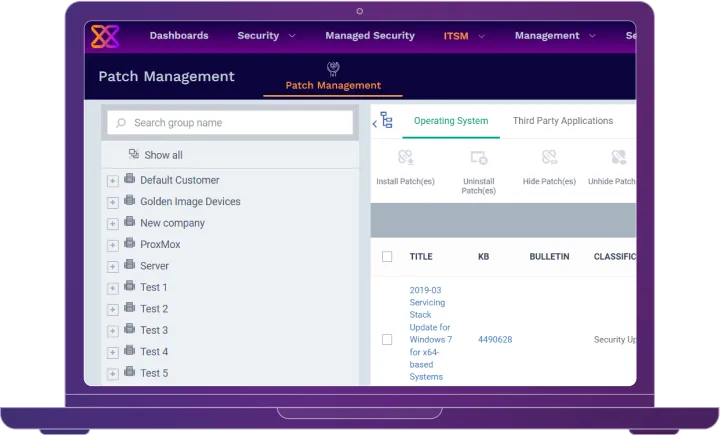
Patch Management
Keep your IT environment secure and compliant with Xcitium's Patch Management solution. Automate patch deployment, vulnerability management, and real-time monitoring to ensure your systems are always up to date and protected. With a centralized management console, customizable patch policies, and detailed reporting, Xcitium’s Patch Management streamlines the patching process and enhances security.
How It Works
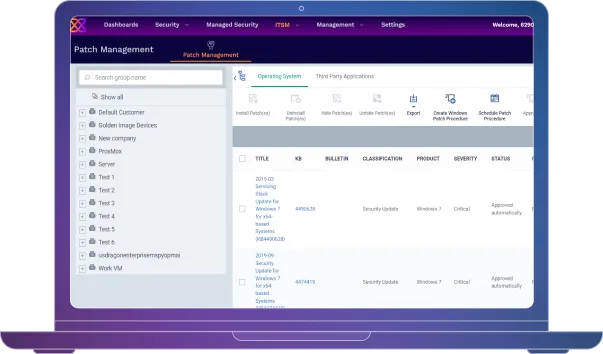
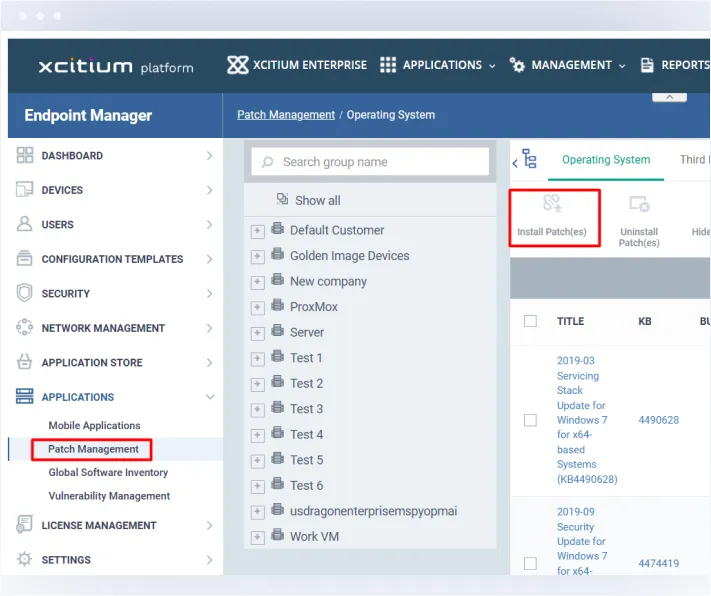
Xcitium's Patch Management solution automatically scans for and deploys patches for operating systems and applications. This ensures that your systems are always up to date and secure without the need for manual intervention. The platform identifies vulnerabilities within your IT environment and prioritizes patches based on risk level. This ensures that critical vulnerabilities are addressed promptly, reducing the risk of exploitation.
Key Features
Automatically scans and deploys patches for operating systems and applications, ensuring your systems are always up to date and secure without manual intervention.
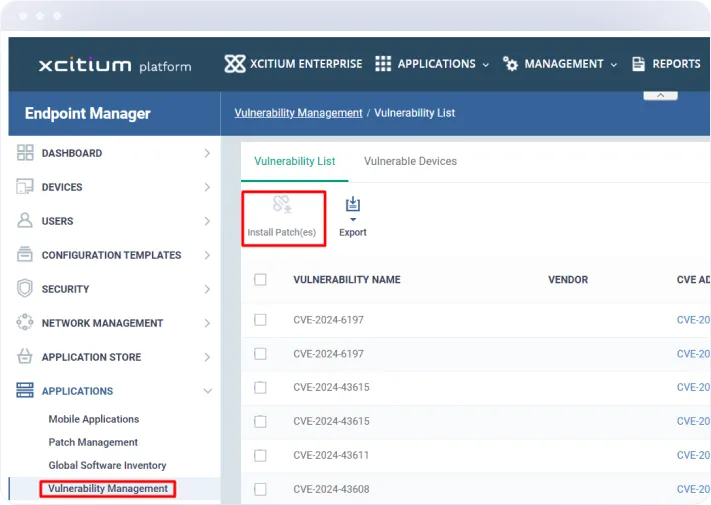
Comprehensive Vulnerability Management
Identifies vulnerabilities in your IT environment and prioritizes patches based on risk level, ensuring that critical vulnerabilities are addressed promptly.
