Insider threats are individuals with access to company data who misuse it for malicious reasons. These could include employees, former employees, contractors, and any other types of insiders that put your organization in jeopardy.
They may be challenging to detect since their attacks do not usually leave any noticeable evidence behind, yet it is still possible to thwart these threats before they cause harm.
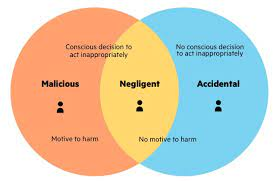
Malicious Insider Threats
Malicious insiders are individuals EDR or entities who use legitimate access to your organization's systems or network to cause disruption or damage, typically with financial gain as their motivation (though these attacks could also be performed for revenge or retaliation).
The goals of their attacks could range from stealing confidential data or damaging assets; most often, their goal is stealing personal data, while other attacks might aim at damaging assets directly. They typically use legal means like theft to gain entry - the end goal can include either taking confidential data for themselves or targeting assets now, the primary financial gain being their motivation. However, revenge or retaliation might also motivate these attacks against individuals or teams within organizations if someone breaches security for either.
Security teams need a complete picture of devices, people, and other entities across their organization to detect insider threats successfully. To detect insider attacks accurately and quickly.
This means providing full context around device and user profiles, business functions, email addresses, domain visits, files downloaded or accessed, relationships established between people using devices or applications, and events and activities conducted within an enterprise.
All these details should be tracked in real-time to facilitate correlation with future business events or activities.
One way to reduce insider threats is to monitor employee accounts and passwords closely, as this will limit how much data can be accessed by those intending to conduct a malicious attack against your company.
Make sure that your employees understand and are aware of your organization's security policy and guidelines to prevent unintended or negligent insider breaches in your organization. This will reduce incidents where unintentional violations occur due to negligence on behalf of employees.
As part of these measures, it is also vital that your employees receive ongoing training and guidance regarding security best practices. This could involve teaching employees about phishing emails, scams, and using personal devices within your organization.
As organizations grow and mature, their internal security policies and processes must evolve with them. Doing so can reduce risks posed by negligent employees while enabling their security team to identify and address threats quickly.
Malicious insiders typically target organizations to obtain assets or information to create money or obtain additional revenue streams. Additionally, these individuals often partner with criminal networks, which supply them with the resources to achieve their goals.
Insider Threats Disgruntled Employees
Disgruntled employees can be a severe detriment to any business. Their actions could wreak havoc with customer service, hamper productivity, and lead to decreased morale within your team. Therefore, taking proactive steps in dealing with disgruntled workers is essential for the success of your enterprise.
A practical approach for dealing with dissatisfied employees is showing kindness and empathy, as this will make your communication more efficient while allowing them to find solutions to their problems. By ending meetings positively, situations become much simpler to handle.
An unhappy employee could be upset for many reasons; to effectively address their anger quickly and prevent further damage to your company. Recognizing the early and accurate source is vital for a swift resolution.
If an employee is engaging in illegal behavior, possessing sensitive data, or abusing their access, immediately call the authorities. Otherwise, contact your human resources department for advice on the best course of action in your situation.
Your next best step may be speaking with a counselor or psychologist to determine an effective solution. Sometimes people need a voice in their work environment, which provides a safe way to express their concerns in a non-threatening way.
Another strategy would be to set up an individual meeting with the employee. This can often help identify what has caused their anger, as it's often more accessible for people to discuss these topics in private settings such as their rooms.
Assuring your employee feels heard and that they know you care will also show them you are willing to assist in solving their problem.
Establishing regular employee meetings as part of your business culture is recommended. Asking questions regularly will enable you to stay abreast of issues before they escalate into significant concerns while working toward solutions for employee concerns so they do not resurface in future discussions.
Insider Threats Collaborators
Collaborators are individuals or groups working toward a shared goal, such as passing a new crime bill. Collaboration not only benefits businesses but individuals as well.
Research has demonstrated the positive results of collaboration on employee satisfaction and retention rates and connecting companies with new customers.
However, it's essential to remember that collaborations often fail for numerous reasons, including cultural and social differences, personal relationships, or environmental influences.
Students may be resistant to collaborative work due to negative experiences in the classroom; however, collaborations that include individuals from various backgrounds can increase cognitive diversity and boost communication skills.
As it can be hard to distinguish between malicious and careless collaborators, it is crucial that employees receive proper education and closely observe their activities.
Malicious insiders usually intend to do harm; their motivation could stem from ideology, finances, or recruitment from external threats.
Financially motivated insiders could sell sensitive data for profit or provide it to competitors in exchange for jobs, which could cause irreparable harm to an organization's reputation.
Threats often find ways to circumvent firewalls and access policies, making it more difficult for organizations to detect them. Therefore, security software that can detect these threats is vitally important.
Insider Threats Lone Wolf
People commonly refer to individuals who prefer being alone as "lone wolves." Sometimes known as recluses, hermits, and even outcasts.
Lone wolves are a personality type that arises through experience and personal challenges, often through genetic inheritance or life experiences.
FAQ Section
Many individuals within an organization who commit harmful actions against their own company are motivated by financial gain. They exploit the access and resources provided to them as trusted members of the organization.
Insider threats can lead to data breaches, the unauthorized disclosure of sensitive information, loss of productivity, and damage to the organization's reputation. These factors can negatively affect how investors perceive the organization's security.
Detecting insider threats can be challenging because the individuals involved possess authorized credentials, making it harder to identify unauthorized or suspicious activities. The key is to identify unusual behavior patterns promptly to prevent potential security breaches.
Compromised employees or vendors pose the most significant risk as both the organization and the insiders themselves are unaware of their compromised status. This lack of awareness makes it difficult to detect and address the threat in a timely manner.