team is offline
✔ Reduces ransomware risk
✔ Saves IT teams from alert fatigue
✔ Faster response = less damage
✔ Gives businesses SOC-level protection
✔ Helps meet compliance (HIPAA, PCI-DSS, SOC2)
✔ Protects hybrid and remote environments
✔ Strengthens Microsoft’s built-in security
Simply put:
👉 MDR for Microsoft turns your Microsoft environment into a fully protected, expertly monitored ecosystem.
Where MDR for Microsoft Makes the Biggest Impact
✔ Small and mid-sized businesses
They can’t afford a full security team.
✔ Enterprises with complex Microsoft environments
Identity attacks are skyrocketing.
✔ Remote-first organizations
Microsoft 365 becomes the primary attack surface.
✔ Regulated industries
Healthcare, finance, and government require 24/7 monitoring.
✔ MSPs & IT service firms
Offload SOC responsibilities.
🔐 MDR for Microsoft vs. Traditional SOC
| Feature | Traditional SOC | MDR for Microsoft |
|---|---|---|
| Cost | High | Affordable |
| Deployment | Complex | Fast |
| Alert Fatigue | High | Low |
| Response Time | Hours | Minutes |
| Coverage | Business hours | 24/7 |
| Integration | Multi-tool | Microsoft-native |
| Threat Visibility | Limited | Full Microsoft ecosystem |
MDR for Microsoft + Zero Trust
MDR reinforces Zero Trust by providing:
-
Continuous monitoring
-
Identity analytics
-
Conditional access tuning
-
Device health validation
-
Real-time containment
Zero Trust requires visibility — MDR provides it.
MDR for Microsoft vs. Microsoft Defender
Here’s the difference in simple terms:
Microsoft Defender = security tool
MDR for Microsoft = security team
Defender protects devices
MDR protects your entire organization
🧠 Examples of Threats MDR for Microsoft Stops
-
Ransomware encryption attempts
-
Phishing attacks inside Microsoft 365
-
Unusual admin account activity
-
Impossible travel logins
-
Fake OAuth app permissions
-
Suspicious PowerShell activity
-
Credential stuffing
-
MFA fatigue attacks
-
Cloud data exfiltration
Attackers are targeting Microsoft environments more than ever — MDR is critical.
🎯 Conclusion: MDR for Microsoft Is Essential in 2025
If you’ve been wondering why so many IT managers and security leaders are investing in MDR for Microsoft, here’s the bottom line:
👉 Microsoft gives you strong tools. MDR gives you the experts who make them unbeatable.
With 24/7 monitoring, rapid response, threat hunting, and deep Microsoft expertise, MDR significantly reduces your risk.
In a world full of nonstop cyber threats, MDR isn’t optional — it’s necessary.
🔐 Strengthen Your Microsoft Security with Xcitium MDR
Get proactive threat hunting, containment, and real-time protection.
👉 Request a free demo: https://www.xcitium.com/request-demo/
❓ FAQs About MDR for Microsoft
1. What does MDR for Microsoft include?
24/7 monitoring, threat hunting, response, and expert investigation.
2. Does MDR replace Microsoft Defender?
No. It enhances Defender by adding human expertise.
3. Is MDR for Microsoft good for small businesses?
Yes — SMBs benefit the most due to limited internal staff.
4. Can MDR stop ransomware?
Yes. Analysts detect early signs and isolate devices.
5. How fast is MDR response time?
Usually within minutes — far faster than in-house teams.