Endpoint Detection & Response (EDR)
Our advanced EDR technology provides real-time threat detection, automated response, and comprehensive visibility into your endpoint activities. Ensure the security of your critical data and IT infrastructure with Xcitium’s robust EDR platform, designed to identify and neutralize sophisticated attacks before they cause harm.
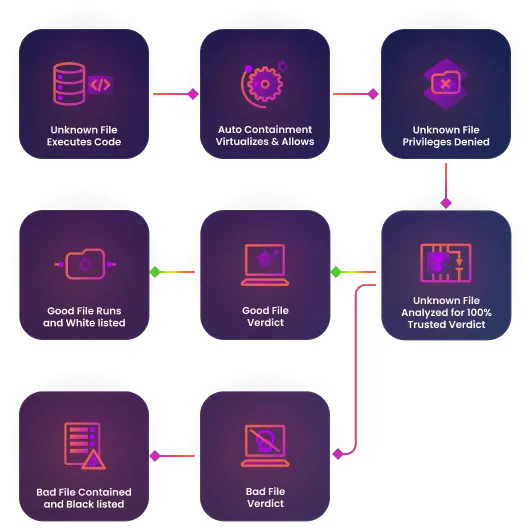
How It Works
Containing threats before they cause harm is crucial for maintaining security and business continuity. Xcitium's Auto Containment solution offers a robust defense mechanism by isolating potential threats in real-time. Our platform ensures that malware and other malicious activities are contained, preventing them from affecting your systems and data while allowing your operations to continue seamlessly.
Request DemoKey Features

Advanced Threat Detection
Utilize machine learning and behavioral analysis to detect known and unknown threats. Identify sophisticated attacks, including fileless malware and zero-day exploits.

Real-Time Monitoring
Xcitium provides continuous visibility into endpoint activities. Monitor system behaviors and network traffic for early threat detection.

Automated Incident Response
Automated threat investigation and response processes. Reduce the time to detect and respond to security incidents.

Forensic Analysis
Xcitium collects and analyzes endpoint data for in-depth forensic investigations. This analysis helps trace the origin and impact of security breaches.

Threat Intelligence Integration
Xcitium’s EDR integrates with global threat intelligence feeds for up-to-date threat information. This integration enhances detection accuracy and response effectiveness.

Big Data VirusScope Analysis System
VirusScope, a part of Xcitium Security products, is a dynamic application analyzer system that detects malicious behavior of a file, blocks and reverses those actions when necessary. The detected malware are reported to Xcitium servers and this data is also used by Verdict.
Benefits
Solution
Why Choose Xcitium?
Xcitium is a leader in cybersecurity, offering innovative solutions to protect against the most advanced threats. Our endpoint security platform combines cutting-edge technology with expert support, ensuring your business stays secure in a constantly evolving threat landscape. Trust Xcitium to safeguard your endpoints and protect your business.





