Have you ever wondered, what does SQL stand for and why it matters so much in technology, business,...

Violating acts of cybercriminals happens right about exploiting smartly identified vulnerabilities....

Running an online business is not only about service offerings and profit earning, as there are...

Ever thought about having effective and powerful digital security? If you are part of a successful...

Every year there are predictions about losing billions to trillions of dollars; hence, aren’t...

Unstoppable cyber-attacks have always been disastrous. As a matter of fact, cyber attackers don’t...

The tech security support offering and people helping elements of cybersecurity services never end....

Cybersecurity involves various services for companies to be free from their daily challenges of...
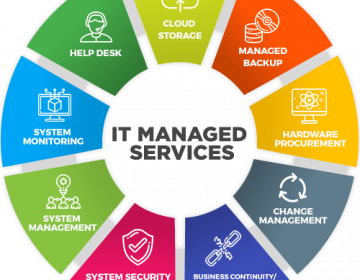
Updating technologies means embracing change. In the age of AI (artificial intelligence) and ML...

The embrace of digitalization has brought some of the greatest tech inventions. Hence, we can’t...