In a world where security breaches and theft are a growing concern, surveillance systems are no...

Ever paused and asked yourself, “What is WiFi?” Though we use it daily to stream, browse, and...
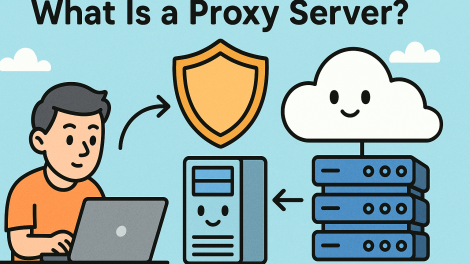
What is a proxy server, and how can it enhance your online security? In today’s digital...

If you ask cybersecurity experts about companies availing entry level computer security, then they...

Malware payloads have various network troubling and systems exploiting variants and today’s...

Locating the open vulnerabilities can’t be as easy as pie all the time. And when powerful...

Ever thought about having effective and powerful digital security? If you are part of a successful...

Network Access Control Definition Network access control (NAC) refers to a method that helps in...