Real-Time Patch Monitoring
Continuously monitors the status of patches across your infrastructure, providing real-time visibility into patch compliance and security posture.
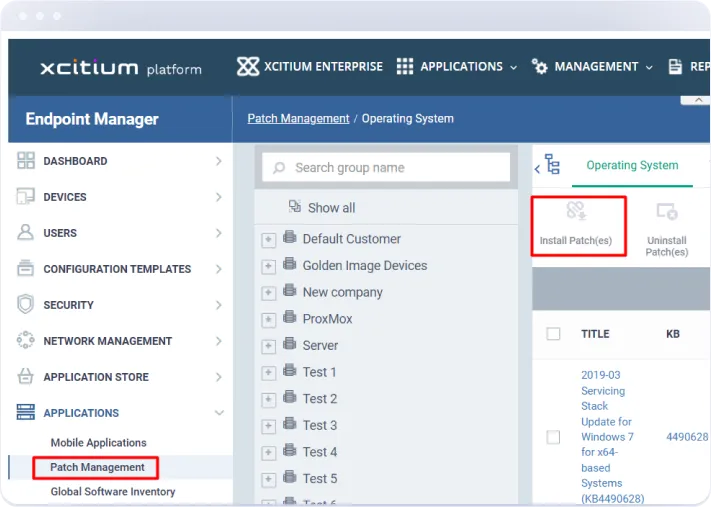
Centralized Patch
Management Console
Offers a centralized interface for managing patches across all devices and systems, simplifying the patch management process and improving efficiency.
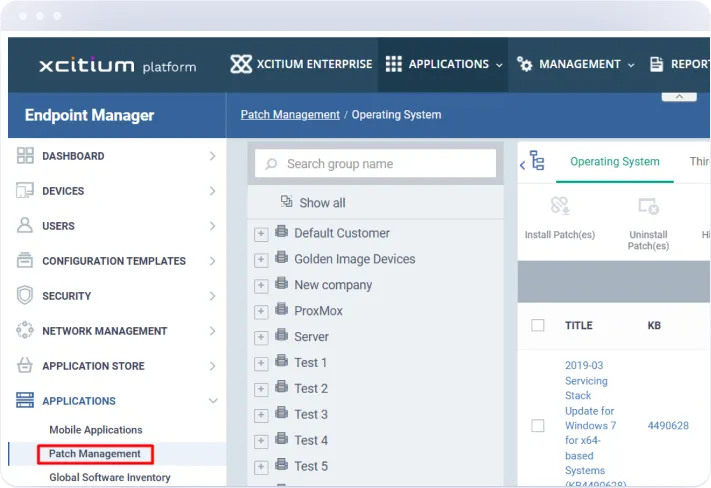
Customizable Patch Polices
Allows you to create and enforce patch policies tailored to your organization’s needs, ensuring that patches are applied in accordance with your specific security and compliance requirements.
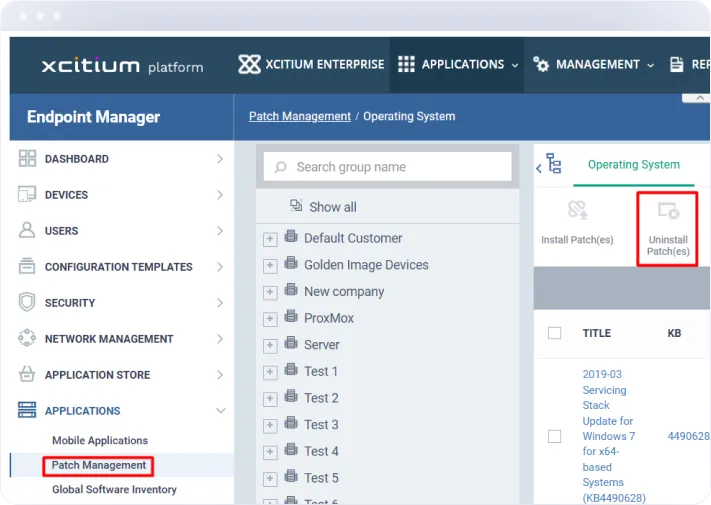
Rollback Capabilities
Provides the ability to roll back patches if issues arise, ensuring that you can quickly revert to a stable state without compromising security.
Benefits
Protection
Compliance
Flexibility
Why Choose Xcitium for Patch Management?
Choosing Xcitium for your Patch Management needs means opting for a robust and comprehensive solution that evolves with your business. Our Patch Management platform combines automated patch deployment, comprehensive vulnerability management, and real-time monitoring to provide unmatched security and efficiency. With a centralized management console, customizable patch policies, and detailed reporting, Xcitium’s Patch Management streamlines the patching process and enhances your security posture.





