Web Protection
Protect your organization with Xcitium Web Protection, a cloud-based web filtering solution that provides complete protection from online threats such as viruses, malware, ransomware, and phishing. It is a low-maintenance, comprehensive content filtering solution that can be set up in five minutes to stop users from accessing inappropriate online content.
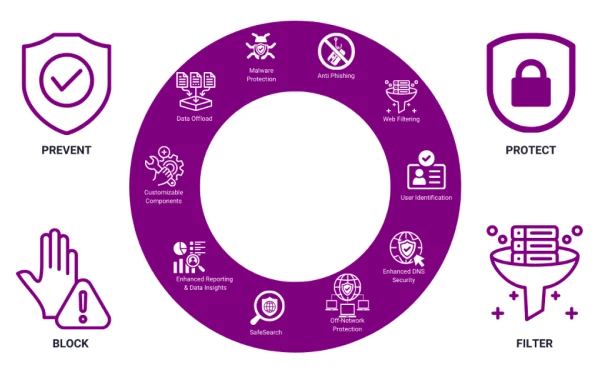
How It Works
All incoming and outgoing web traffic is routed through Xcitium Web Protection, where it undergoes thorough inspection. Xcitium Web Protection will allow or deny access to sites based on your safe lists and block lists and criteria such as URL, keyword, or rating. Through machine learning, artificial intelligence quickly learns which sites contain undesirable content, making it a much more effective and user-friendly experience.
Key Features
Web Filtering
Extensive and flexible filtering options including:
- Comprehensive set of predefined threat categories
- The ability to create custom categories.
- AI-based classification engine
- Coverage for more than 99% of the ActiveWeb
- Roaming agent
Easy-to-Use
Flexible and easy to deploy, manage, and use across the most common use cases. Supports off-network filtering and policy implementation for Windows, Mac, and Chromebook devices.
- 100% cloud-based; no software installation required
- Only requires a simple DNS redirect to a cloud server
