Have you ever wondered, what does SQL stand for and why it matters so much in technology, business,...

Have you ever tried to reset your PC only to be halted by encrypted files or a forgotten BitLocker...

It happens to all of us—you connect to WiFi once and never have to think about the password...

Have you ever wondered what is XML and why it still plays such a big role in technology today?...

If you’ve ever wondered, “What web hosting services do I need for my...

Have you ever tried to connect a new device and realized you’ve forgotten the WiFi password?...

When most people think of cyber threats, they picture malicious code, viruses, or ransomware. But...

In a world where digital communication dominates, verifying who or what is on the other end of a...

1. Executive Summary Endpoint protection — also referred to as endpoint security — is a...
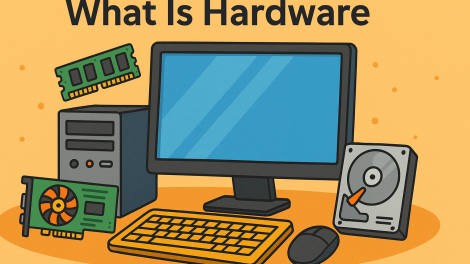
Have you ever wondered what really makes your devices tick? Behind every click, tap, or swipe is a...