Troubleshooting issues, protecting against attacks, or optimizing environments require event logs; however, searching through them can be time-consuming and labor-intensive.
Centralized logging solutions send log data directly from production environments into an independent central repository, making search and analysis faster and trend detection quick for engineers.
1. Efficient Storage
Centralized Logging provides a central repository and analysis platform for all your log data, making it easier for teams to gain visibility, increase efficiencies, and minimize service disruptions.
An excellent centralized logging solution will also automatically compress logs and determine how long to retain them to reduce costs and free up server space. In addition, these solutions should minimize ingest latencies so you can view and search log data faster.
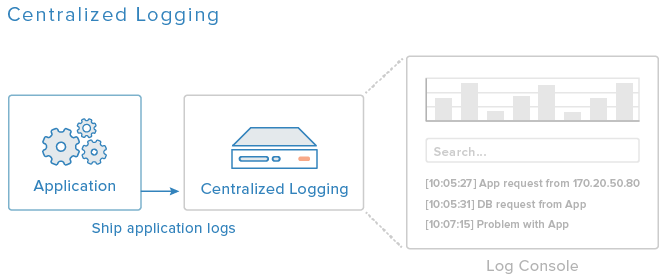
Centralized logging starts by gathering your server logs into one central platform for analysis, either by installing agents on each source system or relying on native methods (like Syslog daemon on servers). Once they arrive at this platform, logs are processed to turn them into useful information; this may involve filtering logs for relevance, normalizing timestamps across logs, and creating visualization charts.
Once indexed, logs can be searched and analyzed, accomplished through predefined charts and dashboards or customized ones. Centralized Logging can also monitor events that might impact your business, such as hardware failures or security threats.
A centralized logging solution can also enhance the performance and stability of your application by informing you about issues, improving monitoring, reducing errors, meeting compliance requirements, and helping meet regulatory obligations. It can also provide valuable business intelligence by uncovering opportunities to streamline operations, optimize network design, or improve customer experiences.
2. Increased Security
Whether it is used to identify problems, protect against attacks, or optimize an environment - network log records play an essential part. With an efficient management system to control them, however, maintaining security for infrastructure and data becomes much more accessible.
Centralized Logging offers a solution by enabling you to view all your logs from one central location. This gives a comprehensive picture of your environment so that potential threats can be identified quickly, while centralization logging makes meeting regulatory compliance and security requirements much more straightforward.
Logs generated from multi-tier systems often exceed the storage capacity, threaten system file integrity and disrupt application performance. A centralized logging solution can filter out noise while providing protocols to respond to unapproved changes and alert admins of specific patterns within log data.
Modern centralized logging platforms utilize machine learning to enrich and correlate logged events, allowing engineers to detect significant trends or anomalies that may otherwise go undetected. This lets engineers quickly determine whether performance issues are isolated or part of a more significant trend, such as increased error rates across an application or customer journeys that slow down over time.
3. Improved Performance
Modern applications generate log data that provides engineers with a wealth of information regarding what is going on, sources of errors, security practices, and user journey trends. If engineers cannot quickly and easily access this information, it could lead to production incidents or interrupted customer journeys; an efficient centralized log management solution should provide real-time monitoring so the right people can see any issues as they happen and act faster to resolve them.
Moreover, having a centralized logging platform speeds up the time required to find relevant error logs when something goes wrong since users don't need to sift through multiple machines or locations in search of relevant logs; instead, this platform works around network interruptions and bandwidth restrictions to provide quick results.
A centralized log management system must first process the collected log data to achieve this goal. This includes parsing logs and enriching them with additional information (like converting timestamps into an acceptable format), filtering out unnecessary records, and compressing them for efficient storage.
Once processed events have been stored; they can be indexed for easier searching and analysis - similar to how full-text searches or database indexes speed up search processes and optimize performance.
Indexing also facilitates easier log consolidation from disparate systems for an overall picture of what's occurring, helping engineers quickly spot and resolve any potential problems, troubleshoot issues, meet compliance requirements and increase the performance of applications - particularly critical given the increasingly sophisticated nature of cybersecurity threats.
4. Increased Visibility
Engineers need the ability to troubleshoot quickly when an issue arises in production, which requires quick access to relevant logs. Logs also allow engineers to keep an eye on any upticks in error rates or sudden increases in infrastructure resource consumption that arise, but finding these logs can be time-consuming; for example, if the team's logs are spread across machines and servers, it could take hours just to identify one log for an issue that needs troubleshooting; without centralization, it would also be impossible to see trends as real-time or compare current data with historical baselines.
Centralized logging solutions help teams tackle problems more quickly by collecting, shipping, and storing logs in one central place. Engineers can more easily access the log data they require while being freed from depending on individual machines or servers, which could potentially become unstable and limit access to critical information.
Centralized Logging can also help improve the signal-to-noise ratio, an issue that can become challenging in distributed environments due to the signal being obscured by irrelevant data.Engineers benefit greatly from centralizing Logging as it makes finding relevant logs more straightforward and ensures that only recent ones are used for troubleshooting purposes - an especially essential feature when working with distributed applications that span multiple servers and host computers.
SolarWinds Security Event Manager (SEM) allows you to collect and analyze logs from workstations, servers, network devices, IDS/IPS firewalls, authentication services, and other sources to address issues quickly. It provides a centralized event log management platform that automatically collects, filters, normalizes, and archives data from all your devices. It offers high-compression data models that reduce storage costs while scaling to meet your needs without additional hardware purchases.
5. Increased Efficiency
Centralized Logging is an integral component of adequate security controls via SIEM and SOAR, enabling systems administrators to analyze patterns, anomalies, and issues across their system in an organized fashion. Furthermore, centralizing logs allows you to create reports and dashboards to monitor system performance and inform administrators when significant shifts in performance occur.
As well as centralizing and analyzing aggregated logs, a centralized log management platform must also be set up with policies to ensure logs don't grow too large, rotate properly, or delete to avoid data loss and allow real-time monitoring so any issues can be addressed promptly.
As an organization that produces large volumes of logs will know, having an efficient centralized logging solution is of the utmost importance. Collecting logs manually and then analyzing them can be tedious, mainly if they're spread across various locations. A centralized log management system helps reduce these manual tasks significantly and increase IT engineers' and developers' efficiencies, leading to increased efficiency as a result of reduced manual activities; furthermore, it ensures all team members can see end-to-end visibility into the software delivery pipeline and can troubleshoot issues quickly thereby decreasing MTTD/MTTR rates which ultimately leads to happier customers.