- Flexible deployment options: SaaS, dedicated infrastructure, and roaming agents for off-network protection
- Easy navigation between customer accounts
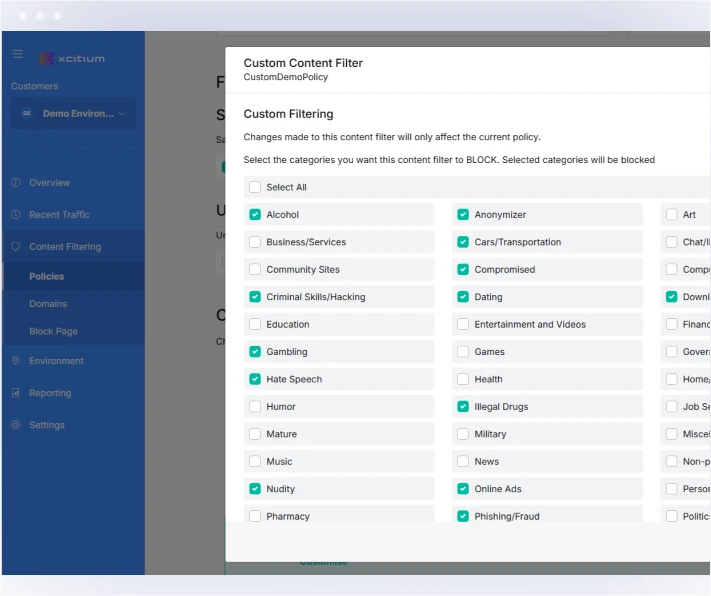
Policies
Filtering is controlled by policies including:
- By user, user group, location, and device
- Customizable and default policies
- Safe search settings
- Policy can be applied based on Active Directory Groups
Reporting
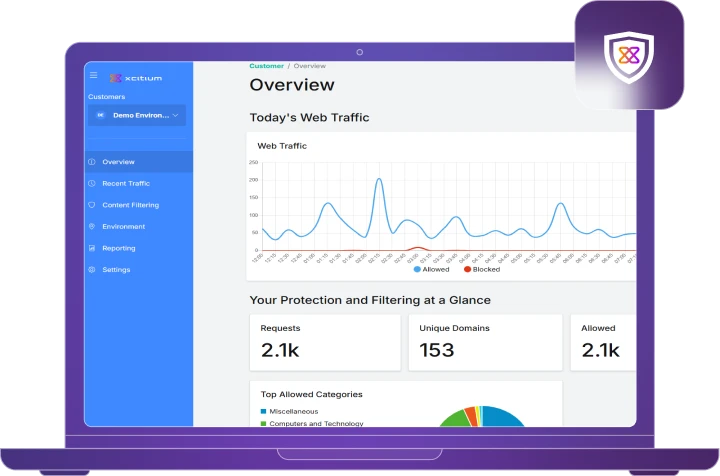
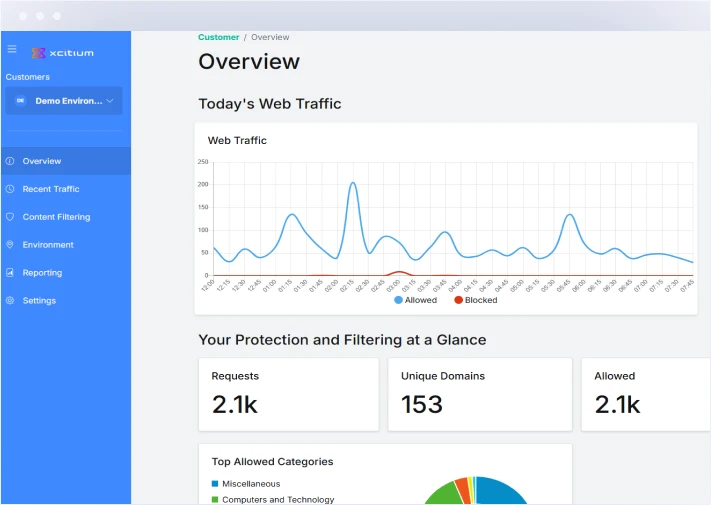
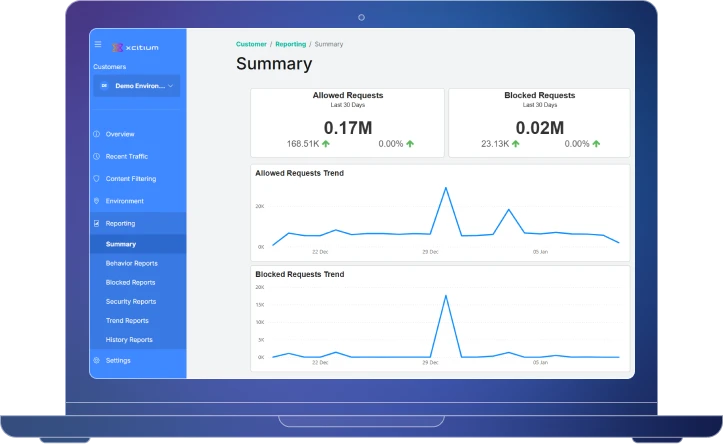
Enjoy maximum visibility into the Web Protection environment and its activities.
- Extensive set of predefined and customizable reports
- Real-time browsing view to assist with monitoring and troubleshooting.
- At-a-glance dashboard provides an overview of system performance and user activity
- Email notifications to inform of attempts to access a blocked category
- Scheduled reports
- Report export
- Supports Syslog
Extensive APIs
To optimize network performance, the gateway manages and prioritizes web traffic. Critical business applications receive the necessary bandwidth, while non-essential usage is limited, ensuring efficient use of network resources.

Benefits
Why Choose Xcitium for Web Protection?
Xcitium web protection is easy to deploy, manage, and use across the most common use cases. Supports off-network filtering and policy implementation for Windows, Mac, and Chromebook devices.





